### - Unauthenticated RCE in Draytek Vigor 2960, 3900 and 300B (CVE-2020-8515)
DrayTek is a manufacturer of Firewalls, VPN Devices , Routers, WLAN devices,
etc, based in China.Investigating on different network devices I found that
there's a device model named Vigor 2960 (no, it's not a switch as the Cisco
one). The Draytek Vigor 2960 is a High-Performance Dual-Wan Load Balancing
Router & VPN Gateway.
[](https://images.seebug.org/1583429251016-w331s)
[](https://images.seebug.org/1583429254040-w331s)
When you try to authenticate, this device sends a POST request to
mainfunction.cgi with different parameters.
[](https://images.seebug.org/1583429256592-w331s)
[
](https://images.seebug.org/1583429260425-w331s)
[](https://www.blogger.com/blogger.g?blogID=3088897312176448925)[](https://www.blogger.com/blogger.g?blogID=3088897312176448925)[](https://www.blogger.com/blogger.g?blogID=3088897312176448925)[](https://www.blogger.com/blogger.g?blogID=3088897312176448925)[](https://www.blogger.com/blogger.g?blogID=3088897312176448925)[](https://www.blogger.com/blogger.g?blogID=3088897312176448925)[](https://www.blogger.com/blogger.g?blogID=3088897312176448925)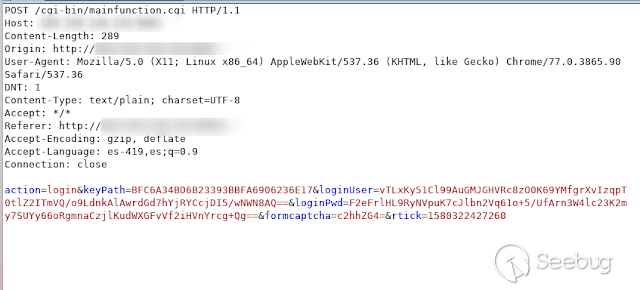
Now, what if we try adding in every parameter any escape character?, after a
few tries , trying to execute the pwd command, it was possible.
[](https://images.seebug.org/1583429272629-w331s)
After executing the command, I was thinking on how to escalate privileges, but
this was a surprise. After running the command id, i though that the answer
was going to be "www-data" or something related, but it was root!.
[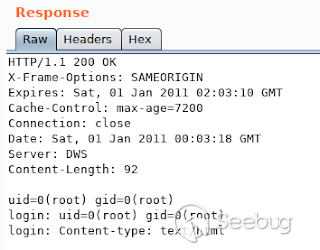](https://images.seebug.org/1583429274904-w331s)
Here are more example of differents commands executed.
ups! /etc/passwd ;)
[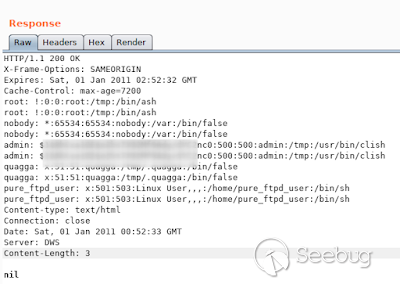](https://images.seebug.org/1583429277096-w331s)
Right now Im working on the reverse shell thing, because the commands executed
are being parsed by the mainfunction.cgi. Is a little bit tricky to get a
reverse shell with a command without spaces. Sed is replacing the spaces with
"+".
[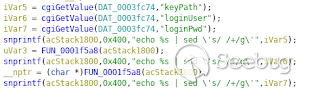](https://images.seebug.org/1583429280643-w331s)
But I'm concern of something more important than that. If you go to shodan.io
right now, and search for "Draytek" only, you'll find 710,029 hosts!.
[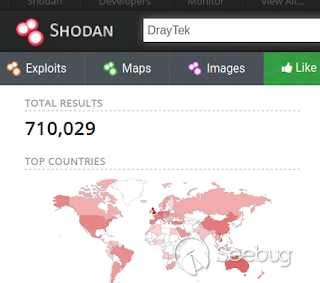](https://images.seebug.org/1583429282546-w331s)
If you search for the Vigor 2960 model, you'll have 15,429 host.
[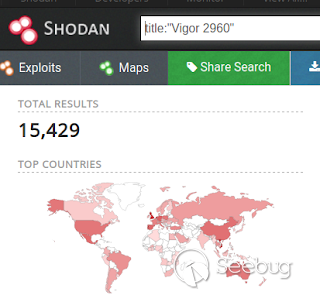](https://images.seebug.org/1583429286467-w331s)
All of this host are vulnerable?. Let's find out.
After a few hours I created a python script to check if a list of IPs is
vulnerable to this RCE. So, after exporting all the results for Vigor 2960,
and a few hours later, all the hosts were tested.
[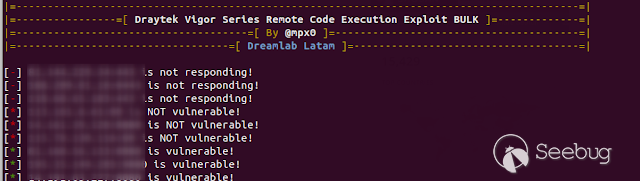](https://images.seebug.org/1583429289288-w331s)
[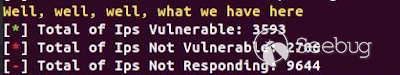](https://images.seebug.org/1583429292265-w331s)
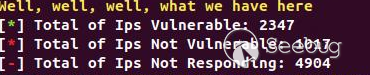
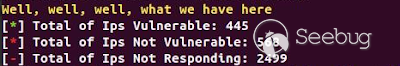
3593 are vulnerable!, and I'm 100% sure that the vulnerable hosts are more,
because of the timeout parameter configured in the requests.
**And that's not all! **
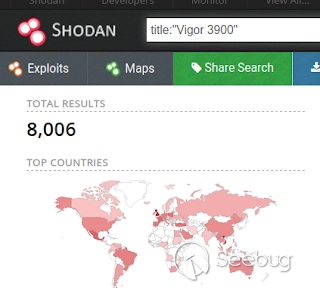
This vulnerability is fully compatible also for the DrayTek Vigor 3900 and
300B!.
_**Draytek Vigor 3900**_
_**
**_
[](https://images.seebug.org/1583429294561-w331s)
[
](https://images.seebug.org/1583429300467-w331s)
[
](https://images.seebug.org/1583429305179-w331s)
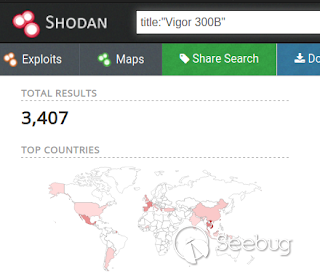
_**Draytek 300B**_
This device is not a VPN device as the others, this is a Loadbalancer.
[](https://images.seebug.org/1583429309722-w331s)
[](https://images.seebug.org/1583429312469-w331s)
[](https://images.seebug.org/1583429315712-w331s)
Until now, what version/firmware was detected as vulnerable?
- Vigor2960
- 1.3.1_Beta
- Vigor3900
- 1.4.4_Beta
- Vigor300B
- 1.4.2.1_Beta
- 1.4.4_Beta
- 1.3.3_Beta
CVE: CVE-2020-8515
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-8515
By @mpx0


暂无评论