### Abstract
I found a new vulnerability in smart contract of IDXM Token (CVE-2018–10666)[1]. Attackers can acquire contract ownership because the setOwner function is delcared as public. A new owner can subsequently bypass intended access restrictions by, for example, calling uploadBalances.
### Details
In the following, I will explain more details about the vulnerability. Figure 1 shows the vulnerable setOnwer() function [2].
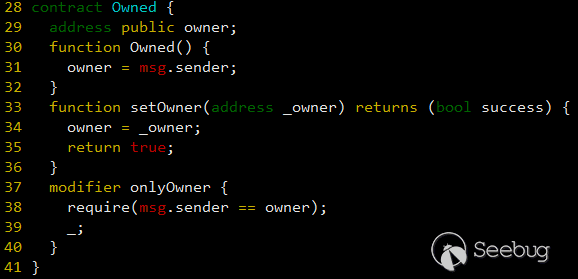
Figure 1. setOwner() function is delcared as public
In Solidity, there are four types of visibilities for functions: external, public, internal or private, where the default is public [3]. setOwner() function is declared without any visibility, so it is declared as public. It means that anybody can call it and change owner variable. So, an attacker can change the owner variable to his account address.
### What can attackers do?
There are important functions that should be called by only owner, such as uploadBalances, lockBalances, and so on. Those functions are protected by onlyOwner modifier which prevents calls from users who are not owner. An attacker can get the ownership of the contract using the vulnerability and then he can call any functions with owner authority. Therefore, he can call the functions declared with onlyOwner modifier.
### Exploit
To confirm this vulnerability, I sent a transaction invoking the setOwner function to change the owner as my account address.
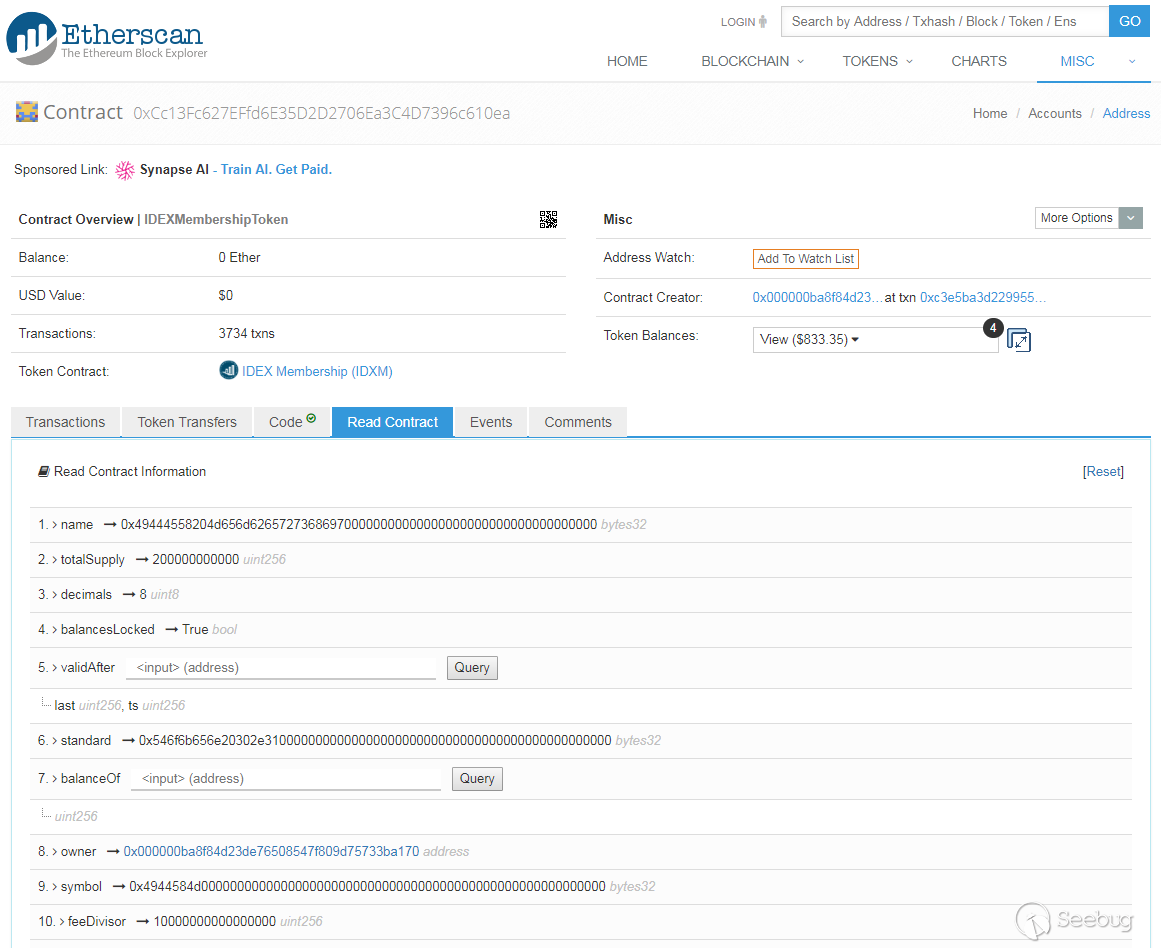
Figure 2. Before the exploit, the owner is ‘0x000000ba8f84d23de76508547f809d75733ba170’ which is same with contract creator
Figure 2 shows that the original state of the contract. The owner of the contract is same with the contract creator which is ‘0x000000ba8f84d23de76508547f809d75733ba170’. After my exploit, the owner is changed as my account address ‘0xa4afe8bc10c32e8e0ca9db6f982e4d9490045407’. Figure 3 shows the result.
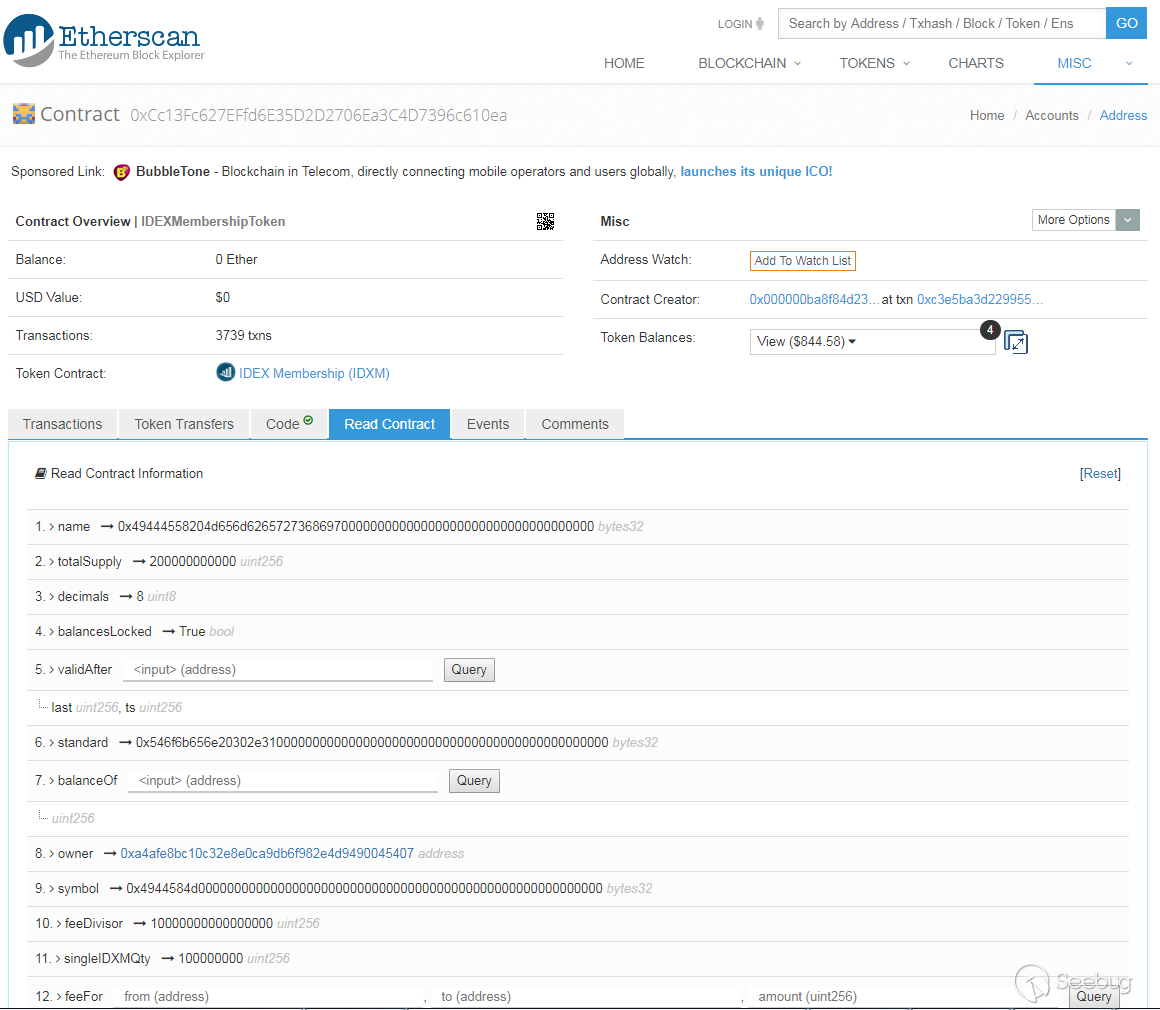
Figure 3. owner is changed as ‘0xa4afe8bc10c32e8e0ca9db6f982e4d9490045407’ after the exploit.
Figure 4 shows the [exploit transaction [4]](https://etherscan.io/tx/0xebf1137e7e9c0eb399dce6397309ef8e95bf3706f10340212be8082ae69c2f10).
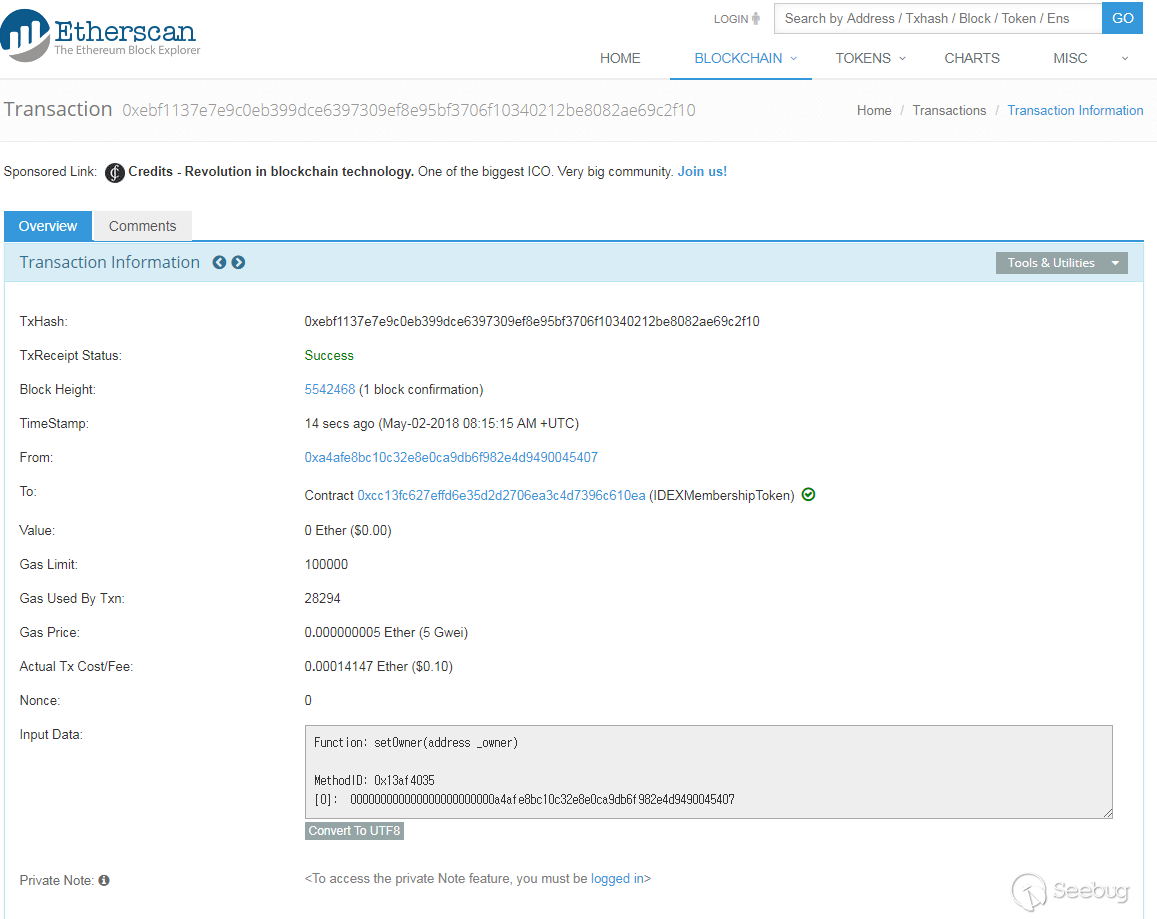
Figure 4. Exploit transaction
### Reports
When I found this vulnerability, I have immediately notified to Aurora which is admins of IDXM [5]. They said that it is a known bug and not critical. Actually, the attacker who gets ownership cannot do critical things such as manipulating user’s balances or destroying contract. The attacker can modify some important variables but admins can change it by getting owership again.
### Conclusion
Declaring visibilitiy of functions is very important. Developers must declare the visibilitiy although it is public function. When they implement a function, they should deeply consider who can or cannot call it. Fortunately, this vulnerability is not critical but many smart contract will danger if their ownership is changed by anyone.
### About me
I’m Jonghyuk Song who is a security researcher at Samsung Research. Recently, I’m intereted in Blockchain security, such as consensus protocol, smart contracts, sodlity and so on.


暂无评论