### tl;dr
Gator Watch - a GPS watch for kids - is leaking data in all ends and anyone on the Internet can live track your kid. We're not talking about a security vulnerability, we're talking about non-existing security.
### Summary
Who: Gator Watch
Severity level: Critical
Reported: August 2017
Reception and handling: Poor
Status: Not fixed
Reward: A thank you
Issue: Anyone can track any watch, listen to voice messages, fake location, etc. etc.
### Background
I bought a Gator 2 smartwatch for my kid after reading some reviews about different watches. The concept was pretty good, but how good was the security?
The company behind Gator Watch claims to have sold more than 300,000 watches. As far as I can understand they are all trackable for anyone on the Internet.
I reported the issue in the start of August and was giving the vendor 90 days to fix the issues, so I was planning to publish this post in the start of November, but suddenly this case was all over the news.
The Gator watch is some places branded as Caref GPS Phone Watch. I'm not entirely sure if this is the same as the Gator 1 watch or if it's also Gator 2.
### Approach (technical stuff)
Looking back at this issue I really started in the wrong end. The biggest issues was so easy to spot without being very technical.
### Watch to server communication
Playing with the watch and the config I saw that it's possible to set up which server the watch connects to..
First I tried connecting to the Gator Watch server via telnet trying to send HTTP commands. That failed, and I tried a couple of other commands, but the remote server just closed the connection on me.
Then I set it up to my own router's IP address, added a port forwarding to my machine where I was running a very simple Python script printing whatever came my way. I configured the watch to use my IP, and surely it started sending simple strings with stuff like IMEI, positions, battery level, etc. It kept the connection open. The connection was not encrypted and there was no type of session ID or token or anything. It always used the IMEI as the identifier. This was pretty shocking.
The quick-and-dirty Python script I hacked together to listen to the watch:
```
#!/usr/bin/env python
import socket
TCP_IP = '0.0.0.0'
TCP_PORT = 17015
BUFFER_SIZE = 20
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.bind((TCP_IP, TCP_PORT))
s.listen(1)
conn = None
try:
conn, addr = s.accept()
print 'Connection address:', addr
while 1:
data = conn.recv(BUFFER_SIZE)
if not data: break
print "received data:", data
#conn.send(data) # echo
except KeyboardInterrupt:
print '\nBye bye :)'
finally:
if conn is not None:
conn.close()
if s is not None:
s.close()
```
I sent some of the commands I got to the Gator Watch server via telnet, and now it kept the connection open. This way one can easily spoof the position of anyone as long as you have the IMEI.
Here's some of the data received from our watch to my fake server (I've randomized the data and removed some newlines):
```
received data: (45353IMEIHERE416P02,GT03.V10.20170303,7,23201)
received data: (45353IMEIHERE416P02,G,160805A6027.0330N00512.3931E000.41058310.00,6)
received data: (45353IMEIHERE416P02,G,160805A6027.0352N00512.3879E001.411000074.23,6)
received data: (45353IMEIHERE416P02,0,1,160805,220200,5)
received data: (45353IMEIHERE416P02,0,1,160805,220200,5)
```
The data contains the software version, IMEI, time, location method (GPS vs Wi-Fi), location coordinates, battery left.
Sending the data to thet server you can get back who is allowed to call the watch. Like #555-2368#Dad. So that makes it pretty easy to identify the family of the child.
### HTTP proxy
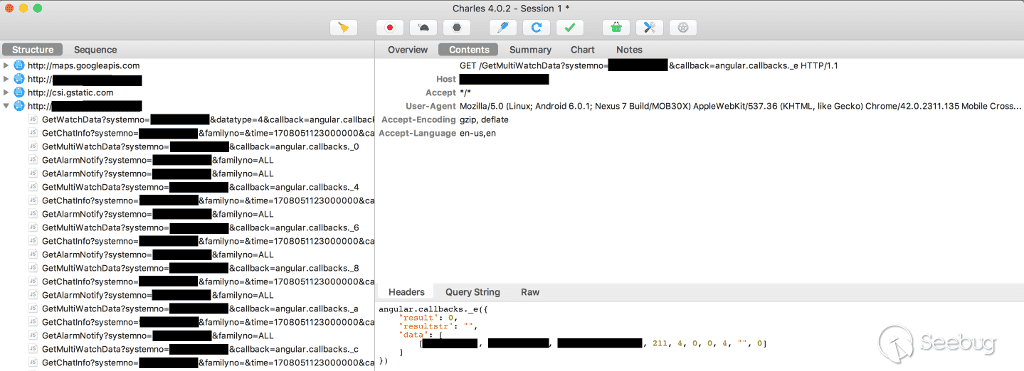
Using Charles to intercept the communication between Gator Android app and server.
[Just as in my first case](https://blog.roysolberg.com/2017/08/get-your-ssn-here) I set up Charles as HTTP+HTTPS proxy to listen to the communication between the Gator Watch server and Gator Watch app. I was shocked to see that there is no encryption between the server and the app.
What's more is that the app and server used an incremental integer as ID for the watch. I could - and still can - just change the ID and get the posisition of any other watch. And it didn't stop there. I could - and still can - easily download the voice messages left by any child or their parent. I changed the ID and got the position of a kid in Sweden. I only downloaded one other voice message, and it was appearantly from a Swedish parent sending some sort of first test message to his kid.
### Decompiling the app
I downloaded the APK for the Android app and decompiled it. It was an hybrid Angular app. Again, there was no signs of the app using https for anything. The JavaScript source code gave away addresses to other servers and I found a URL with a what looks like an admin interface.
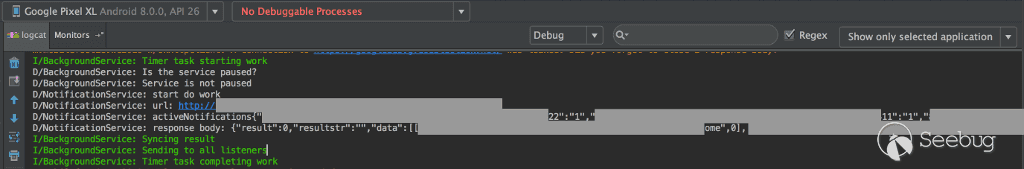
### Android system log
Being an Android developer I work most days with the phone's system log on the screen. What I didn't see until after I found out of everything, is that the Gator app actually constantly logs the URL which you can just open in your browser and change the integer ID in and get the position of any child wearing the watch.
### Security issues
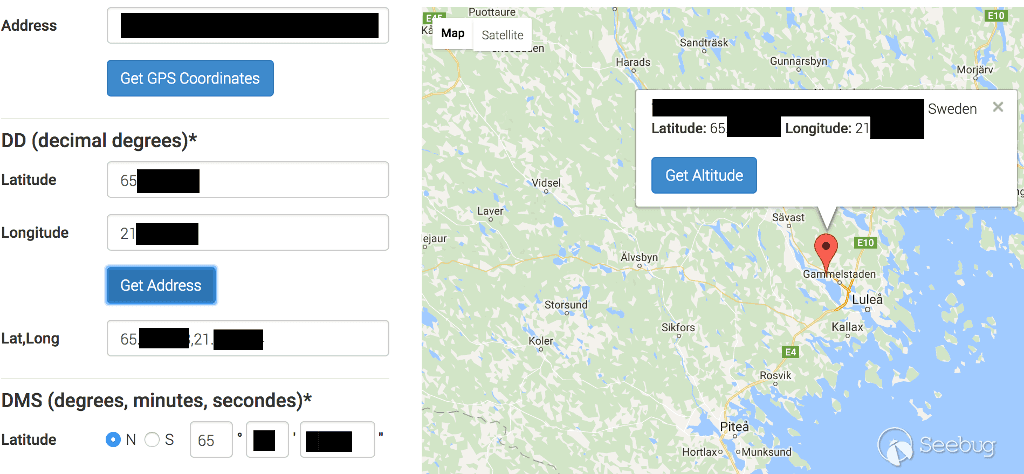
I got the location and voice messages of a random watch in Sweden. (Screenshot from gps-coordinates.net.)
The issues I saw were these:
- Anyone can easily track all Gator watches using a web browser
- Anyone can download any voice message left by child or grown-up
- Anyone can spoof the location of a watch
- Anyone can get hold of phone numbers and names that is allowed to call a watch
- There is no encryption between the app and the server
- There is no encryption between the watch and the server
### Reception and handling
#### Day zero
Saturday evening I sent an e-mail to customer support of Gator Norway explaining the issues.
#### Day 3
Tuesday morning I got a reply thanking me for sending them the information. They would check this out as soon as possible. And "We want our watch to be safe for both children and parents!"
#### Day 16
Without my knowledge [The Norwegian Consumer Council](https://www.forbrukerradet.no/) and security company [mnemonic](https://www.mnemonic.no/) started their own testing of different smartwatch brands sold in Norway - among them the Gator 2 watch.
#### Day 18
I asked for a status on the issue.
#### Day 39
They used 3 weeks to get back to me, and told that it "would take some time" to fix this. I can understand that adding security on a completely broken system isn't done very easily. They also said that the Gator 3 Watch and Gator 3 app is already secured.
#### Day 76
[The Norwegian Consumer Council suddenly broke the news about security issues in smartwatches for children](https://www.forbrukerradet.no/siste-nytt/elendig-sikkerhet-i-smartklokker-for-barn) (Norwegian article) - among them Gator Watch. BBC also brought the news. (English article) This is when I decided to write this post with the technical details and all. There was no reason to wait the normal 90 days when this is out. It's important that as many people as possible is told about this.
### Conclusion
If you ask me this is as bad as it can get. As a parent you want your kid to be nothing but safe. And when you buy a product like this you expect to make them more safe. But what happens is that you put your child at risk. Any predator can track your kid, and even start see patterns in when a child usually goes to e.g. school or after-school activities. It would even be possible to fake the position of the child, tricking parents to believe everything is fine or that their child is somewhere else than they are looking for him/her.
As a developer I just cannot understand how a product like this can end up on the market. Any developer involved in the project on any level would know that this is a really bad product. It's not like anyone mistakenly has screwed up. No one has cared to add any layer of security.
If your child is using Gator Watch I would recommend you stop him or her from doing that. Now.
For those of you wanting to go even deeper I would recommend the solid [report by Norwegian Consumer Council and mnemonic](https://fil.forbrukerradet.no/wp-content/uploads/2017/10/watchout-rapport-october-2017.pdf) (PDF, English, 49 pages). They also cover some other brands, go into more privacy issues and show how they did the technical tests.
### Update
[Read my follow-up on the Gator Watch](https://blog.roysolberg.com/2018/03/gator-watch-revisited) almost half a year later.


暂无评论