**CVE-2020-27871: Directory Traversal leading to arbitrary file upload**
Orion allows the installation of various modules, with each module capable of
performing a specific network monitoring and management function. One such
module is the Network Configuration Manager (NCM) module. Where this module is
installed, there is an arbitrary file upload vulnerability that could be
leveraged for remote code execution. The root cause of this vulnerability is
illustrated in the following code snippet:
As shown, the NCM module has a firmware vulnerability management functionality
that downloads a ZIP file containing JSON files from an external website. By
default, it downloads from `https://nvd.nist.gov`, but this default can be
overridden. It then automatically extracts data from the .zip archive. It does
not check the file extensions of the extracted files, nor does it verify the
file upload path. Thus it is possible to upload the file anywhere in the file
system. Files are extracted and written in the context of SYSTEM.
This flaw can be easily exploited. For example, by issuing the following
request, it is possible to upload an arbitrary ASPX file to the www directory:
This vulnerability has one caveat in that it can only be exploited by an Admin
user. However, this requirement can be bypassed by the vulnerability we will
discuss next.
**ZDI-CAN-11903/ZDI-21-192: Privilege escalation**
[This](https://www.zerodayinitiative.com/advisories/ZDI-21-192/) vulnerability
is present when any of the following SolarWinds Orion platform modules are
installed:
\- Network Configuration Manager
\- Server Configuration Manager
\- IP Address Manager
When any one of these products are installed, SolarWinds stores account roles
in the `WebUserSettings` table.
View fullsize
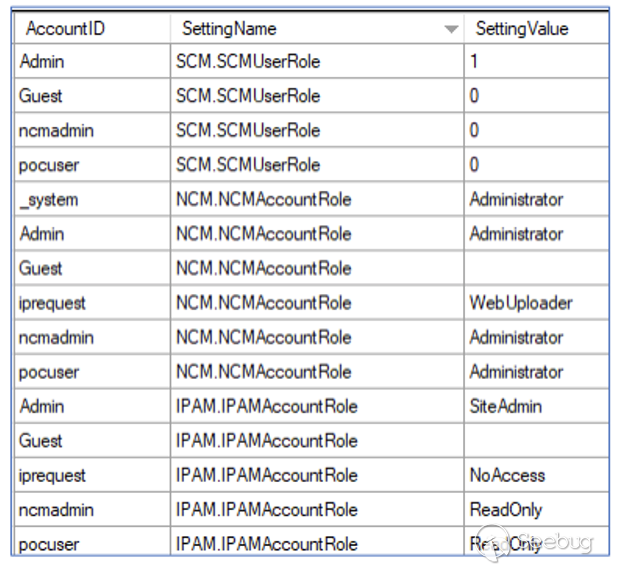!
The researcher discovered this table can be modified by a hidden
`SaveUserSetting` endpoint. A guest user can elevate their privileges to
Administrator by simply issuing the following request:
**Conclusion**
This series of blog posts shows that simple bugs and oversights can have
severe consequences. Luckily, SolarWinds has addressed all the above
vulnerabilities in [Orion Platform 2020.2.1
HF2](https://documentation.solarwinds.com/en/Success_Center/orionplatform/content/release_notes/orion_platform_2020-2-1_release_notes.htm).
We highly recommend those running a vulnerable version of this platform to
upgrade.
You can find me on Twitter at [@zebasquared](https://twitter.com/zebasquared),
and follow the [team](https://twitter.com/thezdi) for the latest in exploit
techniques and security patches.


暂无评论