CVE-2024-27497: Replace Your Linksys E2000 Router Now
=====================================================
BY [DO SON](https://securityonline.info/author/ddos/ "Posts by do son") · MARCH 4, 2024
A severe security hole (**CVE-2024-27497**) in the [Linksys E2000 router](https://www.linksys.com/support-product?sku=E2000) lets hackers waltz right into your network, potentially stealing sensitive data, compromising your devices, and using your connection for further malicious activity. Sadly, there’s no fix in sight.
How to Delete LastPass Account &...
Play
Unmute
Remaining Time \-9:57
Fullscreen
[How to Delete LastPass Account & Migrate to a New Password Manager (2023)](https://humix.com/redirect?url=https%3A%2F%2Feverybithelps.io%2Fhumix%2Fvideo%2FFnXns4tBWW2)
This vulnerability, [discovered](https://warp-desk-89d.notion.site/Linksys-E-2000-efcd532d8dcf4710a4af13fca131a5b8) in the [firmware version Ver.1.0.06 build 1](https://www.linksys.com/hk/support-article/?articleNum=148341) of the Linksys E2000 router, enables a bypass of authentication mechanisms, posing a significant threat to network security. The essence of this flaw lies within the position.js file, where the session\_key—a crucial piece of data intended to secure user sessions—is mishandled.
The flaw leverages the router’s mechanisms against itself. By exploiting the way session\_key values are retrieved and displayed within position.js, attackers can craftily obtain active session keys, effectively unlocking the door to the administration interface without needing the actual credentials.
The exploitation of this [vulnerability](https://securityonline.info/cve-2022-38555-linksys-e1200-buffer-overflow-vulnerability/) unfolds in a two-step process that’s chilling in its simplicity and potential impact. Initially, the attacker waits for the administrator to log into the router’s web management interface, a common enough occurrence in the maintenance of any network. This action generates a valid session ID string, ripe for the taking.
[
](https://go.ezodn.com/ads/charity/proxy?p_id=587d1eec-f2d3-4d49-5f1a-d6adb5ecb927&d_id=124533&imp_id=5099066796236228&c_id=1134&l_id=10016&url=https%3A%2F%2Fvillagebookbuilders.org%2Fdonate%2F&ffid=1&co=CN)
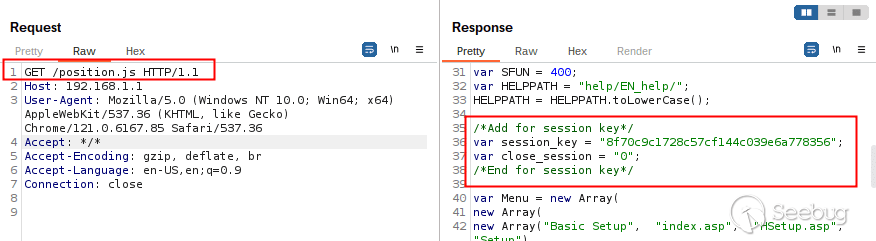
Image: notion.site
With the admin session active, the attacker then sends a specially crafted GET request to /position.js or any associated file that calls it, such as hset.htm, BlockSite.asp, BlockTime.asp, or getconnst.asp. This request is designed to leak the session ID, laying bare the supposedly secure session key.
Armed with this session ID, the attacker can bypass the login process entirely, gaining unauthorized access to the router’s admin interface. This level of access grants the attacker the ability to alter configurations, monitor network traffic, or deploy further malicious activities—all under the guise of a legitimate administrator.

Image: notion.site
What amplifies the severity of CVE-2024-27497 is the absence of an official fix. With no patch in sight, users of the affected routers are left in a precarious position, forced to seek alternative methods to safeguard their networks from potential exploitation.
In light of this [vulnerability](https://securityonline.info/cve-2017-17411-linksys-wvbr0-25-command-injection/), users and administrators of Linksys E2000 routers must take proactive measures to mitigate the risk of exploitation. This could involve monitoring network activity for unusual patterns, implementing additional authentication mechanisms, or isolating the management interface from general network access.
SHARE
[
](https://securityonline.info/cve-2024-27497-replace-your-linksys-e2000-router-now/#)
[
](https://securityonline.info/cve-2024-27497-replace-your-linksys-e2000-router-now/#)
[
](https://securityonline.info/cve-2024-27497-replace-your-linksys-e2000-router-now/#)
[
](https://securityonline.info/cve-2024-27497-replace-your-linksys-e2000-router-now/#)
[
](https://go.ezodn.com/ads/charity/proxy?p_id=587d1eec-f2d3-4d49-5f1a-d6adb5ecb927&d_id=124533&imp_id=4899044712212016&c_id=1149&l_id=10016&url=https%3A%2F%2Fwww.healthworksnewcastle.org.uk%2Fget-involved%2Fdonate%2F&ffid=1&co=CN)


暂无评论