### Westermo Source Code Disclousure in Router MRD-315 (CVE-2020-7227)
Westermo is a company that provides a full range of industrial data
communications solutions for demanding applications in the transport, water
and energy markets among others. It has its own line of network products and
one of these are the MRD Series.
Searching for interesting devices on shodan, I came across one of these
Westermo brand technologies that uses industrial routers for the different
operations that ICS products do
(https://www.westermo.com/products/routers/wireless-routers/mrd-315).
[](https://images.seebug.org/1583428597093-w331s)
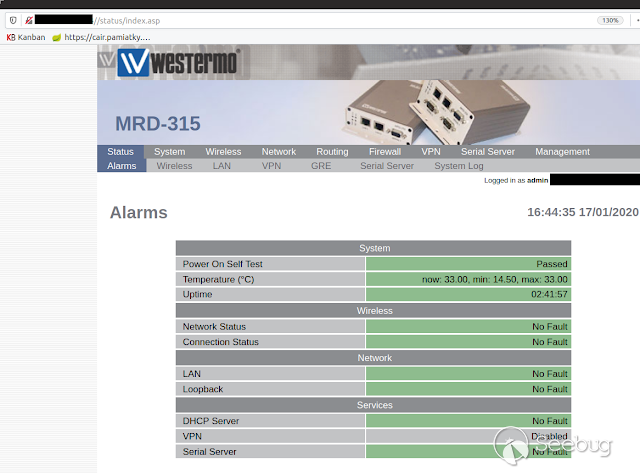
The device has a HTTP webpage on port 80, which allow us to enter the
administration panel with the correct credentials. In this sense, the manual
indicate us that the default credentials of these devices are admin:westermo,
so with a bit of luck, we can enter to these devices hosted on the internet.
[](https://1.bp.blogspot.com/-of1nSD1h8H0/XiMC-
WNxpEI/AAAAAAAAAKA/gBdEKdHEDigcr6MI-
XsWZzVyPfMXJ157wCLcBGAsYHQ/s1600/panel.png)
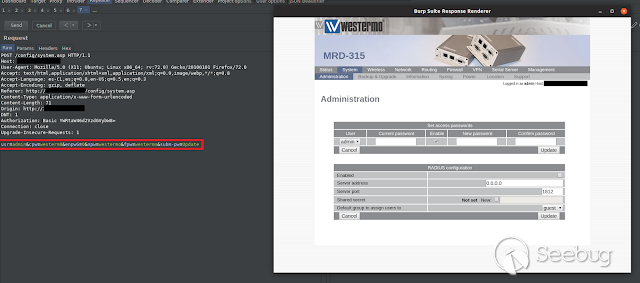
One of the first things I noticed on the web page is that the device uses
different URLs that end with the ASP extension, so the web page uses Visual
Basic Script or Jscript in order to works. Browsing some of the device's
functionalities, I began to capture some of the requests that were made in the
application frontend.
[](https://1.bp.blogspot.com/-T80vm_bd80c/XiMxs9pSblI/AAAAAAAAALc/jUIsgNoiFY8Fu8udnQVwYwMLlohdlcn6QCLcBGAsYHQ/s1600/changepwd.png)
In this case, I am trying to change the admin password and everything flows
normally, but, if we delete a mandatory field on the request (for example, the
"usr" parameter), the application crash and show us an error with all the
source code.
[](https://images.seebug.org/1583428607470-w331s)
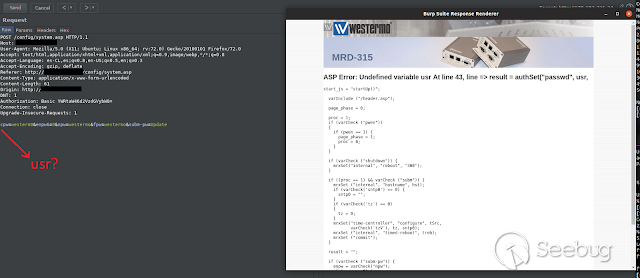
And here is, the source code for the system.asp file. Similarly, it is
possible to do this with other functionalities in order to get a huge part of
the application source code.
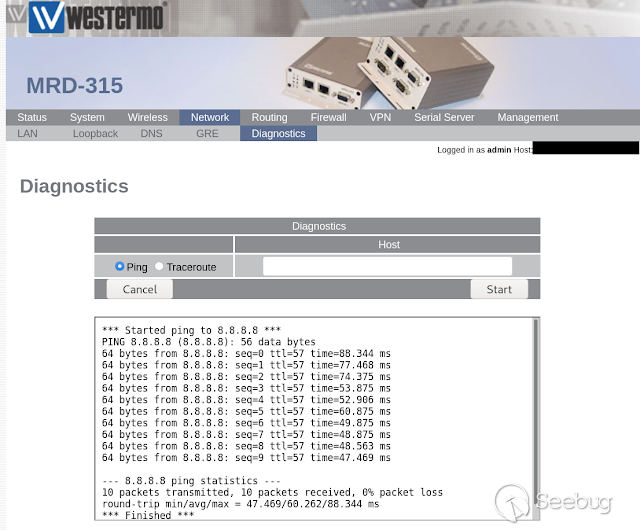
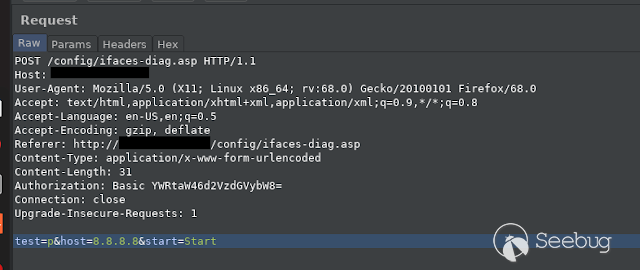
Let see another example. If we navigate to Network --> Diagnostics, we can
excecute a ping command in order to test the connection funcionality.
[](https://images.seebug.org/1583428611311-w331s)
[](https://images.seebug.org/1583428615117-w331s)
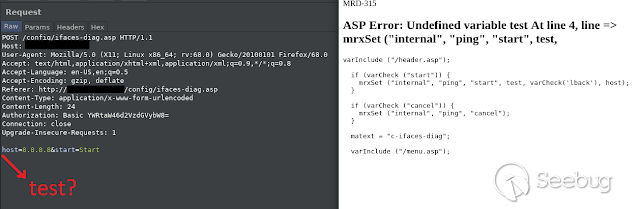
If we capture the request in the frontend, we can delete a mandatory parameter
and reveal the application source code.
[](https://1.bp.blogspot.com/-7D0O9r3blA0/XiMv748UtEI/AAAAAAAAALQ/3nznHi3pZ0ot8Y0nFxroX7b5XzVVJPzVgCLcBGAsYHQ/s1600/ping_vuln.PNG)
With some of patience, an attacker can reveal a huge mount of the source code,
in order to search for more vulnerabilities in the web application.
This was tested on MRD-315 Firmware v1.7.4.0 and v1.7.3.0
Saludos,
@h4tt0r1


暂无评论