### Symmetricom SyncServer S100/S200/S250/S300/S350 - Stored XSS - Not authenticated - (CVE-2020-9028)
[](https://images.seebug.org/1583459807099-w331s)
SyncServer _**S100/S200/S250/S300/S350**_ devices in their WEB application,
are not properly sanitizing the entry of user, so it presents a stored XSS
vulnerability, specifically in the " _ **User Creation, Deletion and Password
Maintenance**_ " function, which makes it possible for an attacker to inject
Javascript code into the " ** _newUserName_** " parameter when creating a new
user.
This attack can be made unauthenticated due to the failure mentioned
[HERE](https://sku11army.blogspot.com/2020/01/symmetricom-syncserver_27.html)
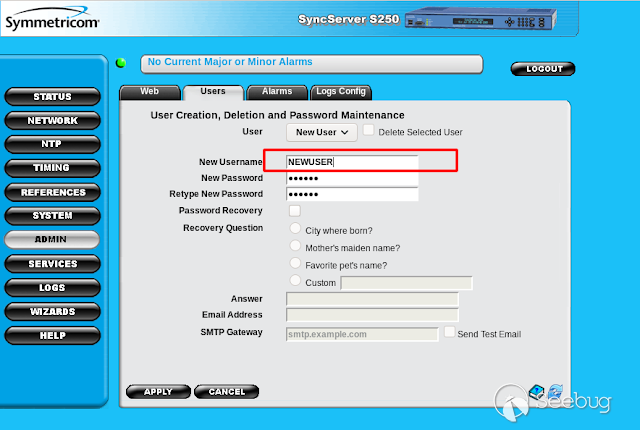
We go to the _**ADMIN Menu = > USERS => NEW USER**_. Once there, create any
user and capture the request.
[](https://images.seebug.org/1583459818933-w331s)
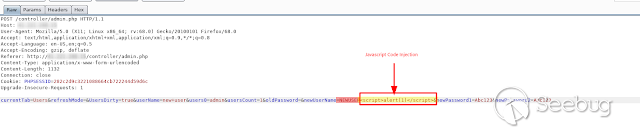
We modify the parameter " **newUserName** " and inject our payload, in this
case the classic " _ **< script> alert (1) </script>**_"
[](https://images.seebug.org/1583459824511-w331s)
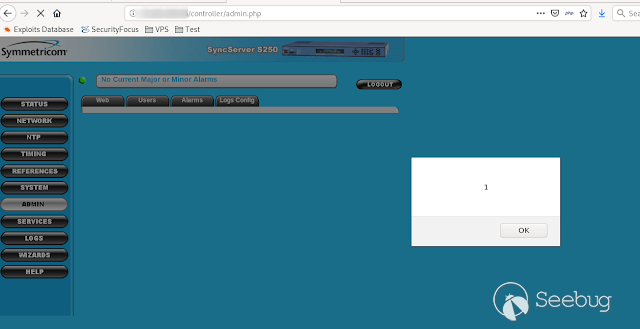
To see the execution, we enter the ADMIN menu again
[](https://images.seebug.org/1583459827909-w331s)
**Affected Versions:**
- **SyncServer S100 - ****2.90.70.3 Build 2.90.70.3 **
- ****SyncServer S200 - 1.** 30**
- **SyncServer S250** ** \- 1.25**
- **SyncServer S300 - ****2.65.0 Build 2.65.0 **
- **SyncServer S350 - 2.80.1 Build 2.80.1**
**
** CVE-2020-9028
**By: @Linuxmonr4**


暂无评论