### Postauth RCE in latest NagiosXI
[Last time](https://code610.blogspot.com/2019/12/multiple-xss-bugs-in-nagios-569.html) I described few XSS bugs for latest Nagios (5.6.9). During the research and code review I found a possibility for RCE. Below you will find the details from the journey. Here we go...
We will ([again](https://code610.blogspot.com/2019/12/multiple-xss-bugs-in-nagios-569.html)) start here:
I used 'latest' available version - 5.6.9 - for VirtualBox, downloaded [here.](https://www.nagios.com/downloads/nagios-xi/vmware/)
As you (probably;)) [read/remember](https://code610.blogspot.com/2019/12/multiple-xss-bugs-in-nagios-569.html), in scheduled reporting we have a persistent XSS. [Sometimes](https://code610.blogspot.com/p/found.html) when I found a bug 'related to OWASP' (so for example: XSS) I'm trying to check the source code of webapp ('if available') to look for similar cases:

So, to see a bigger picture:
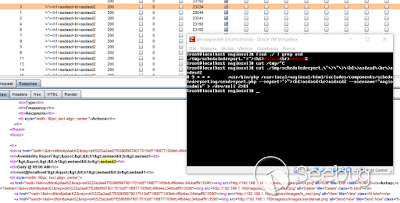
As you can see on the screen:
\- we can create file on server
\- we can inject some garbage on the filename (like '> or ">)
\- we are using php 'to run command'
Cool. My goal was to get RCE here. ;)
So the case was:
\- attacker (logged-in normal/registered user) will inject malicious payload in scheduler
\- scheduler will run attached code when using cron*
*(in source you will see that our injection is possible when script will do: rm -f <ourString>but we will get to that later;))
Checking again (and again...):
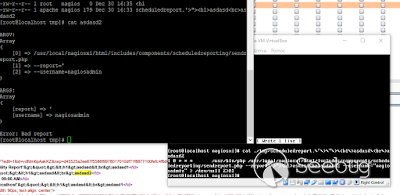
Still nothing. The case is: how to inject a string to cron-not-to-php? Hm... I (still) don't know yet.
I tried to use the same command (in other shell windows) as was the command injected to the (created) script. I was wondering, maybe I'll find the injection string this way...
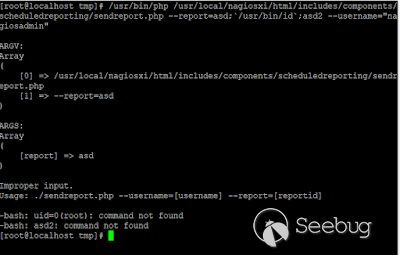
Still - nope.
So after a 'day with Nagios VM' we should be somewhere here, reading logs ;)
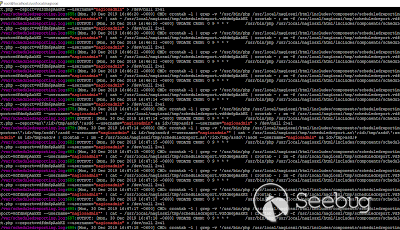
we are here again:
After few more times/requests I decided to check logs again... this time I found this:
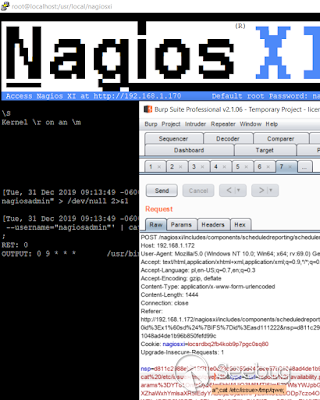
Well. Yes, /etc/issue is printed to the log file ;D
As you can see, payload should write file to /tmp/qwe. And in fact, it is true, but we are looking in wrong /tmp/ directory. ;) Check it out:
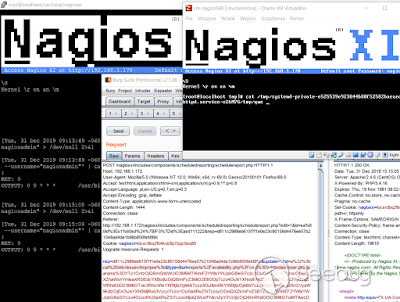
So no we should be somewhere here, verifying:
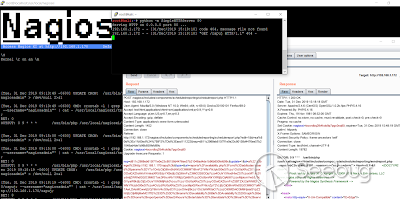
I used revshell from [pentestmonkey](http://pentestmonkey.net/tools/web-shells/php-reverse-shell) (thanks!):

Quick configuration and we should be here:
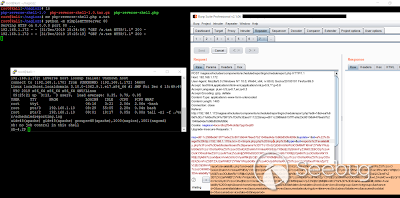


暂无评论