https://sku11army.blogspot.com/2020/01/uhp-networks-multiple-reflected-xss-in.html
### Multiple Reflected XSS in UHP routers (CVE-2020-7235 - CVE-2020-7236)
**UHP Networks] Multiple Reflected XSS in UHP routers**
**** UHP Networks is a company dedicated to devolping, manufacturing and
marketing of VSAT satellite networking equipment. Its main products include
various UHP universal satellite routers, where the main application of these
devices is broadband, SCADA and multimedia connectivity in large VSAT networks
using HTS (High Throughput Satellite). ****
**
**
[
](https://images.seebug.org/1583428482724-w331s)
<http://www.uhp.net/products/routers/uhp-100/>
When searching for these devices in ZoomEye, I found several administration
panels of the UHP-100 device, which in most cases was accessible without the
need for credentials.
**
**
[
](https://images.seebug.org/1583428486533-w331s)
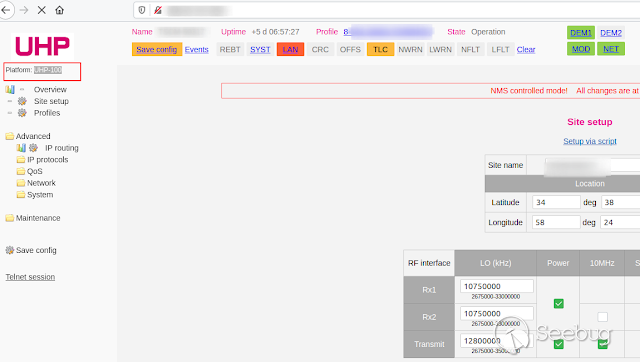
When accessing one of these devices, I noticed that it was possible to change
any parameters of site, profiles, and network.
## Reflected XSS #1
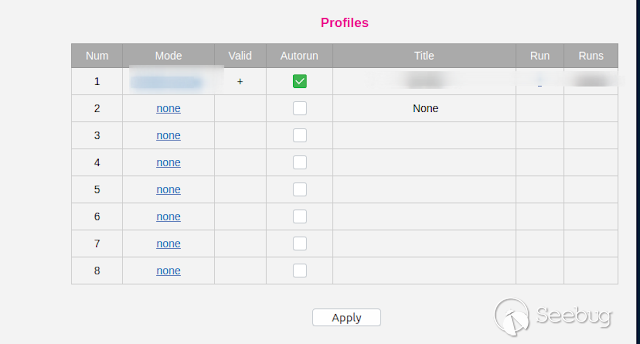
In the profiles section, the "Title" field caught my attention, which was the
only one where I could enter data. So, I decided to try simple HTML payloads
and javascript codes.
[](https://images.seebug.org/1583428502919-w331s)
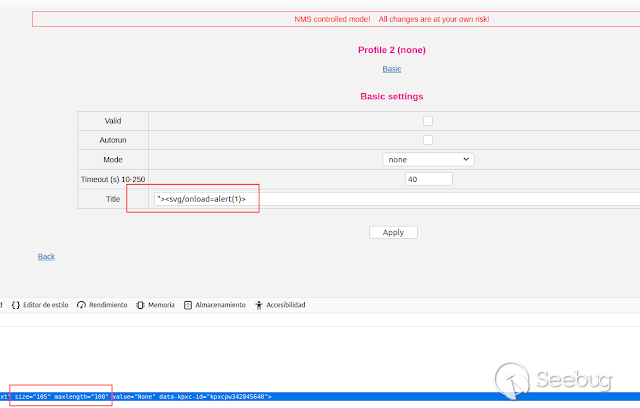
Before entering my payload in the field, I increased the maximum length, since
it was not possible to enter more than 10 characters.
[
](https://images.seebug.org/1583428505940-w331s)
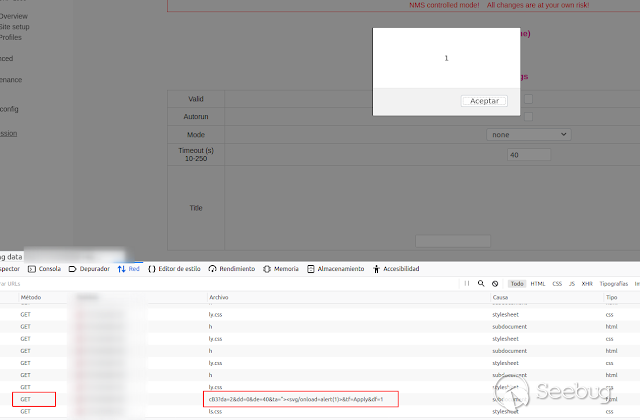
When the changes apply, the XSS was immediately triggered but I believed that
this would happen by entering the profiles tab where you can see the title of
all of them. Then, I reviewed the request that was sent, and I noticed that
the data was sent by GET method to "http: // [IP] / cB3" interpreting them
right there.
[](https://images.seebug.org/1583428523502-w331s)
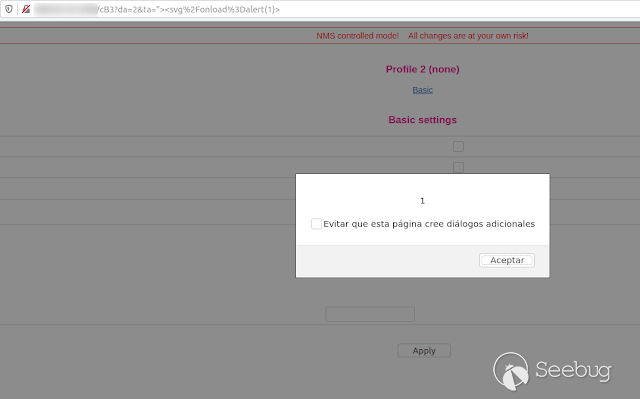
Then I decided to go directly to the page where the data is sent, but this
time I only used the "da" and "ta" parameters which correspond to the profile
number and title. At the time of entering with these parameters, the XSS was
once again successful.
[](https://images.seebug.org/1583428527377-w331s)
## Reflected XSS #2
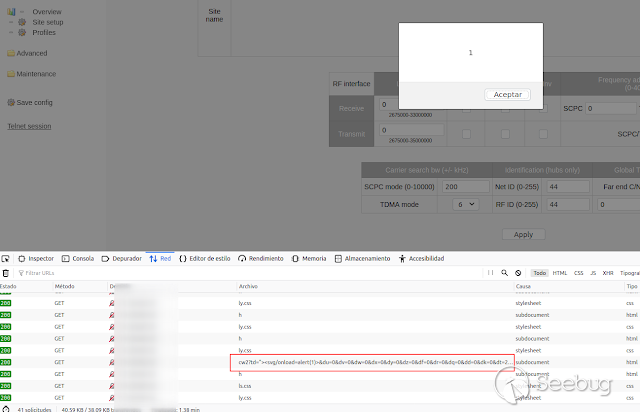
I tried the same thing in the "Site name" field of the "Site setup" section,
and the XSS was triggered as well.
[](https://images.seebug.org/1583428531143-w331s)
Using these simple URLs, we can determine if our UHP device is vulnerable:
• XSS 1: [http://[ IP
]/cw2?td=%22%3E%3Csvg%2Fonload%3Dalert(1)%3E](http://173.244.88.140/cw2?td=%22%3E%3Csvg%2Fonload%3Dalert\(1\)%3E)
• XSS 2: [http://[](https://www.blogger.com/null)[ IP
]/cB3?da=9&ta=%22%3E%3Csvg%2Fonload%3Dalert(1)%3E](http://200.43.161.200/cB3?da=9&ta=%22%3E%3Csvg%2Fonload%3Dalert\(1\)%3E)
Tested on:
Version **3.4.1.15 (03.10.2017)**
Version **3.4.2.4 (26.01.2018)**
Version **3.4.3 (18.07.2018)**
By [@s4mnez ](https://twitter.com/s4mnez)
**
**


暂无评论