## Summary
A physical attacker (or one with authorized-ADB access, e.g. PC malware) can change the ‘boot mode’ of a locked OnePlus 3/3T device, by rebooting into `fastboot` and issuing the `fastboot oem boot_mode {rf/wlan/ftm/normal}` command. The vulnerability may allow the attacker to elevate his privileges & exfiltrate modem-related information, in contradiction to the fact that locked bootloaders MUST NOT allow any security-sensitive operation to be run.
## Technical Details
Similarly to [CVE-2016-8467](/vulns/aleph-2016002) the attacker can change the boot mode of the device by issuing the `fastboot oem boot_mode {rf/wlan/ftm/normal}` command. For example:
```
> fastboot oem boot_mode wlan
...
OKAY
[ 0.034s] finished. total time: 0.036s
```
Beyond the intended functionalities of the special boot modes (which could be problematic on their own, however, we did not investigate them), such a boot mode change causes the bootloader to load the platform in an non-secure configuration – `adb` access is now available (without requiring host-authorization, albeit `userdata` is unmounted) together with `permissive`-mode SELinux. This can be seen by the output of the `getenforce` command:
```
> adb -d shell
OnePlus3:/ $ getenforce
Permissive
OnePlus3:/ $
```
With `permissive`-mode SELinux, the attacker could bypass security controls normally enforced by SELinux. For example, we’ve managed to change the USB configuration, so that sensitive USB interfaces are now enabled (e.g. the modem’s `diag` and `AT` interfaces):
```
OnePlus3:/ $ setprop sys.usb.config diag,acm_smd,acm_tty,rmnet_bam,mass_storage,adb
OnePlus3:/ $
```
The command above enables the following USB interfaces:
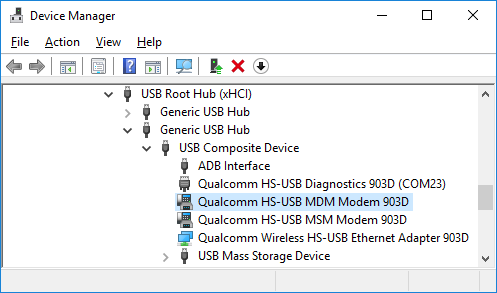
The `Qualcomm HS-USB MDM Modem` interface is the `AT` interface of the device’s modem:
```
ATI
Manufacturer: QUALCOMM INCORPORATED
Model: 4112
Revision: MPSS.TH.2.0.c1.9-00078-M8996FAAAANAZM-1.81324.1 1 [Dec 15 2016 20:00:00]
SVN: 01
IMEI: [...]
+GCAP: +CGSM
OK
```
The `Qualcomm HS-USB Diagnostics` interface is the modem’s diagnostics interface, and as explained thoroughly in the [Nexus 6/6P blog post](/2017/01/05/attacking-android-custom-bootmodes/), allows the attacker to modify modem-related configurations, and exfltrate sensitive information.
The vulnerability is rated with **Moderate** severity only (as opposed to **High** severity <span class="cve-high" title="Google Nexus 6/6P Custom Boot Modes USB Configs Override">[CVE-2016-8467](/vulns/aleph-2016002)</span>) because after the boot mode change, the platform does not continue with its normal boot process – it will perpetually display a notification to the user (although the victim may notice it too late, if at all):

It should be noted that \[CVE-2016-8467](/vulns/aleph-2016002)\ did not enable ADB nor set SELinux to `permissive` mode.
OxygenOS 4.1.0 has mitigated the issue by removing the `fastboot oem boot_mode` command from its bootloader:
```
> fastboot oem boot_mode
...
FAILED (remote: unknown command)
finished. total time: 0.023s
```
## Timeline
* 19-Mar-17 : Public disclosure.
* 16-Mar-17 : Patch available.
* 01-Mar-17 : Added as [ALEPH-2017005](/vulns/aleph-2017005)
* 29-Jan-17 : [CVE-2017-5623](https://alephsecurity.com/vulns/aleph-2017005) assigned.


暂无评论