4,000,000 WordPress Sites Using Really Simple Security Free and Pro Versions Affected by Critical Authentication Bypass Vulnerability
=====================================================================================================================================
**Introductory Note:** This is one of the more serious vulnerabilities that we have reported on in our 12 year history as a security provider for WordPress. This vulnerability affects **Really Simple Security, formerly known as Really Simple SSL**, installed on over 4 million websites, and allows an attacker to remotely gain full administrative access to a site running the plugin.
The vulnerability is scriptable, meaning that it can be turned into a large scale automated attack, targeting WordPress websites. The vendor worked with the WordPress plugins team to force-update all sites running this plugin before we published this post.
**You Can Help** by creating as much awareness around this issue in the community as possible, ensuring that any laggard and unmaintained sites update to the patched version. We encourage hosting providers to force-update their customers and perform scans on their hosting filesystems to ensure no customer is running an unpatched version of this plugin.
**It’s important to note that the Pro versions of this plugin are also affected by this vulnerability and sites running the premium versions should verify that they have automatically updated, so please do help get the word out. It appears that sites without a valid license may not have auto-updates functioning.**
The Details
-----------
On November 6th, 2024, our Wordfence Threat Intelligence team identified and began the responsible disclosure process for an Authentication Bypass vulnerability in the [Really Simple Security plugin](https://wordpress.org/plugins/really-simple-ssl/), and in the [Really Simple Security Pro and Pro Multisite plugins](https://really-simple-ssl.com/pro/), which are actively installed on more than 4,000,000 WordPress websites. The vulnerability makes it possible for an attacker to remotely gain access to any account on the site, including the administrator account, when the two-factor authentication feature is enabled.
[Wordfence Premium](https://www.wordfence.com/products/wordfence-premium/), [Wordfence Care](https://www.wordfence.com/products/wordfence-care/), and [Wordfence Response](https://www.wordfence.com/products/wordfence-response/) users received a firewall rule to protect against any exploits targeting this vulnerability on November 6, 2024. Sites using the free version of Wordfence will receive the same protection 30 days later on December 6, 2024.
We contacted the Really Simple Plugins team on November 6, 2024, and received a response on November 7, 2024. After providing full disclosure details, the developer released the patch for the Pro plugins on November 12, 2024, and for the Free plugin on November 14, 2024.
Due to the critical severity of this vulnerability (CVSS score 9.8 Critical), the plugin vendor worked with the WordPress.org plugins team to push a forced security update to the patched version, 9.1.2, for anyone running a vulnerable version of the plugin. This means most sites should already be patched or will be patched soon, however, we urge users to verify that their sites were updated to the latest patched version of Really Simple Security, version 9.1.2 at the time of this writing, as soon as possible if running version 9.0.0 or newer. A [thread in the WordPress.org](https://wordpress.org/support/topic/plugin-updating-automatically-with-auto-updates-disabled-3/) forum for the plugin indicates that the forced updates began this morning and may continue over the next few days.
Vulnerability Summary from Wordfence Intelligence
-------------------------------------------------
**Description:** [Really Simple Security (Free, Pro, and Pro Multisite) 9.0.0 – 9.1.1.1 – Authentication Bypass](https://www.wordfence.com/threat-intel/vulnerabilities/detail/really-simple-security-free-pro-and-pro-multisite-900-9111-authentication-bypass)
**Affected Plugins:** Really Simple Security, Really Simple Security Pro, Really Simple Security Pro Multisite
**Plugin Slugs:** [really-simple-ssl](https://wordpress.org/plugins/really-simple-ssl/), [really-simple-ssl-pro](https://really-simple-ssl.com/pro/), [really-simple-ssl-pro-multisite](https://really-simple-ssl.com/pro/)
**Affected Versions:** 9.0.0 – 9.1.1.1
**CVE ID:** [CVE-2024-10924](https://www.cve.org/CVERecord?id=CVE-2024-10924)
**CVSS Score:** 9.8 (Critical)
**CVSS Vector:** [CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H](https://www.first.org/cvss/calculator/3.1#CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H)
**Researcher/s:** István Márton (Wordfence)
**Fully Patched Version:** 9.1.2
The Really Simple Security (Free, Pro, and Pro Multisite) plugins for WordPress are vulnerable to authentication bypass in versions 9.0.0 to 9.1.1.1. This is due to improper user check error handling in the two-factor REST API actions with the ‘check\_login\_and\_get\_user’ function. This makes it possible for unauthenticated attackers to log in as any existing user on the site, such as an administrator, when the “Two-Factor Authentication” setting is enabled (disabled by default).
Technical Analysis
------------------
The Really Simple Security plugin, formerly known as Really Simple SSL, was recently renamed with the latest major version update and has been expanded with many security features like login protection, vulnerability detection, and two-factor authentication. Unfortunately, one of the features adding two-factor authentication was insecurely implemented making it possible for unauthenticated attackers to gain access to any user account, including an administrator account, with a simple request when two-factor authentication is enabled.
Examining the code reveals that the plugin uses the `skip_onboarding()` function in the `Rsssl_Two_Factor_On_Board_Api` class to handle authentication via REST API.
274
275
276
277
278
279
`public` `function` `skip_onboarding( WP_REST_Request` `$request` `): WP_REST_Response {`
`$parameters` `=` `new` `Rsssl_Request_Parameters(` `$request` `);`
`// As a double we check the user_id with the login nonce.`
`$user` `=` `$this``->check_login_and_get_user( (int)``$parameters``->user_id,` `$parameters``->login_nonce );`
`return` `$this``->authenticate_and_redirect(` `$parameters``->user_id,` `$parameters``->redirect_to );`
`}`
The `check_login_and_get_user()` function verifies the user using the `user_id` and `login_nonce` parameters.
65
66
67
68
69
70
71
72
73
74
75
76
77
`private` `function` `check_login_and_get_user( int` `$user_id``, string` `$login_nonce` `) {`
`if` `( ! Rsssl_Two_Fa_Authentication::verify_login_nonce(` `$user_id``,` `$login_nonce` `) ) {`
`return` `new` `WP_REST_Response(` `array``(` `'error'` `=>` `'Invalid login nonce'` `), 403 );`
`}`
`/**`
`* Get the user by the user ID.`
`*`
`* @var WP_User $user`
`*/`
`$user` `= get_user_by(` `'id'``,` `$user_id` `);`
`return` `$user``;`
`}`
The most significant problem and vulnerability is caused by the fact that the function returns a `WP_REST_Response` error in case of a failure, but this is not handled within the function. This means that even in the case of an invalid nonce, the function processing continues and invokes `authenticate_and_redirect()`, which authenticates the user based on the user id passed in the request, even when that user’s identity hasn’t been verified.
Ultimately, this makes it possible for threat actors to bypass authentication and gain access to arbitrary accounts on sites running a vulnerable version of the plugin. As always, authentication bypass vulnerabilities and resulting access to high privileged user accounts, make it easy for threat actors to completely compromise a vulnerable WordPress site and further infect it.
This vulnerability only critically affects site owners who have enabled “Two-Factor Authentication” in the plugin settings.
Wordfence Firewall Protection Mechanism
---------------------------------------
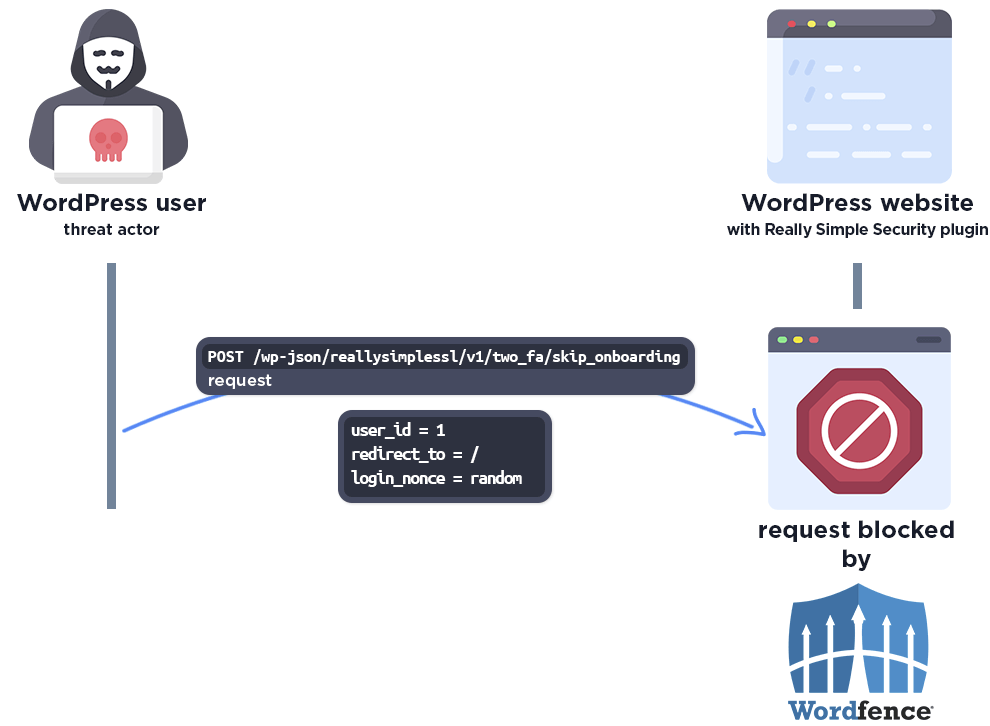
Wordfence has protected our Premium, Care and Response customers against this exploit **since November 6th, 2024**. The following graphic demonstrates how an attacker might exploit this vulnerability, and how the Wordfence firewall intercepts the malicious request and protects a site from exploitation by an attacker.
[](https://www.wordfence.com/wp-content/uploads/2024/11/really-simple-ssl-auth-bypass-howto-wordfence-firewall.png)
The Wordfence firewall rule detects the malicious REST API action and blocks the request.
Disclosure Timeline
-------------------
**November 6, 2024** – Wordfence Threat Intelligence team discovered the Authentication Bypass vulnerability in the Really Simple Security plugins.
**November 6, 2024** – [Wordfence Premium](https://www.wordfence.com/products/wordfence-premium/), [Care](https://www.wordfence.com/products/wordfence-care/), and [Response](https://www.wordfence.com/products/wordfence-response/) users received a firewall rule to provide protection against any exploits that may target this vulnerability.
**November 6, 2024** – We initiated contact with the plugin vendor asking them to confirm the inbox for handling the discussion.
**November 7, 2024** – We initiated contact again using the plugin vendor’s alternative email address.
**November 7, 2024** – The vendor confirmed the inbox for handling the discussion.
**November 7, 2024** – We sent over the full disclosure details to the vendor. The vendor acknowledged the report and began working on a fix. During this time, the vendor also co-ordinated with the plugins team to push this out as a security release.
**November 12, 2024** – The fully patched version of the Really Simple Security Pro plugins, 9.1.2, were released.
**November 13, 2024** – We informed the vendor that it is security best practice is to release the patched version as soon as possible along with a signal that a security issue was resolved.
**November 14, 2024** – The fully patched version of the Really Simple Security Free plugin, 9.1.2, was released and forced updates were initiated.
**December 6, 2024** – Wordfence Free users receive the same protection.
Conclusion
----------
In this blog post, we detailed an Authentication Bypass vulnerability within the Really Simple Security plugin and within the Really Simple Security Pro and Pro Multisite plugins affecting versions 9.0.0 through 9.1.1.1. This vulnerability allows threat actors to bypass authentication and gain access to the accounts of any user, including administrators. The vulnerability has been fully addressed in version 9.1.2 of the plugin.
We encourage WordPress users to verify that their sites are updated to the latest patched version of Really Simple Security as soon as possible, considering the critical nature of this vulnerability.
[Wordfence Premium](https://www.wordfence.com/products/wordfence-premium/), [Wordfence Care](https://www.wordfence.com/products/wordfence-care/), and [Wordfence Response](https://www.wordfence.com/products/wordfence-response/) users received a firewall rule to protect against any exploits targeting this vulnerability on November 6, 2024. Sites using the free version of Wordfence will receive the same protection 30 days later on December 6, 2024.
**If you know someone who uses these plugins on their site, we recommend sharing this advisory with them to ensure their site remains secure, as this vulnerability poses a significant risk.**
Search
### Trust Your Site
to the Leader in WordPress Security
Wordfence includes an endpoint firewall, malware scanner, robust login security features, live traffic views, and more. Discover why over 5 million WordPress sites put their trust in Wordfence.
[Protect Your Site](https://www.wordfence.com/products/pricing/)
**Did you enjoy this post? Share it!**


暂无评论