### Authenticated Remote Code Execution in M302-L M302-LG M402-LG Industrial 4G LTE Cellular Router
[](https://images.seebug.org/1583460498092-w331s)
Proscend M302-L / M302-LG series are industrial-grade 4G LTE Cellular Routers
with 4-port 10/100 Mbps Ethernet interfaces for mission-critical cellular
communications. Featured with powerful network protocols and VPN tunnels,
M302-L / M302-LG series Industrial 4G LTE Cellular Routers provide secure and
reliable applications for mobile, M2M, and Industrial Internet of Things
(IIoT) deployments.
To fulfill the market demand, Proscend M302-L / M302-LG series Industrial 4G
LTE Cellular Routers are built with hardened industrial components, approving
severe HALT (Highly Accelerated Life Test) certification and wide operation
rage from -20 to 70°C for harsh environments. The M302-L / M302-LG series
provide Dual SIM redundancy for seamless wireless connectivity. The M302-LG
model is equipped with GPS function and displays accurate the routers position
for quickly managing existing devices. With the user-friendly interface, the
M302-L and the M302-LG enable fast and easy configuration to reduce
complicated settings.
Enhancing machine and machine communications efficiently for industrial
networking, Proscend M302-L / M302-LG series Industrial 4G LTE Cellular
Routers are highly suitable and cost-effective for your industrial solutions.
_\--www.proscend.com_
_
_**Authenticated RCE**
**
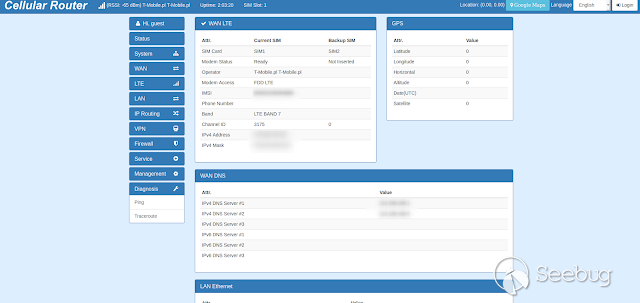
**When you first access to the device, you were land at the system status
page. I've noticed that at the bottom of the menu there is a Diagnosis section
with a ping feature
[](https://images.seebug.org/1583460501189-w331s)
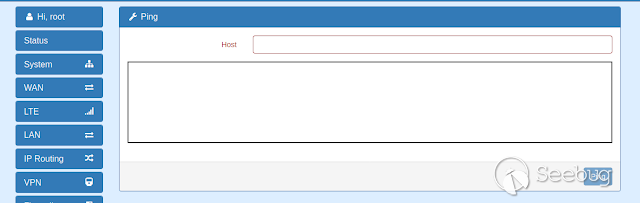
Before accesing the ping feature you must login, in this case with the default
credentials **root:2wsx#EDC**
**
**
Now we are at the ping page to test this feature against arbitrary code
execution
[](https://images.seebug.org/1583460503098-w331s)
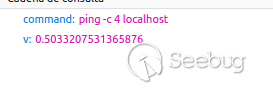
We first tried to ping to localhost to map the HTTP request
[](https://images.seebug.org/1583460507542-w331s)
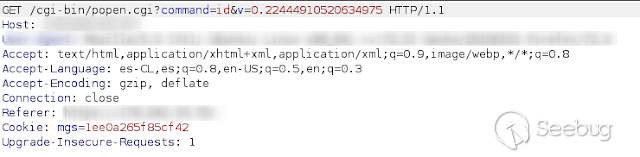
I took a closer look to the command parameter, and I noticed that the full
command is sent to the device, so I think there might be a chance to run any
other OS command I want. I tested with the **id** command and it worked
[](https://images.seebug.org/1583460519380-w331s)
[](https://images.seebug.org/1583460521639-w331s)
The vulnerable version discovered with this are:
- M302-L
- M302-LG
- M402-LG
[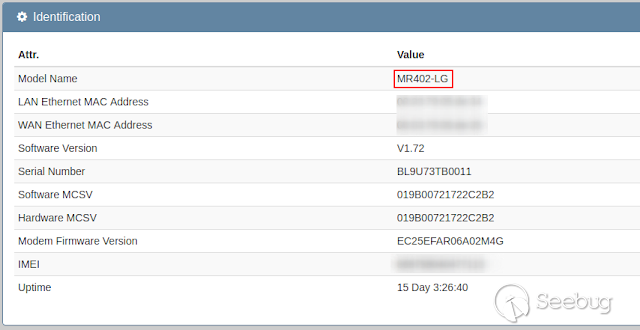](https://images.seebug.org/1583460523308-w331s)
[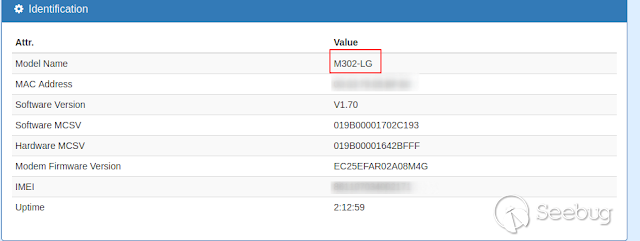](https://images.seebug.org/1583460525756-w331s)
I'm going to keep looking this vulnerability on other versions and updating
this post...
@xpl0ited1


暂无评论