Local Privilege Escalation via MSI installer in Palo Alto Networks GlobalProtect
================================================================================
Title
Local Privilege Escalation via MSI installer
Product
Palo Alto Networks GlobalProtect
Vulnerable Version
5.1.x, 5.2.x, 6.0.x, 6.1.x, <6.2.5, 6.3.x
Fixed Version
\>=6.2.5, all other versions are not patched yet
CVE Number
CVE-2024-9473
Impact
high
Homepage
[https://docs.paloaltonetworks.com/globalprotect](https://docs.paloaltonetworks.com/globalprotect "https://docs.paloaltonetworks.com/globalprotect")
Found
16.11.2023
By
Michael Baer (Office Fürth) | SEC Consult Vulnerability Lab
The MSI installer of GlobalProtect of Palo Alto Networks contains a privilege escalation vulnerability. This enables a local, low-privileged attacker with GUI access to a system, where GlobalProtect is installed via the MSI installer, to escalate the privileges to SYSTEM level.
Vendor description
------------------
_"GlobalProtect enables you to use Palo Alto Networks next-gen firewalls or Prisma Access to secure your mobile workforce."_
Source: [https://docs.paloaltonetworks.com/globalprotect](https://docs.paloaltonetworks.com/globalprotect)
Business recommendation
--------------------------
The vendor provides a patched version v6.2.5 which should be installed immediately. Further affected branches will be patched by the vendor in the future, except branch 5.2.x which is EOL. Users are urged to upgrade to the most recent versions.
SEC Consult highly recommends to perform a thorough security review of the product conducted by security professionals to identify and resolve potential further security issues.
Vulnerability overview/description
-------------------------------------
### 1) Local Privilege Escalation via MSI installer (CVE-2024-9473)
The configuration of the GlobalProtect MSI installer file was found to produce a visible conhost.exe window running as the SYSTEM user when using the repair function of msiexec.exe. This allows a local, low-privileged attacker to use a chain of actions, to open a fully functional cmd.exe with the privileges of the SYSTEM user.
Proof of concept
-------------------
### 1) Local Privilege Escalation via MSI installer (CVE-2024-9473)
For the exploit to work, GlobalProtect has to be installed via the MSI file. Afterwards, any low-privileged user can start the repair of GlobalProtect by double-clicking the installer and trigger the vulnerable actions without a UAC popup. The installer, if deleted from it's original location, can be found in C:\Windows\Installer with a randomized name.
During the repair process, the subprocess PanVCrediChecker.exe gets called with SYSTEM privileges and performs a read action on the file "C:\Program Files\Palo Alto Networks\GlobalProtect\libeay32.dll".
This can be used by an attacker by simply setting an oplock on the file. As soon as it gets read, the process is blocked until the lock is released. To do that, one can use the 'SetOpLock.exe' tool from "https://github.com/googleprojectzero/symboliclink-testing-tools" with the following parameters, see figure 1:
SetOpLock.exe "C:\Program Files\Palo Alto Networks\GlobalProtect\libeay32.dll" x
slide 1 of 1
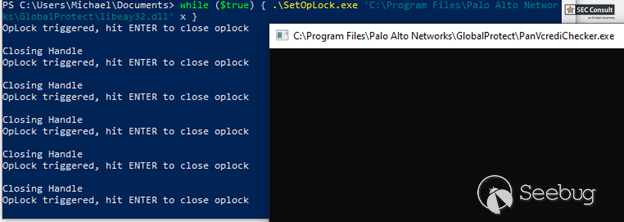
Figure 1: SetOpLock.exe execution
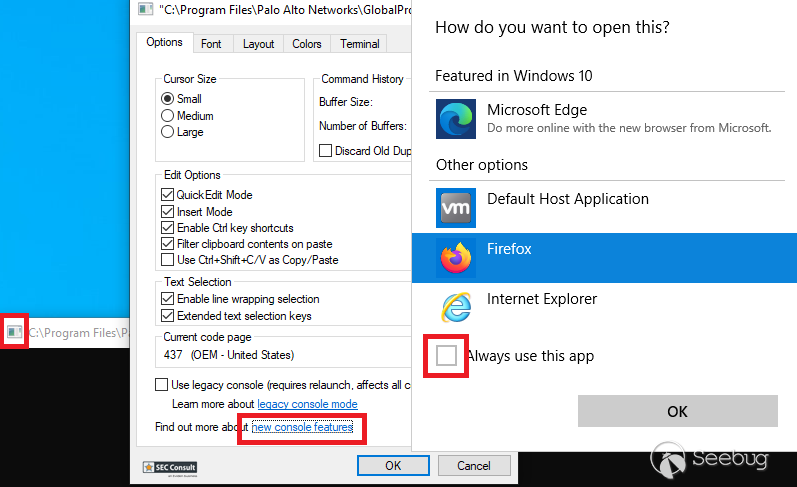
Figure 2: Open browser (untick "Always use this app")
During the repair process, the locked file is accessed several times. The lock has to be released by pressing ENTER five times before the conhost.exe window opens. For the sixth request, the lock should not be released to keep the window open. The conhost window that gets opened when PanVcrediChecker.exe is executed doesn't close and can then be interacted with.
The attacker can then perform the following actions to spawn a SYSTEM shell:
* Right click on the top bar of the window
* Click on properties \[see figure 2 below\]
* Under options, click on the "new console features" link \[see figure 2 below\]
* Open the link with e.g. firefox or chrome \[see figure 2 below\]
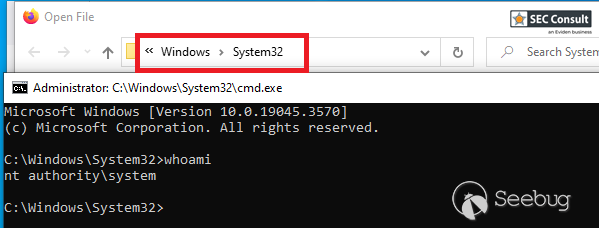
Figure 3: Execution of cmd.exe as SYSTEM
* In the opened browser window press the key combination CTRL+o
* Type cmd.exe in the top bar and press Enter \[see figure 3 below\]
Note that this does not work using a recent version of the Edge Browser.
Vulnerable / tested versions
----------------------------
The following versions have been tested which were the only versions available to SEC Consult at the time of the test. SEC Consult was not entirely sure, which exact version the product was:
* ProductVersion as stated by the PropertyTable: 5.2.10
* Version as stated by Windows after installing: 5.1.5
* 6.1.2 is affected as well
The vendor confirmed that versions <6.2.5 are affected. Furthermore, all other branches 5.1.x, 5.2.x, 6.0.x, 6.1.x and 6.3.x are affected as well. Branch 5.2.x is end of life according to the vendor and will not be patched.
Vendor contact timeline
-----------------------
2023-11-17
Contacting vendor through PSIRT@PaloAltoNetworks.com asking for most recent software version
2023-11-21
Vendor confirms receipt of contact
2023-11-23
Vendor denies providing most recent version and asks for full technical report via their online form: https://security.paloaltonetworks.com/report Note: Submitting the advisory draft via online form repeatedly results in server errors
2023-11-23
Sending the advisory via PSIRT@PaloAltoNetworks.com
2024-01-11
Contacting vendor through PSIRT@PaloAltoNetworks.com asking for confirmation of receiving the advisory and status of their triage.
2024-01-12
Vendor confirms receiving the advisory. The issue is tracked internally.
2024-03-06
Contacting vendor through PSIRT@PaloAltoNetworks.com asking for update of the vulnerability.
2024-04-02
The vendor notifies that the product team is working on the report.
2024-04-08
Asking vendor to notify about updates and the timeline of a fix.
2024-04-24
Vendor was able to reproduce the issue, but not in the most recent versions. 5.1.5 is affected, but not 5.2.10 nor 5.1.12, nor 6.2.2.
2024-05-23
Asking vendor about affected/fixed versions and regarding CVE number.
2024-05-30
Vendor apologizes for version confusion, following up with team internally. Vendor plans to publish an advisory with CVE, but no date yet, asks us to wait/coordinate our advisory with theirs.
2024-06-03
Answering that we will wait for their release & advisory.
2024-06-17
Asking for a status update regarding the version numbers & advisory release. Vendor: no ETA/timeline yet, no version information.
2024-09-25
Asking for a status update regarding the vendor advisory and for confirmation of the available fixes.
2024-09-27
Vendor investigated further and previous versions are unfortunately affected as well. Product team works on a fix, advisory & CVE release scheduled for 9th October 9 AM PT.
2024-09-27
Acknowledging the coordinated advisory release for 9th October.
2024-10-03
Vendor communicates further information regarding affected versions and their advisory draft.
2024-10-07
Vendor confirms 5.2.x as affected as well, but is EOL without fix.
2024-10-09
Coordinated release of security advisory.
Solution
--------
The vendor provides an updated version v6.2.5 which fixes the issues for this specific branch. Other versions are not yet patched and will be fixed in future releases.
Further information can be found at the vendor's website: [https://security.paloaltonetworks.com](https://security.paloaltonetworks.com/)
Users are urged to upgrade to the latest version and remove old versions of the MSI installer, especially users of v5.2.x as this branch is EOL and won't receive an update.
SEC Consult has also released a blog post on 12th September 2024 regarding MSI installer security issues tracked as CVE-2024-38014 and a general fix by Microsoft. We have contacted Microsoft to have a more general solution for every affected vendor. For further details check out the blog post: [https://r.sec-consult.com/msi](https://r.sec-consult.com/msi)
Workaround
-------------
None
Advisory URL
------------
[https://sec-consult.com/vulnerability-lab/](https://sec-consult.com/vulnerability-lab/)
EOF Michael Baer / @2024


暂无评论