### Symmetricom SyncServer S100/S200/S250/S300/S350 - User Creation/Modification/Deletion - Not authenticated - (CVE-2020-9034)
[](https://images.seebug.org/1583429155277-w331s)
Lately I have been researching a lot about NTP servers and other rack
equipment that you commonly see in data centers. In a way, I have been
thinking about how critical these devices are generally and how little or no
security they have.
the SyncServer **S100/S200/S250/S300/S350** devices in their WEB application,
is not properly validating sessions in any of its functions ["Broken Access
Authentication"], which allows an unauthenticated remote attacker to access
critical functions of the application, such as the creation, modification or
elimination of users.
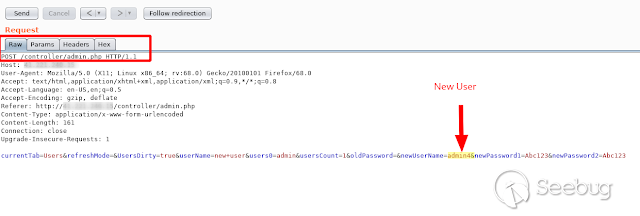
We go to the _**ADMIN Menu = > USERS => NEW USER**_. Once there, create any
user and capture the request.
Now we will create a new user without being authenticated in the application
[](https://images.seebug.org/1583429165881-w331s)
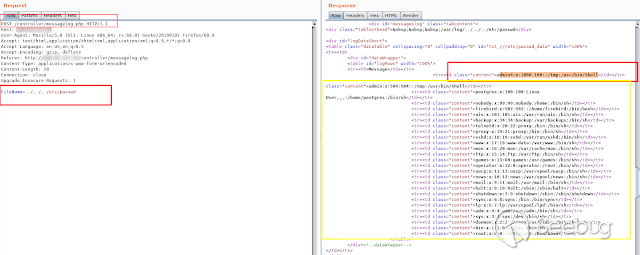
To verify that the new user exists, I will use the cross directory I found -
[here is the description](https://sku11army.blogspot.com/2020/01/symmetricom-
syncserver.html)-
[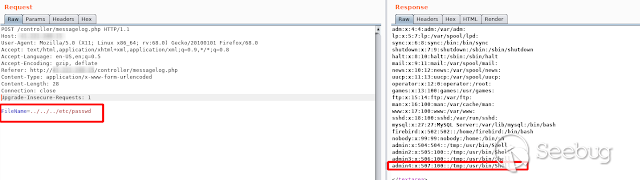](https://images.seebug.org/1583429169395-w331s)
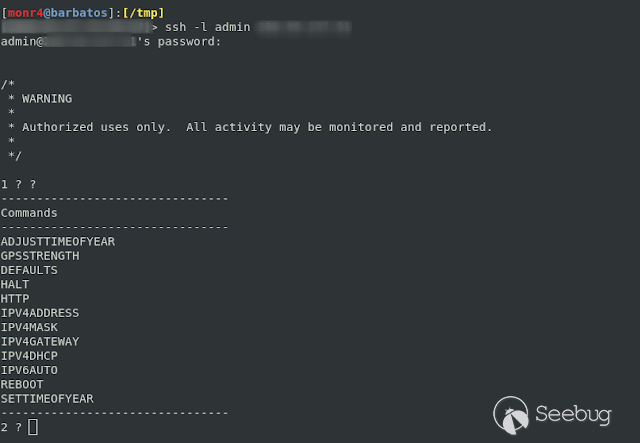
Now we test it on an S300 models
[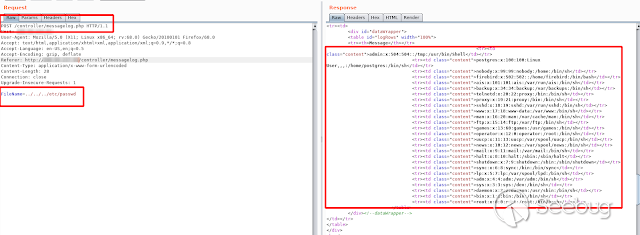](https://images.seebug.org/1583429172658-w331s)
[](https://images.seebug.org/1583429175258-w331s)
[](https://images.seebug.org/1583429177869-w331s)
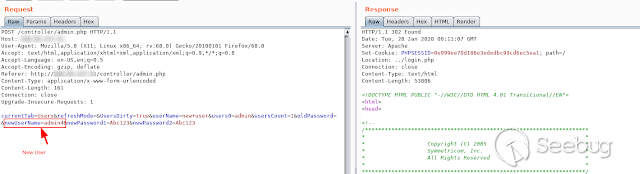
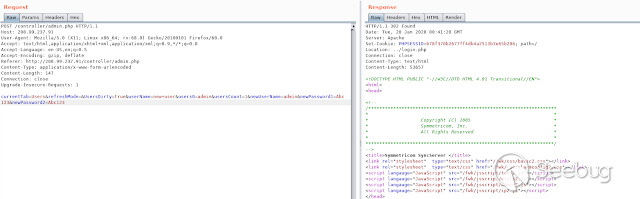
In addition, we can use the same request to change the account of an existing
user and make an " ** _ACCOUNT TAKE OVER_** "
[](https://images.seebug.org/1583429182438-w331s)
[](https://images.seebug.org/1583429185047-w331s)
**
****Affected Versions:**
- **SyncServer S100 - ****2.90.70.3 Build 2.90.70.3 **
- ****SyncServer S200 - 1.** 30**
- **SyncServer S250** ** \- 1.25**
- **SyncServer S300 - ****2.65.0 Build 2.65.0 **
- **SyncServer S350 - 2.80.1 Build 2.80.1**
CVE-2020-9034
**By: @Linuxmonr4**


暂无评论