漏洞文件: `download-add.php`
漏洞代码:
if( ! empty( $_POST['do'] ) ) {
check_admin_referer('wp-downloadmanager_add-file');
// Decide What To Do
switch( $_POST['do'] ) {
// Add File
case __('Add File', 'wp-downloadmanager'):
$file_type = ! empty( $_POST['file_type']) ? intval( $_POST['file_type'] ) : 0;
switch($file_type) {
case 0:
$file = ! empty( $_POST['file'] ) ? addslashes( wp_kses_post( trim( $_POST['file'] ) ) ) : '';
$file = download_rename_file($file_path, $file);
$file_size = filesize($file_path.$file);
break;
case 1:
if($_FILES['file_upload']['size'] > get_max_upload_size()) {
$text = '<p style="color: red;">'.sprintf(__('File Size Too Large. Maximum Size Is %s', 'wp-downloadmanager'), format_filesize(get_max_upload_size())).'</p>';
break;
} else
{
if(is_uploaded_file($_FILES['file_upload']['tmp_name']))
{
$file_upload_to = ! empty( $_POST['file_upload_to'] ) ? $_POST['file_upload_to'] : '';
if( $file_upload_to !== '/' ) {
$file_upload_to = $file_upload_to . '/';
}
if(move_uploaded_file($_FILES['file_upload']['tmp_name'], $file_path.$file_upload_to.basename($_FILES['file_upload']['name'])))
$file = $file_upload_to.basename($_FILES['file_upload']['name']);
$file = download_rename_file($file_path, $file);
$file_size = filesize($file_path.$file);
} else {
$text = '<p style="color: red;">'.__('Error In Uploading File', 'wp-downloadmanager').'</p>';
break;
}
} else
{
$text = '<p style="color: red;">'.__('Error In Uploading File', 'wp-downloadmanager').'</p>';
break;
}
}
break;
可以看到这里没有对我们的上传的文件进行检查,也没有随机命名文件名,且文件名的后缀是我们可控的,于是我们能够上传任意文件。
手工触发的方式:
进入: `/wp-admin/admin.php?page=wp-downloadmanager/download-add.php`, 选择 `uploadfile` 选项,
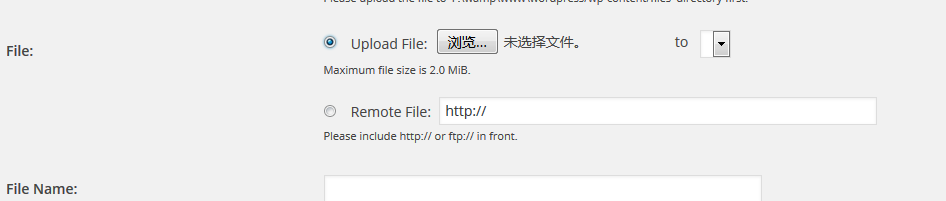
上传 `shell.php`,之后访问 `/wp-content/files/shell.php` ,即可。。。


暂无评论